Blogs
An Overview of DDoS Attacks: Understanding the Threat.
Posted by secureaccend on
May 6, 2024
0
Category: Blogs
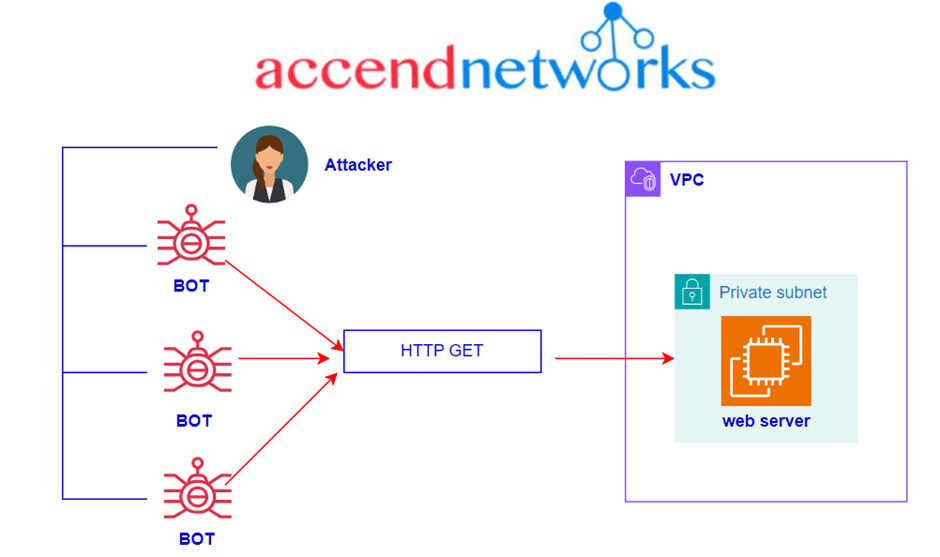
An Overview of DDoS Attacks: Understanding the Threat. In the current digital era, cybersecurity is key. Among the various threats that organizations face are Distributed Denial of Service (DDoS) attacks which are particularly disruptive. DDoS attack defence is one of the top security concerns on the web today, regardless of the attacker’s purpose, because disruption of availability can result in financial losses and other undesirable repercussions. In this blog article we will explore how AWS
Configure and restore an automatic AWS Backup job of an Amazon EC2 instance.
Posted by secureaccend on
May 6, 2024
Category: Blogs
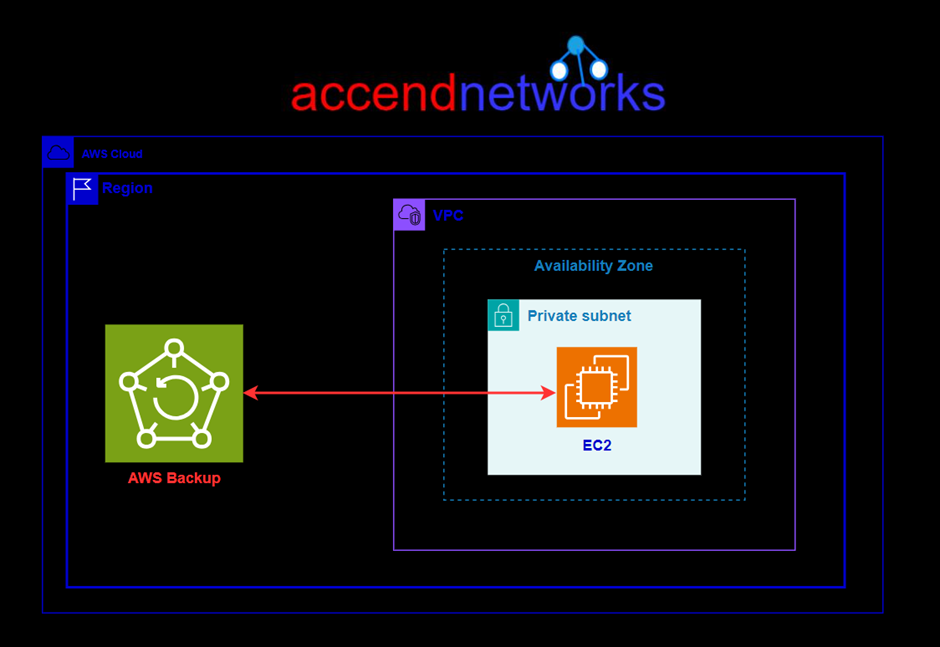
Configure and restore an automatic AWS Backup job of an Amazon EC2 instance. AWS Backup is a fully managed backup services that Centralises data protection across AWS services and on-premises enviroments. It simplifies the backup process by providing a unified interfaces to manage backups, retention policies , and recovery options. In this blog article, we will provide a demo of a backup and restore job on an AWS EC2 instance. Let’s proceed as follows. In
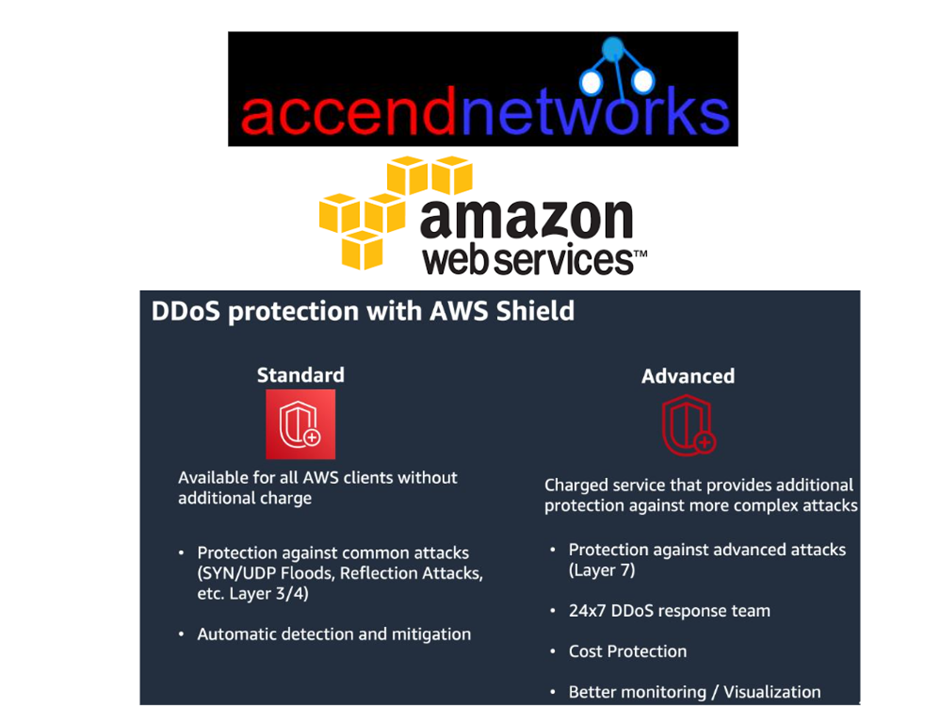
