Adding IPSec VPN as SD-WAN Member on FortiGate with Performance...
Read MoreAccend Networks San Francisco Bay Area Full Service IT Consulting Company
Blog
Effortless Job Processing with AWS Batch
Effortless Job Processing with AWS Batch: A Complete Guide to...
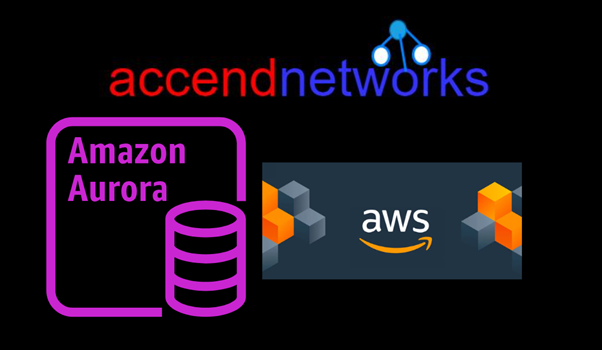
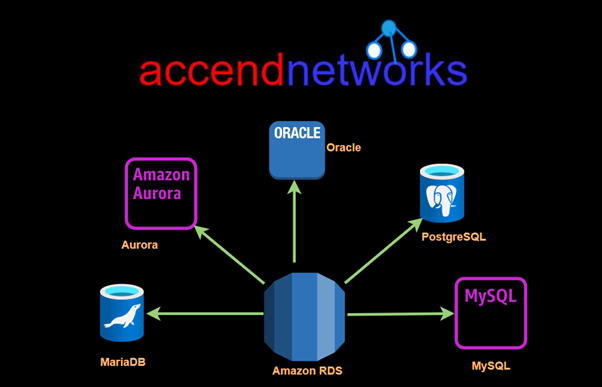
Read MoreUnlocking the Power of Amazon Aurora
Unlocking the Power of Amazon Aurora: A Comprehensive Guide to...
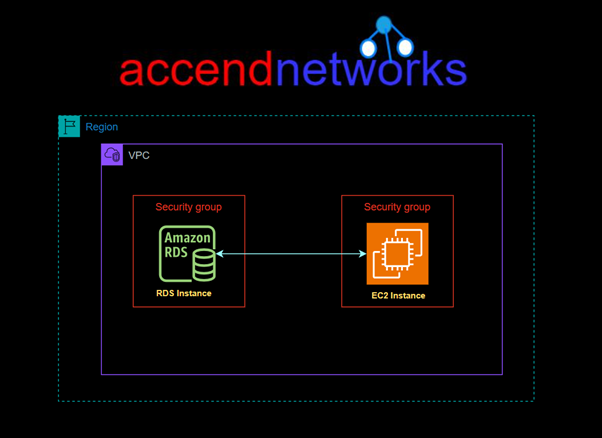
Read MoreHow to Set Up and Connect Amazon RDS with EC2: A Practical Guide
How to Set Up and Connect Amazon RDS with EC2:...
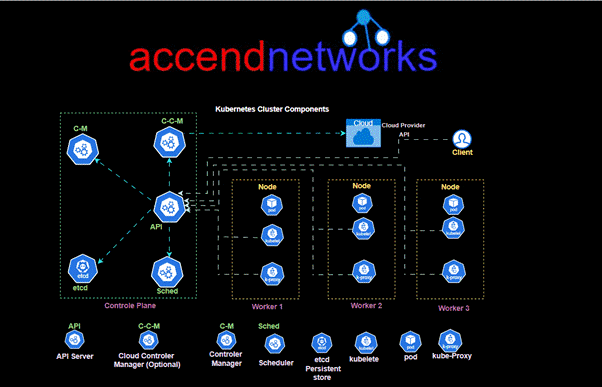
Read MoreUnderstanding Amazon EKS: Managed Kubernetes on AWS
Understanding Amazon EKS: An Overview of Managed Kubernetes on AWS...
Read MoreHow to Configure AWS CLI: A Step-by-Step Guide for Beginners
How to Configure AWS CLI: A Step-by-Step Guide for Beginners...
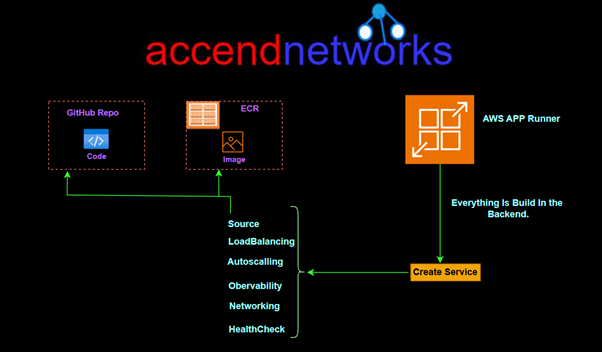
Read MoreHow AWS App Runner Simplifies Web App Management
Effortless Cloud Deployments: How AWS App Runner Simplifies Web App...
Read MoreBoost DynamoDB Performance with DynamoDB Accelerator (DAX): A Complete Guide
Boost DynamoDB Speed and Efficiency with DynamoDB Accelerator (DAX) Amazon...
Read MoreAWS Resource Access Manager
AWS Resource Access Manager (RAM) Explained: Securely Share Resources Across...
Read MoreUnderstanding Relational Database Service in AWS
Understanding Relational Database Service in AWS: A Comprehensive Guide Amazon...
Read MoreMigrating Data to Amazon Redshift
Migrating Data to Amazon Redshift: Best Practices for ETL Pipelines...
Read MoreMastering Amazon Elasticsearch
Mastering Amazon Elasticsearch (Amazon OpenSearch): A Comprehensive Overview Introduction Amazon...
Read MoreIntroduction to Amazon LightSail
Introduction to Amazon LightSail: Simplified Cloud Hosting for Your Projects...
Read MoreHow to Deploy a WordPress Site on Amazon LightSail
How to Deploy a WordPress Site on Amazon LightSail: A...
Read MoreGuide to AWS Public, Private, and Elastic IPs
Guide to AWS Public, Private, and Elastic IPs: Understanding AWS...
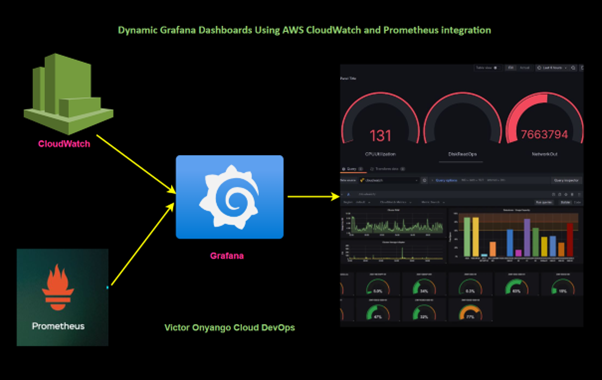
Read MoreDynamic Grafana Dashboards using AWS Cloudwatch
A Comprehensive Guide to Dynamic Grafana Dashboards Using AWS CloudWatch...
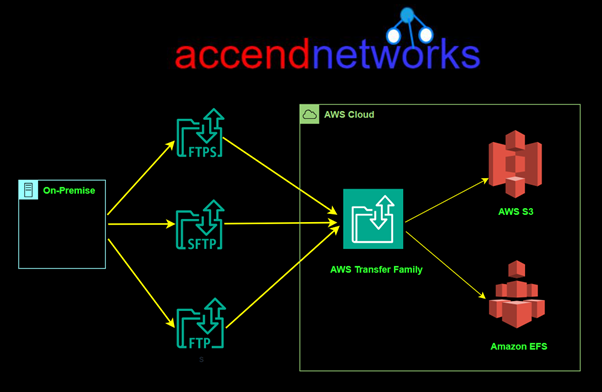
Read MoreAWS Transfer Family Overview
Introduction to AWS Transfer Family | Key Features & Benefits...
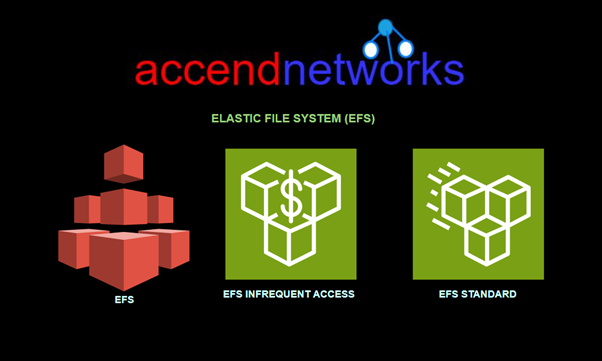
Read MoreAmazon Elastic File System
A Comprehensive Overview Amazon Elastic File System: Shared File Storage...
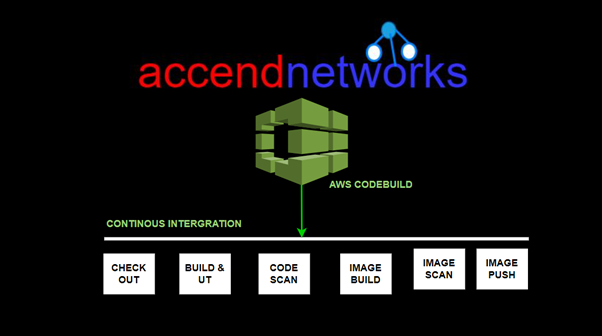
Read MoreComprehensive Guide to AWS Code Build
Comprehensive Guide to AWS Code Build: Features, Setup, and Best...
Read MoreControl and Optimize Cloud Expenses
Control and Optimize Cloud Expenses: Best Practices for Cost Management...
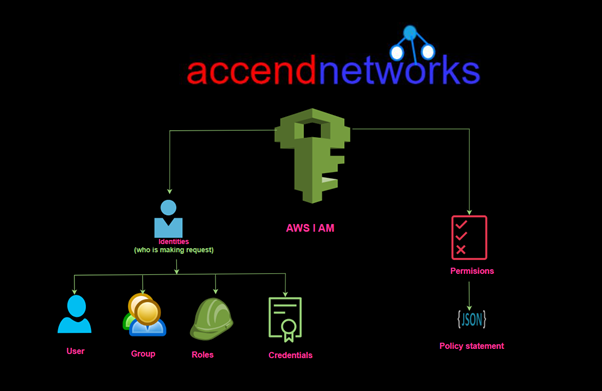
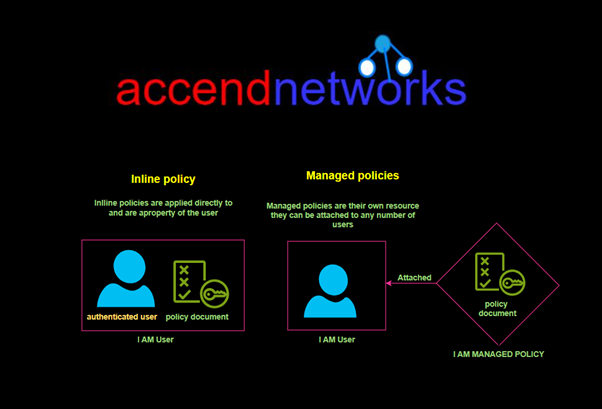
Read MoreExploring Managed and Inline Policies for Cloud Security
Exploring Managed and Inline Policies for Cloud Security: Hands-On Demo...
Read MoreOptimizing Cloud Expenses
Optimizing Cloud Expenses: Best Practices to Reduce Costs In today’s...
Read MoreMastering AWS Cost Monitoring
Mastering AWS Cost Monitoring: Essential Tools & Techniques Controlling and...
Read MoreLeveraging AWS Lambda for Efficient Stale
Automating Your Infrastructure: Leveraging AWS Lambda for Efficient Stale EBS...
Read MoreMinimizing Cross-Region Data Transfer Expenses in AWS
Minimizing Cross-Region Data Transfer Expenses in AWS: Cost-Saving Strategies Introduction...
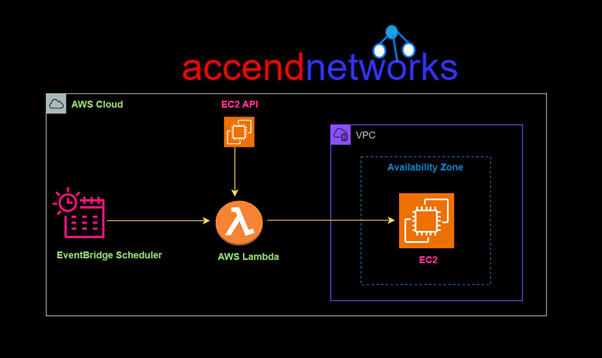
Read MoreEffortless Task Scheduling with Amazon Event Bridge Scheduler
Effortless Task Scheduling with Amazon Event Bridge Scheduler: Features and...
Read MoreUsing an Alias for Your AWS Account ID
Using an Alias for Your AWS Account ID AWS (Amazon...
Read MoreUnderstanding AWS Placement Groups
Understanding AWS Placement Groups: Maximizing Performance and Reliability in EC2...
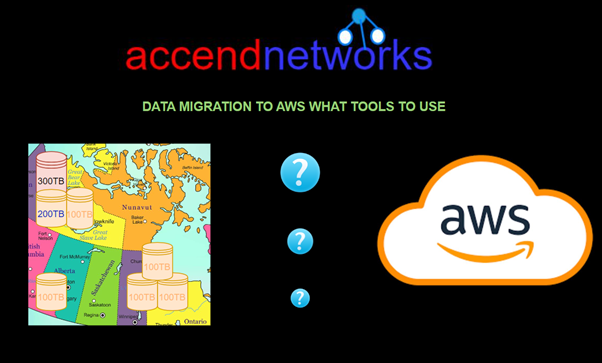
Read MoreExploring AWS Data Migration Services
Exploring AWS Data Migration Solutions: Unlocking Seamless Cloud Transitions Migrating...
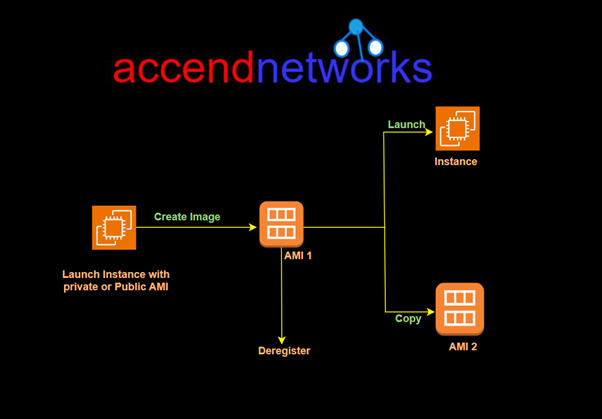
Read MoreUnderstanding AMI in AWS
Understanding AMI in AWS: A definitive guide to cloud resilience...
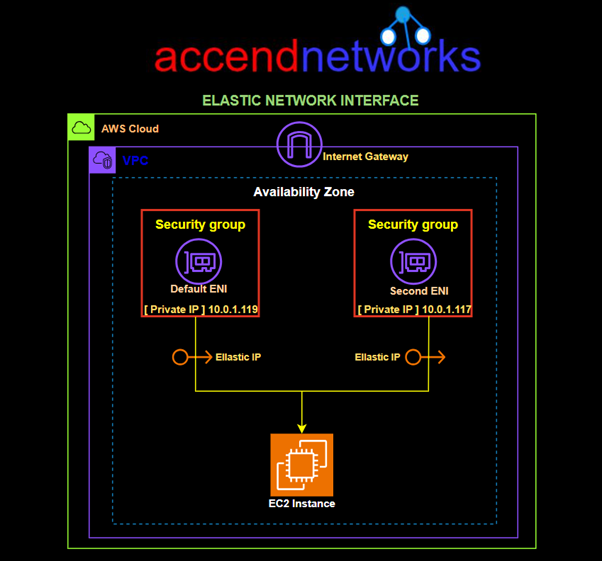
Read MoreAWS Elastic Network Interface
Understanding AWS Elastic Network Interface (ENI) In the AWS environment,...
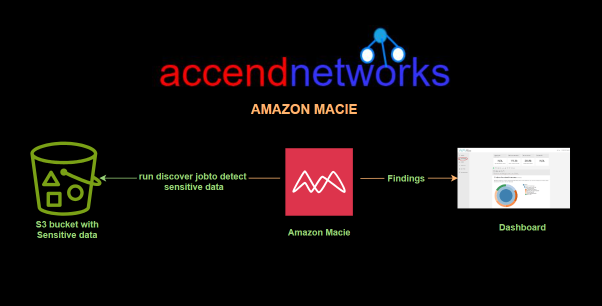
Read MoreProtecting Sensitive Data with AWS Macie
Protecting Sensitive Data in AWS: A Practical Demo with AWS...
Read MoreScaling Big Data with Amazon Redshift
Scaling Big Data with Amazon Redshift: Insights into Managing Large...
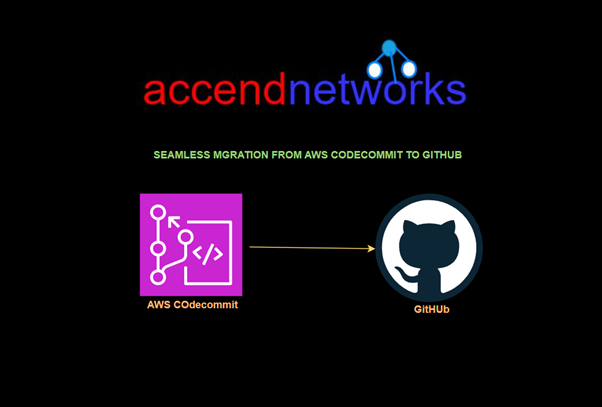
Read MoreAWS Code Commit Obsolete
AWS CodeCommit Obsolete: Transitioning from AWS CodeCommit and Steps for...