Protecting Applications with AWS Shield. DDoS (Distributed Denial of Service) attacks are still a big threat to online businesses. Attackers use millions of tonnes of traffic to bring down a victim’s web applications from multiple sources. What Is AWS Shield? AWS Shield is a managed solution for preventing DDoS attacks basically on AWS-hosted applications. It inspects traffic in real-time and applies mitigation strategies automatically in order to avoid performance degradation. Meanwhile, it inspects incoming requests
AWS Artufacts: Navigating compliance and security reports in aws
Posted by secureaccend on
May 6, 2024
Category: Blogs
AWS ARTIFACTS: NAVIGATING COMPLIANCE AND SECURITY REPORTS IN AWS. Amazon Web services has become a bedrock of cloud computing offering a plethora of services to cater for diverse business needs. Among its offerings are the AWS artifacts, a collection of compliance and security reports that provides valuable insights into the security and regulatory compliance of AWS services. What is AWS Artifact? AWS Artifacts is a centralized resource for accessing documentation related to AWS services’ security
How Amazon Macie Works Introduction As organizations grow, so do the volumes of sensitive data that need to be stored securely. Organizations must comply with the growing data privacy regulations and evolving guidance on protecting their sensitive data. This makes identifying and protecting sensitive data at scale complex, expensive and time consuming. Amazon Macie is a data security service to help you address these challenges. It discovers sensitive data using machine learning and pattern matching