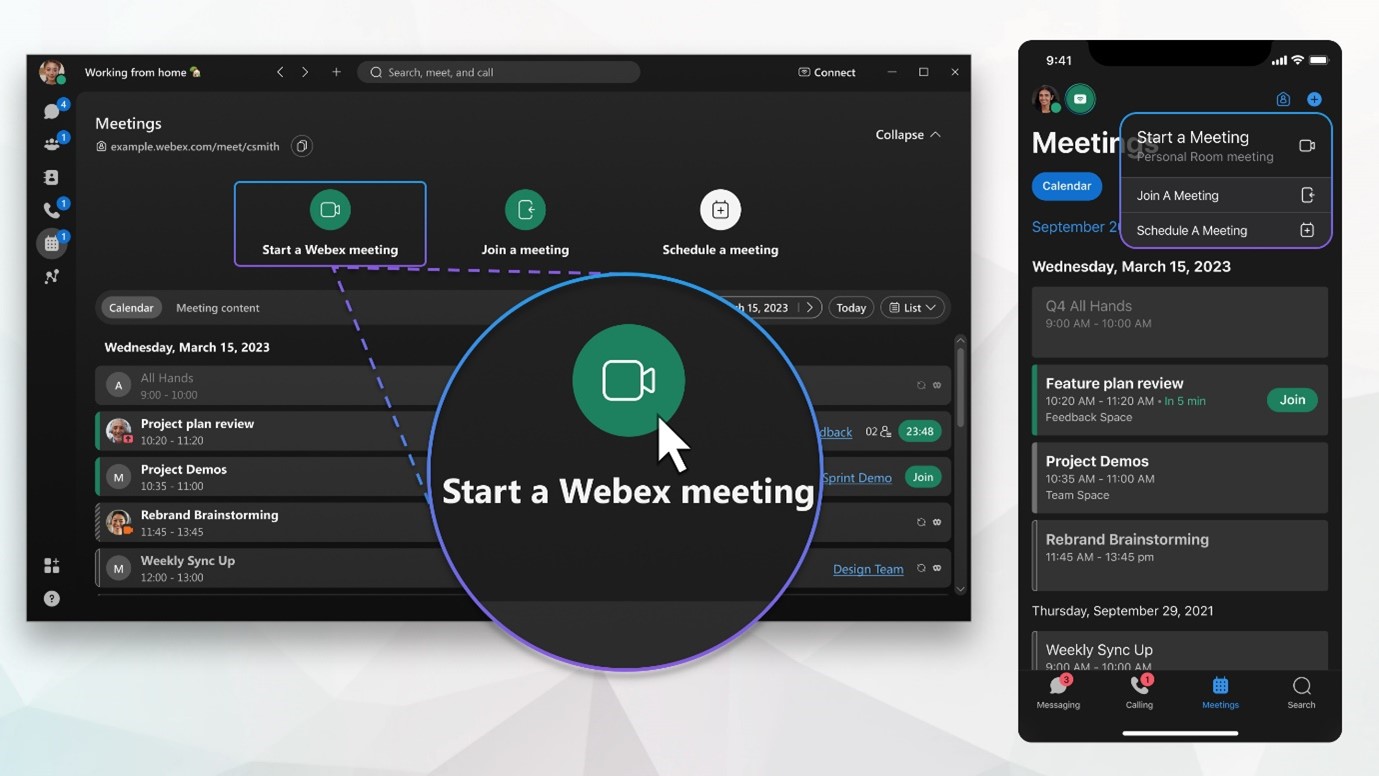
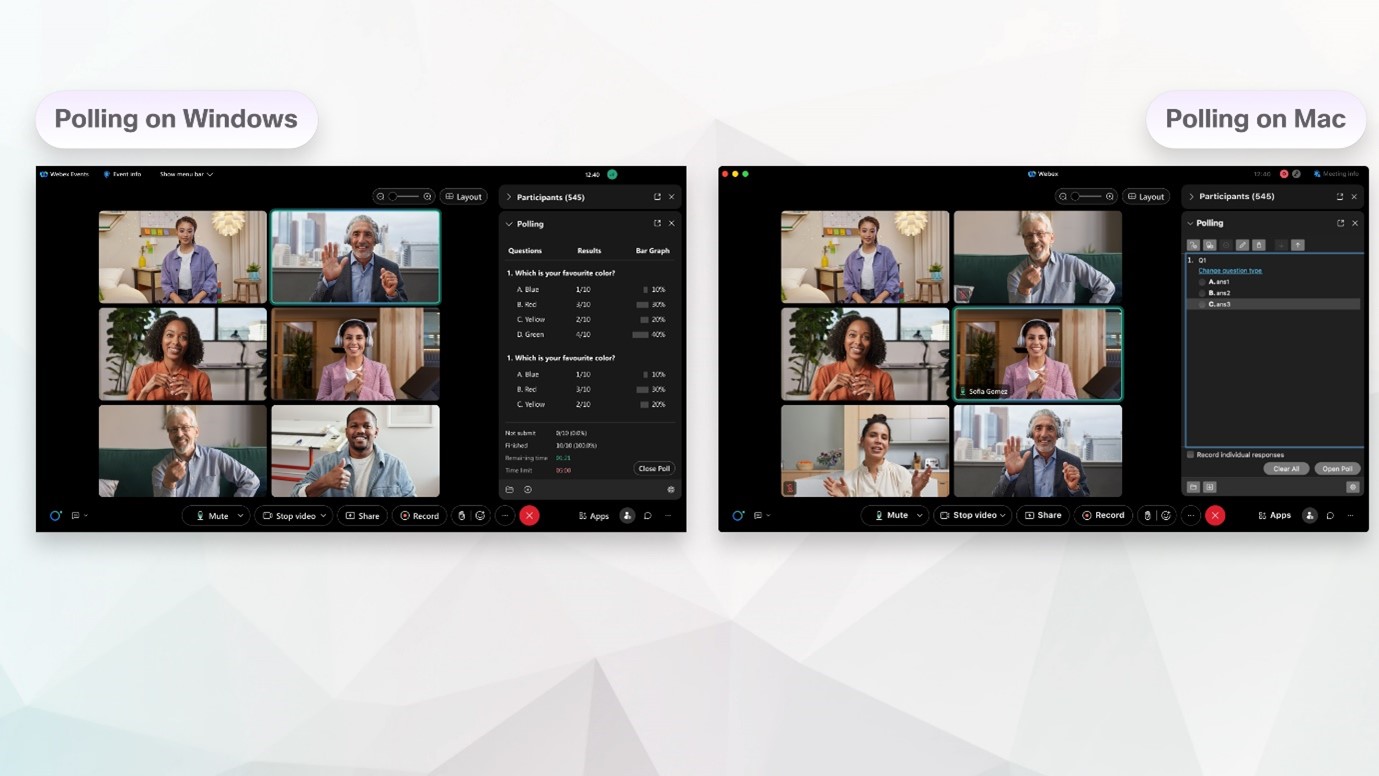
Read MoreDifferent Types of The WebEx Meetings
What are the different types of the WebEx meetings There...
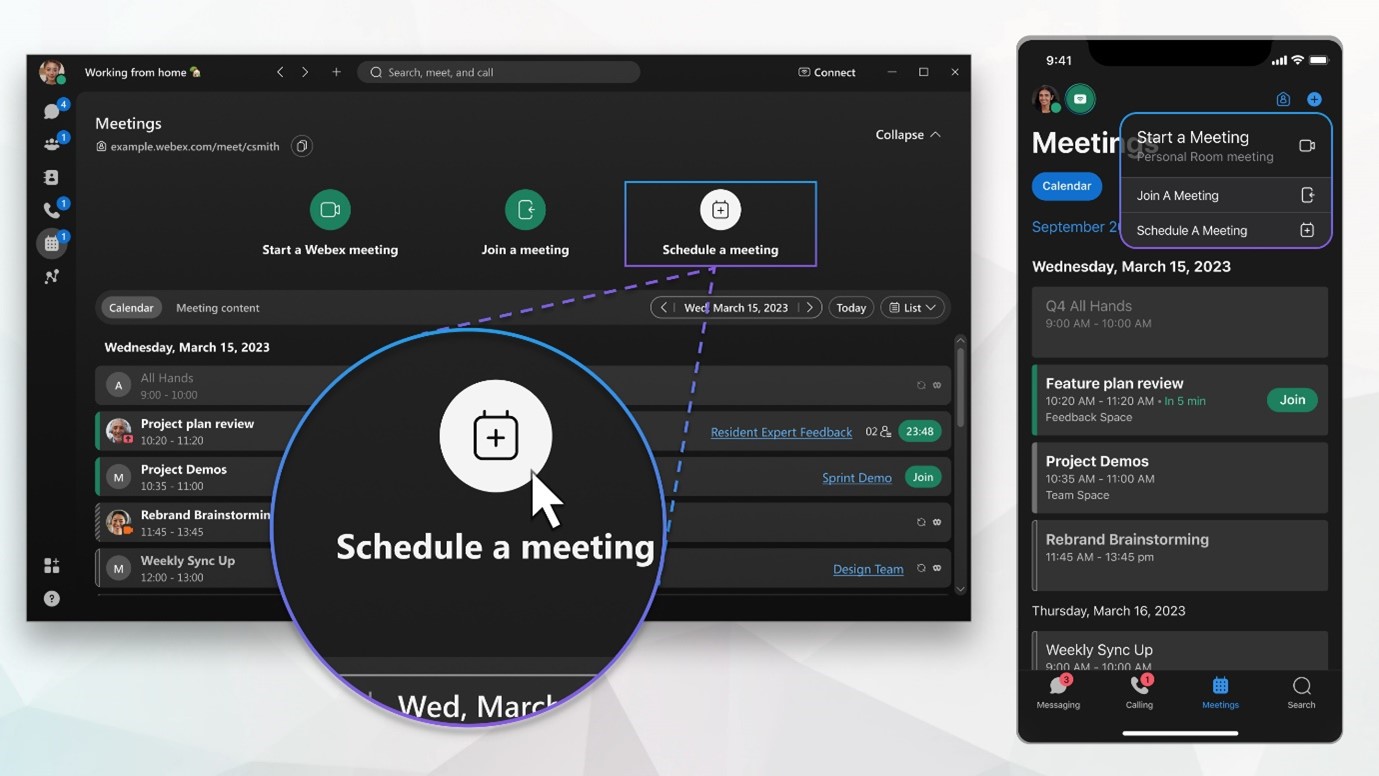
Read MoreSetting Up the Scheduled Meeting
Setting up the Scheduled Meeting (Normal Meeting) Schedule a meeting...
Read MoreConnect to meeting audio and do content sharing
How to Connect to Meeting Audio and Do Content Sharing...
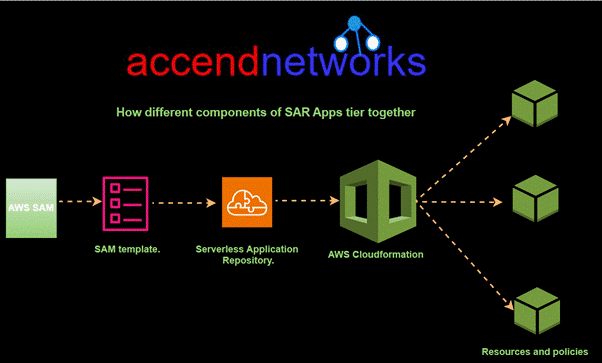
Read MoreAWS Serverless Application
AWS Serverless Application Repository an Overview Serverless application repository allows...
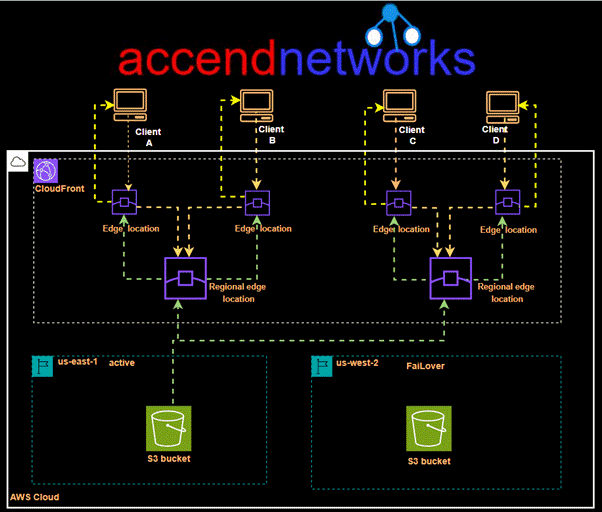
Read MoreDeep Dive into CloudFront
Deep Dive into CloudFront: Understanding Internal Caching Mechanisms and Implementing...
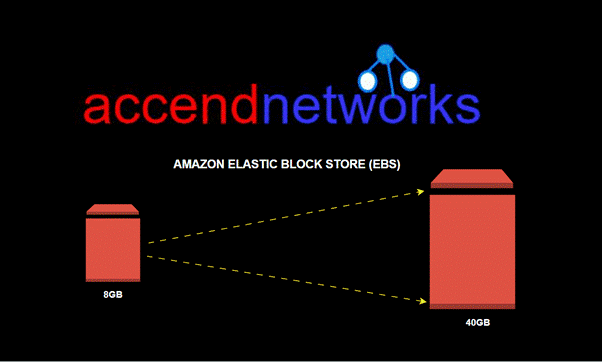
Read MoreExpand Your EC2 Storage
Effortlessly Expand Your EC2 Storage: Increasing EBS Volume Size Amazon...
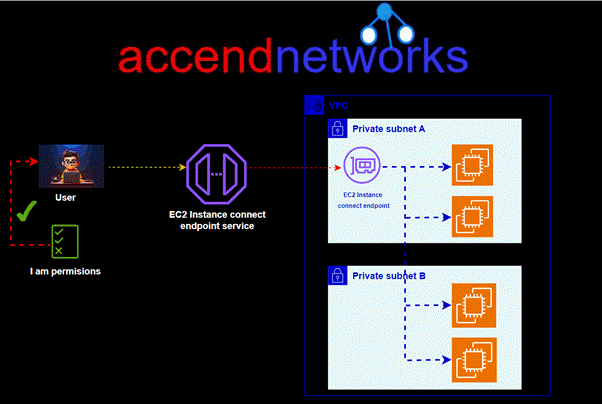
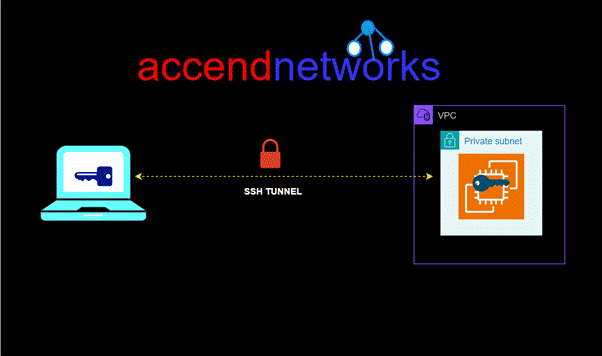
Read MoreEC2 Instance Connect Endpoint
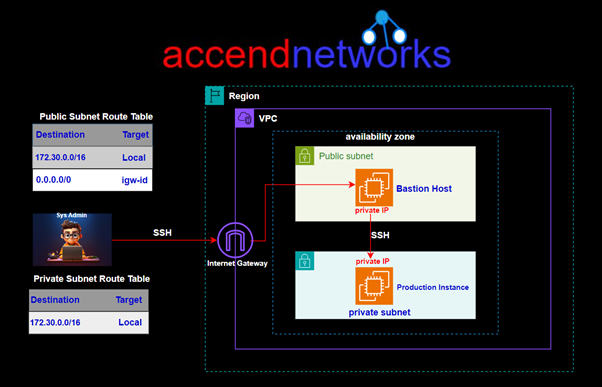
EC2 Instance Connect Endpoint: Secure Access to Private Subnet Instances...
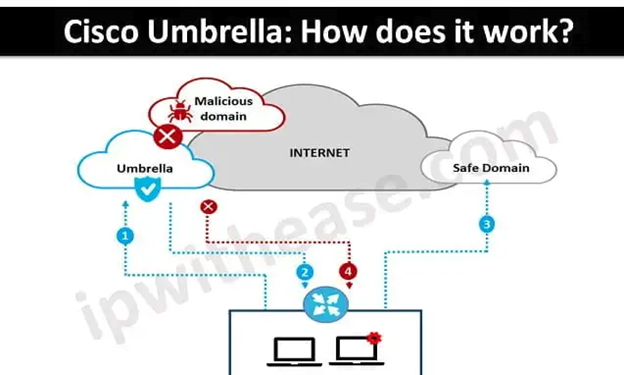
Read MoreCisco Umbrella Monitoring
Cisco Umbrella Monitoring and Logging Best Practices How to: Validate...
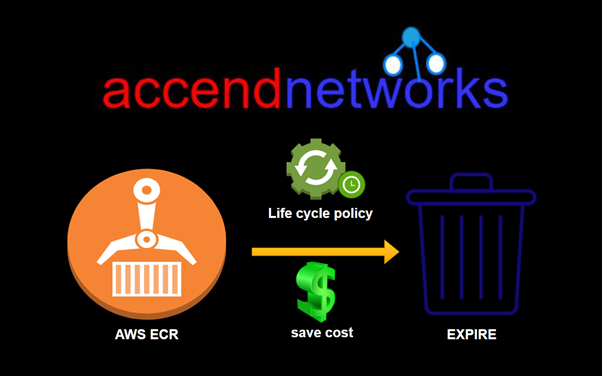
Read MoreOptimizing ECR Costs
Optimizing AWS ECR Costs: Effective Use of Lifecycle Policies Amazon...
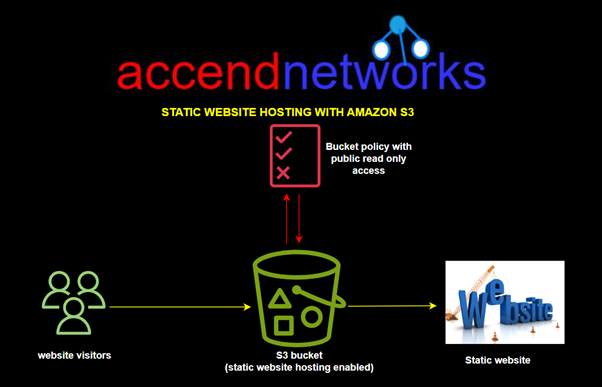
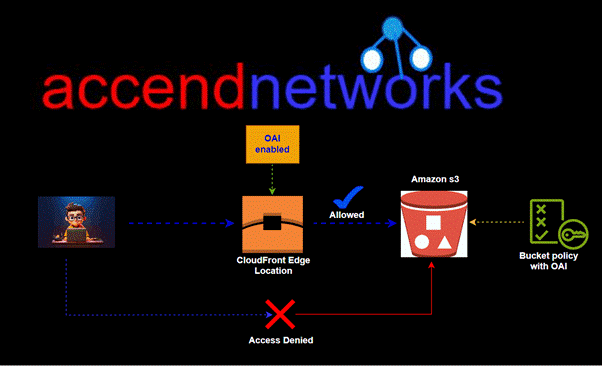
Read MoreSecuring S3 Buckets
Securing Your S3 Buckets: Preventing Unauthorized Access with CloudFront OAI...
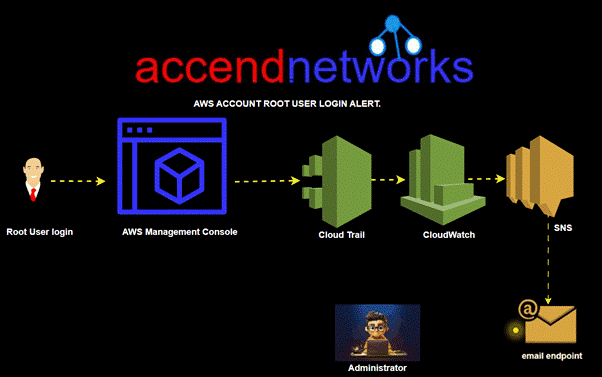
Read MoreEnhancing AWS Security
Enhancing AWS Security: Implementing Root Account Login Alerts When it...
Read MoreAzure Roles and RBAC Privilege Identity Management
Using Azure Roles and RBAC Privilege Identity Management (PIM) In...
Read MoreCisco Secure Email
Email Notifications Get email notifications on critical security issues; system...
Read MoreAWS Key Management Service Part One
Unlocking the Power of AWS Key Management Service (KMS) Part...
Read MoreSecure Uploads and Downloads in S3
Secure File Uploads and Downloads in S3 Using Presigned URLs...
Read MoreAWS Key Management Service (KMS) Part Two
Unlocking the Power of AWS Key Management Service (KMS) Part...
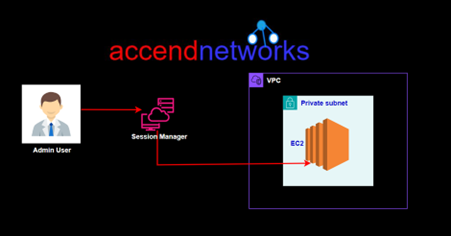
Read MoreAWS Systems Manager
Unveiling the Power of AWS Systems Manager: Simplifying Management and...
Read MoreAutomate Your EBS Backups
Automate Your EBS Backups: A Comprehensive Guide to Scheduled Snapshots...
Read MoreIntroduction to Azure Blob Storage
Introduction to Azure Blob Storage Azure Blob Storage is part...
Read MoreSlash AWS Expenses
Slash AWS Expenses: Automate EC2 Idle Instance Shutdown with CloudWatch...
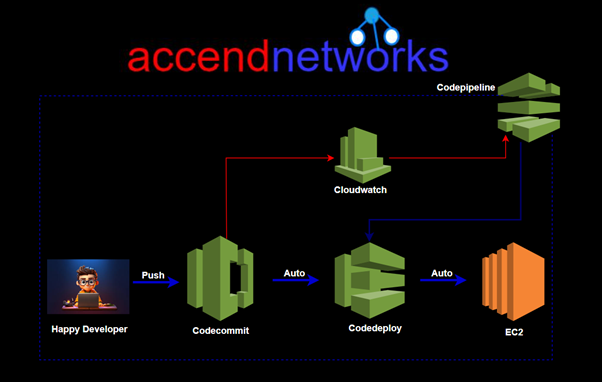
Read MoreAWS CodeCommit: Streamlining Source Control in the Cloud.
What is AWS CodeCommit? Streamlining Source Control in the Cloud....
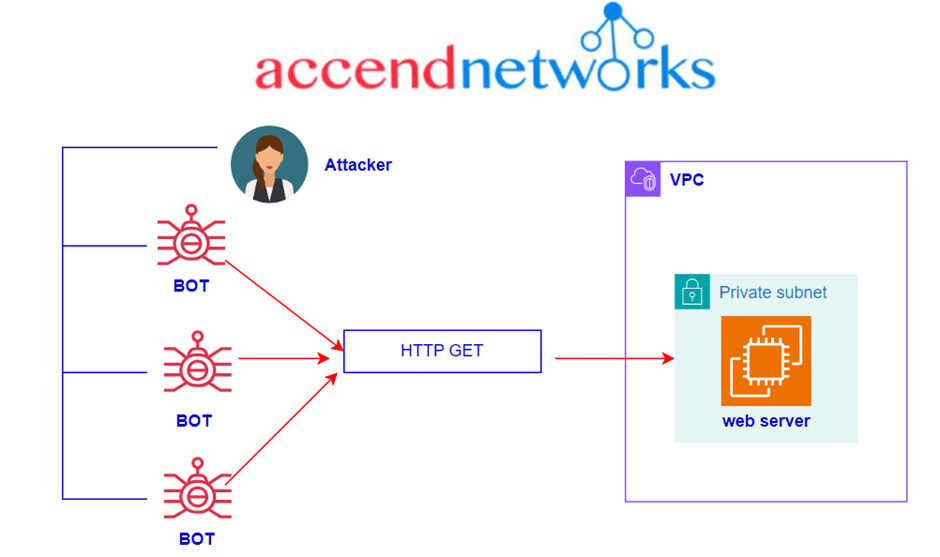
Read MoreAn Overview of DDoS Attacks: Understanding the Threat.
An Overview of DDoS Attacks: Understanding the Threat. In the...
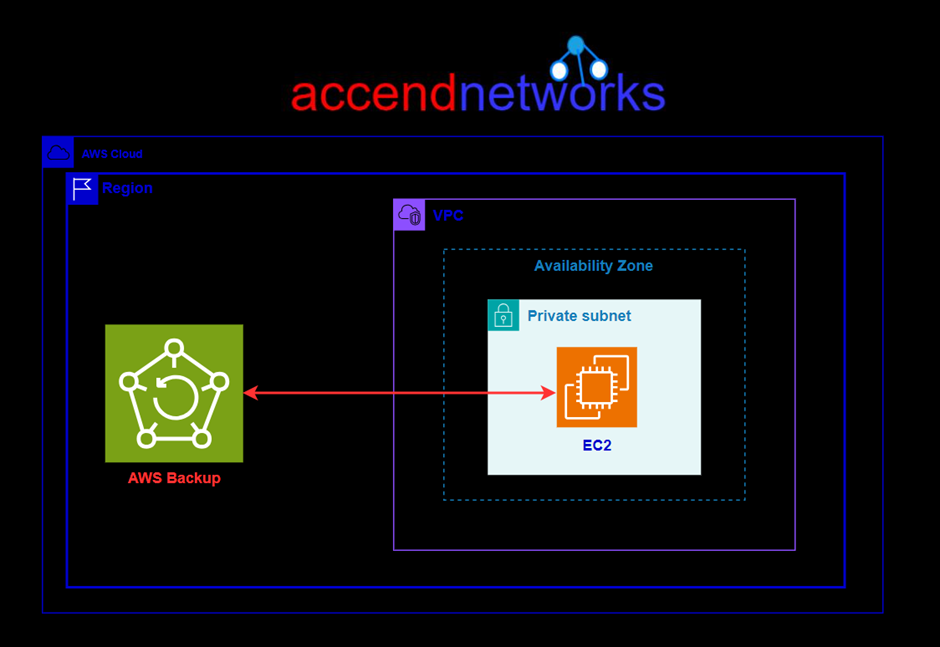
Read MoreAWS Backup an Amazon EC2 instance
Configure and restore an automatic AWS Backup job of an...
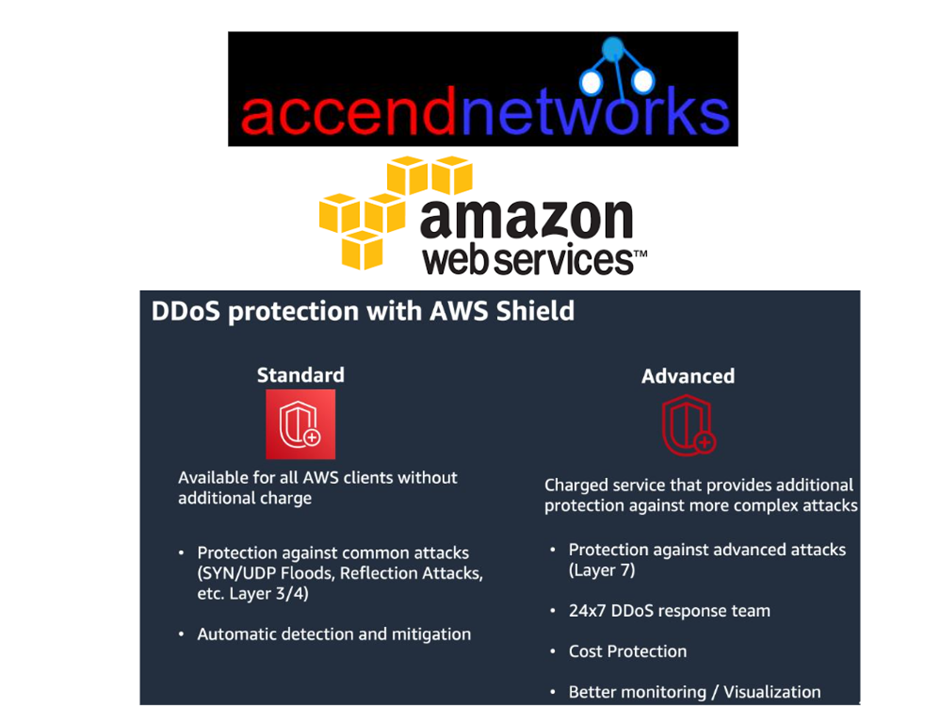
Read MoreProtecting Applications with AWS Shield
Protecting Applications with AWS Shield. DDoS (Distributed Denial of Service)...
Read MoreWhat is AWS artifact
AWS ARTIFACTS: NAVIGATING COMPLIANCE AND SECURITY REPORTS IN AWS. Amazon...
Read MoreAmazon Inspector: Automated and continual vulnerability management at scale
How To Use Amazon Inspector: an automated and continual vulnerability...
Read MoreHow To Monitor AWS API Activity with AWS CloudTrail
Monitoring AWS API Activity with AWS CloudTrail AWS CloudTrail is...
Read MoreBenefits of Using AWS Secrets Manager Part One
Safeguarding Your Secrets: The Importance of Using AWS Secrets Manager...
Read MoreHow to Store Secrets with Secrets Manager – Part II
How to Store Secrets with Secrets Manager – Part II...
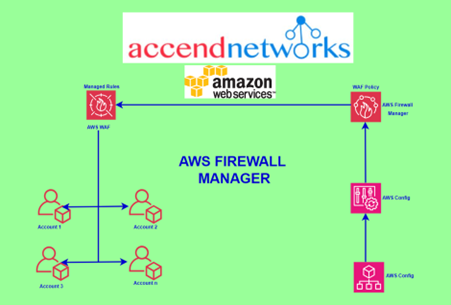
Read MoreHow To Filter Traffic with AWS Web Application Firewall – Part One
Filtering Traffic with AWS Web Application Firewall part one. What’s...
Read MoreFiltering Traffic with AWS Web Application Firewall Part Two
Filtering Traffic with AWS Web Application Firewall Part Two. A...
Read MoreHow To Create Serverless Computing with AWS Lambda
How To Create Serverless Computing with AWS Lambda. In the...
Read MoreFind Out What Decoupling Workflows in AWS Is
Find Out What Decoupling Workflows in AWS Is Decoupling workflows...
Read MoreHow To Create AWS Certificate Manager
AWS CERTIFICATE MANAGER The world of digital security is complex...
Read MoreHow To Create AWS SQS Sending Messages
How To Create AWS SQS Sending Messages. In the dynamic...
Read MoreAmazon Elastic Container Service (ECS)
Amazon Elastic Container Service (ECS) Introduction: In the ever-evolving landscape...
Read MoreHow To Create Application Load Balancers in AWS
How To Configure Application Load Balancers in AWS What is...
Read MoreHow To Configure AWS Transit Gateway
How To Configure AWS Transit Gateway The network architecture in...
Read MoreHow To Create AWS EC2 Auto Scaling
How To Configure AWS EC2 Auto Scaling Amazon Web Services...
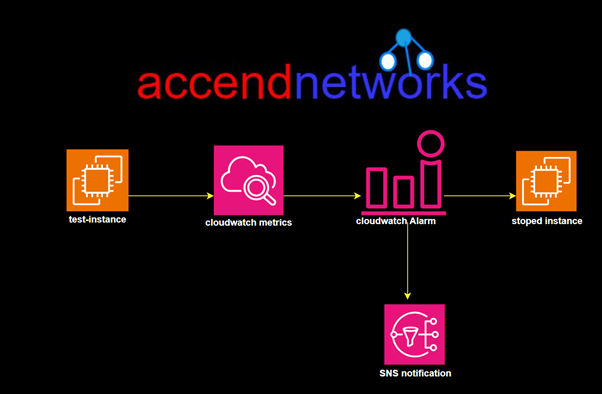
Read MoreHow Does Amazon CloudWatch Work?
How Does Amazon CloudWatch Work? Amazon CloudWatch monitors your Amazon...
Read MoreHow To Create with Network Load Balancer in AWS
Extreme Performance with Network Load Balancers In today’s fast-paced digital...
Read MoreHow To Configure Serverless Computing
How To Configure Serverless Computing.. Serverless computing has emerged as...
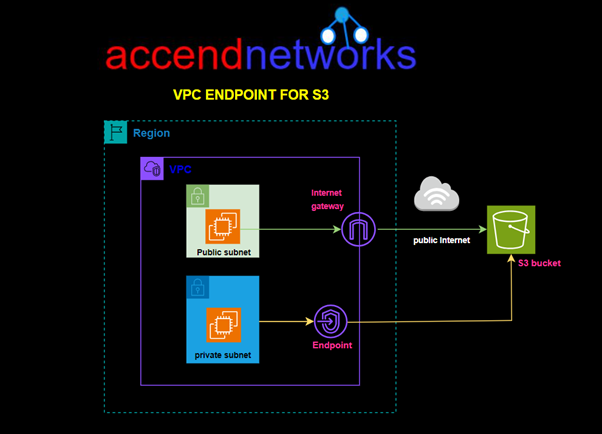
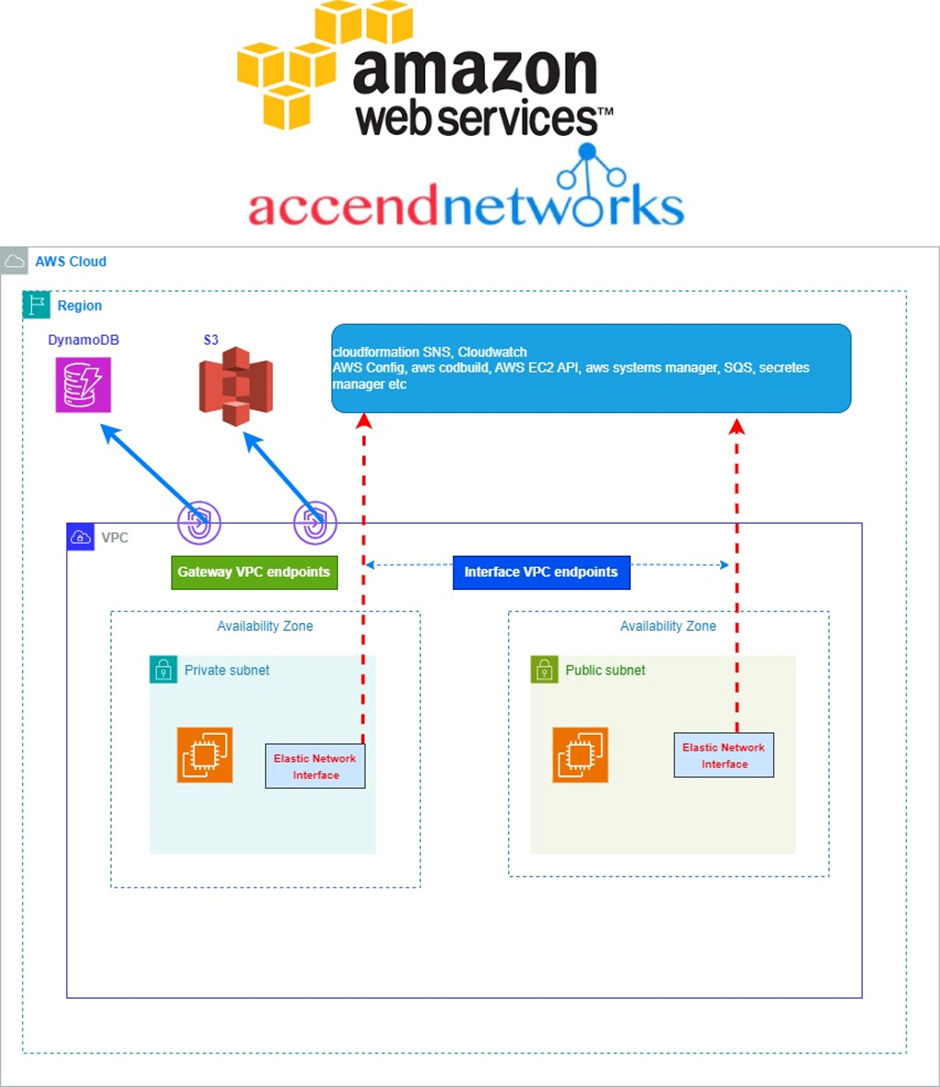
Read MoreHow to Configure VPC Endpoints to Enhance Security and Efficiency in Cloud Networking.
How to Configure VPC Endpoints to Enhance Security and Efficiency...
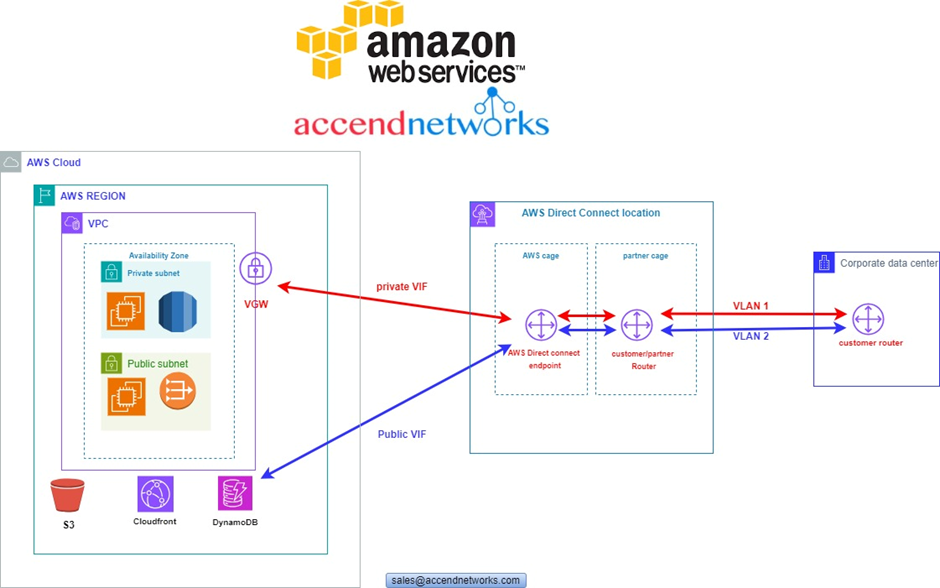
Read MoreExploring the Power of AWS Direct Connect: Bridging the Gap Between On-Premises and the Cloud.
Exploring the Power of AWS Direct Connect: Bridging the Gap...
Read MoreHow to Configure A Dual-NAT Gateway
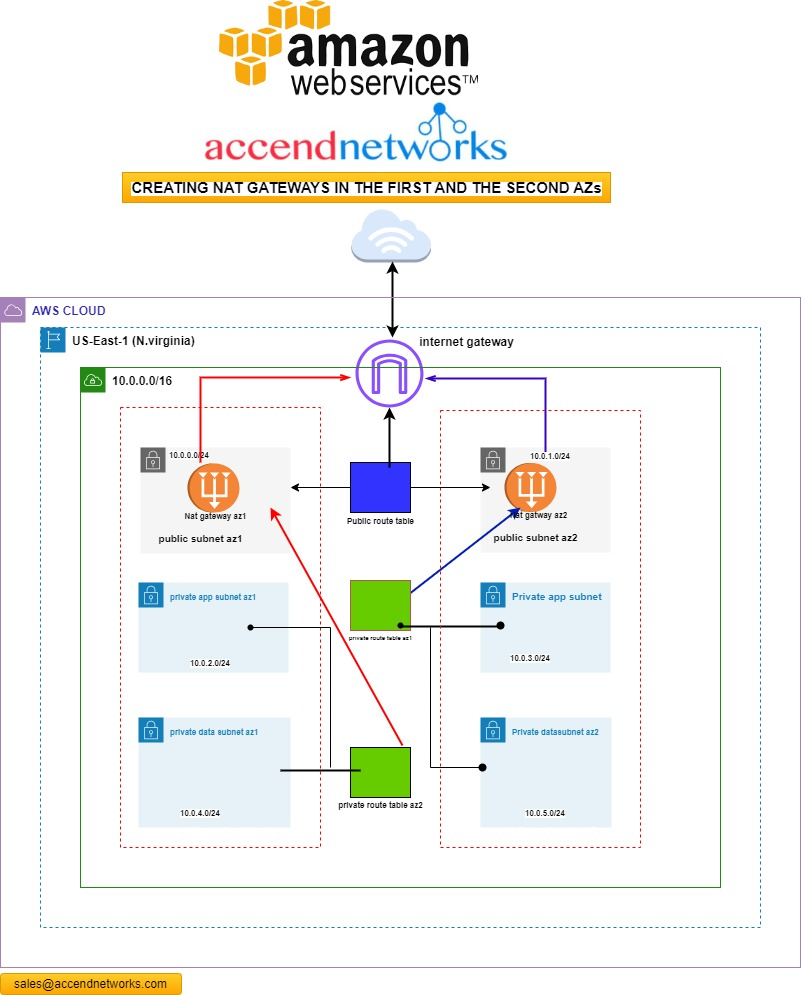
HOW TO CONFIGURE A DUAL-NAT GATEWAY IN TWO DIFFERENT AVAILABILITY...
Read MoreVpc Part Two: Building A Custom 3-tier Vpc From Scratch
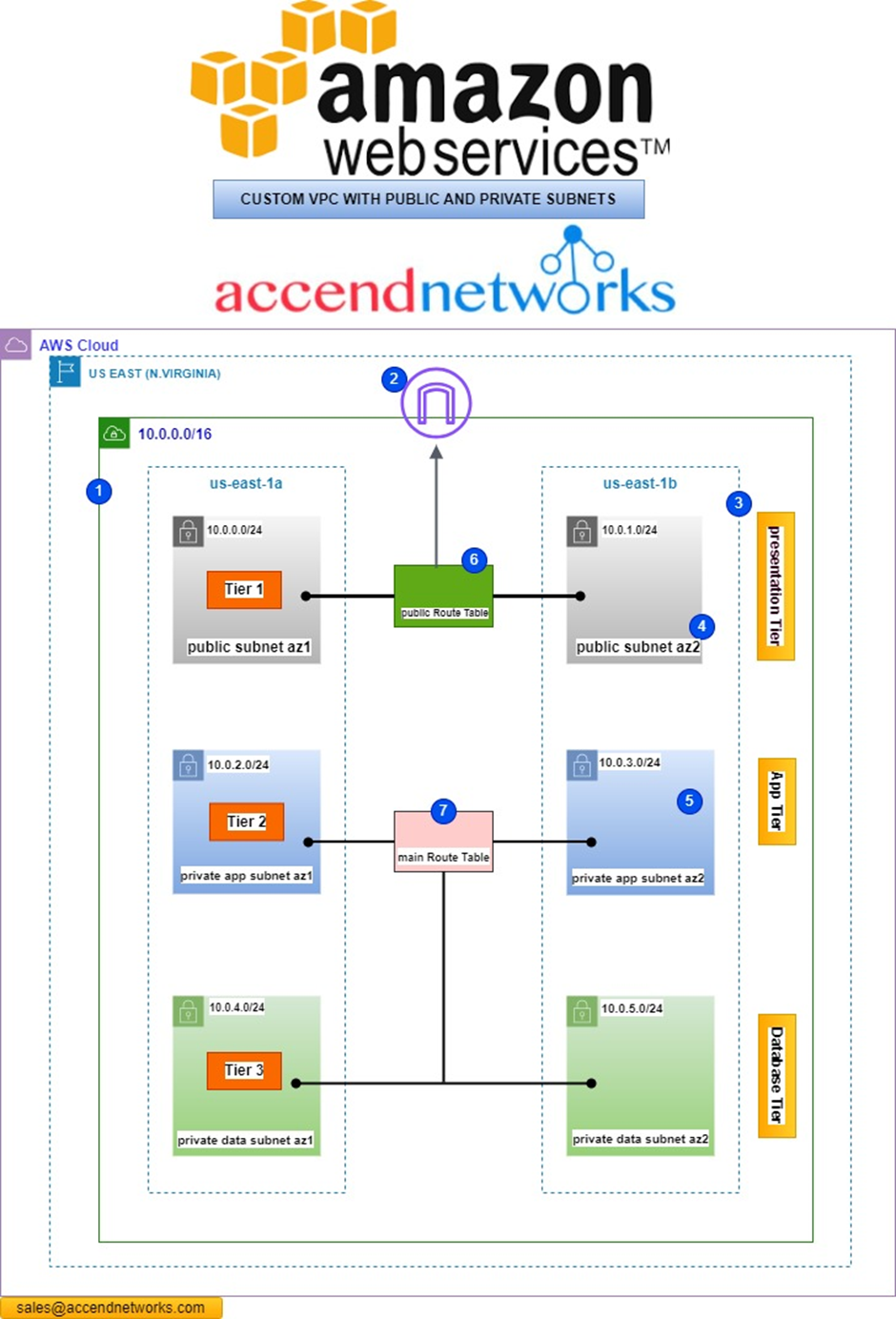
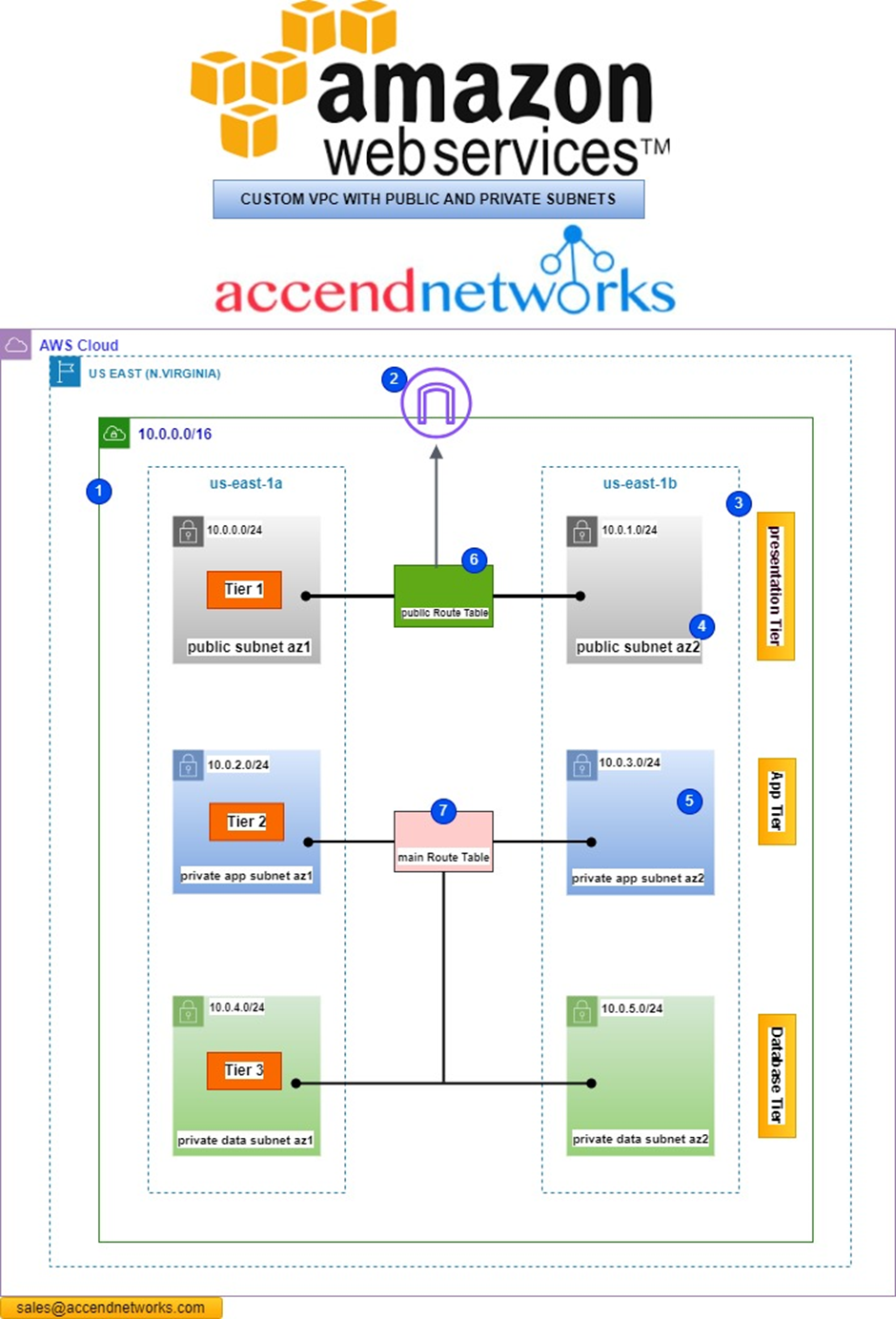
VPC PART TWO: BUILDING A CUSTOM 3-TIER VPC FROM SCRATCH...
Read MoreUnderstanding AWS ACL (Access Control Lists): Controlling Subnet Traffic
Understanding AWS ACL (Access Control Lists): Controlling Subnet Traffic Network...
Read MoreVpc Part Two: Building A Custom 3-tier Vpc From Scratch.
VPC PART TWO: BUILDING A CUSTOM 3-TIER VPC FROM SCRATCH....
Read MoreVirtual Private Cloud (VPC) Overview: Empowering Secure and Scalable Cloud Networks Part 1
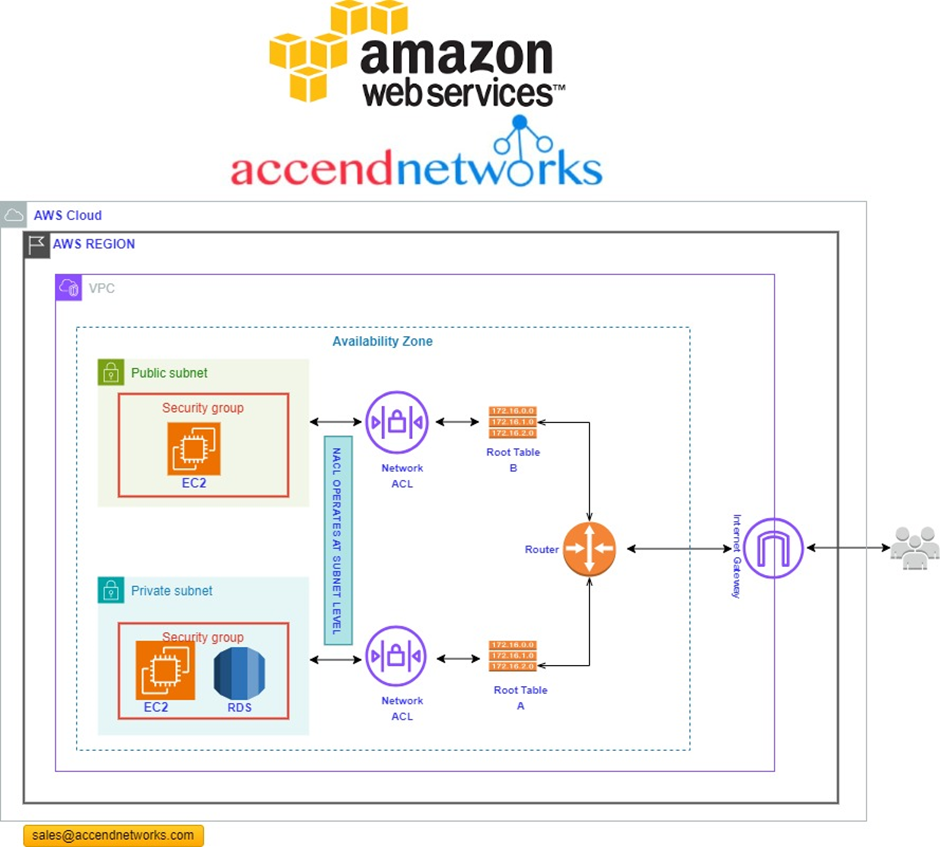
Virtual Private Cloud (VPC) Overview: Empowering Secure and Scalable Cloud...
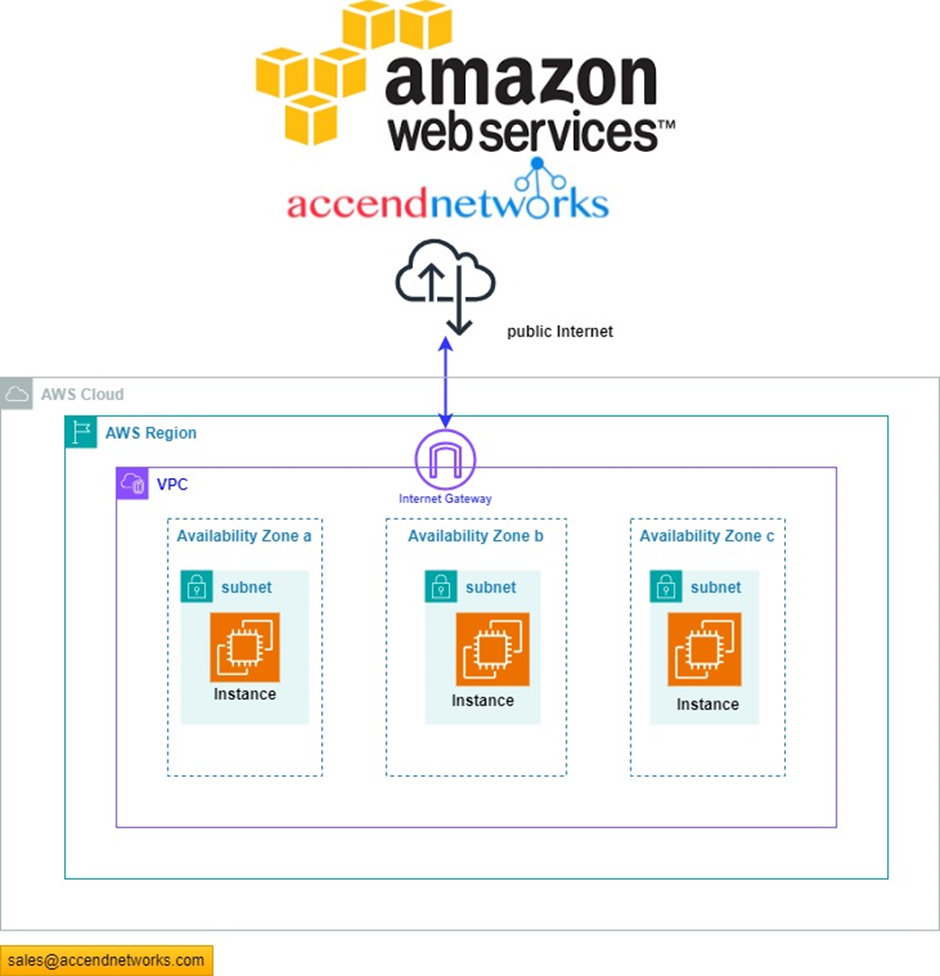
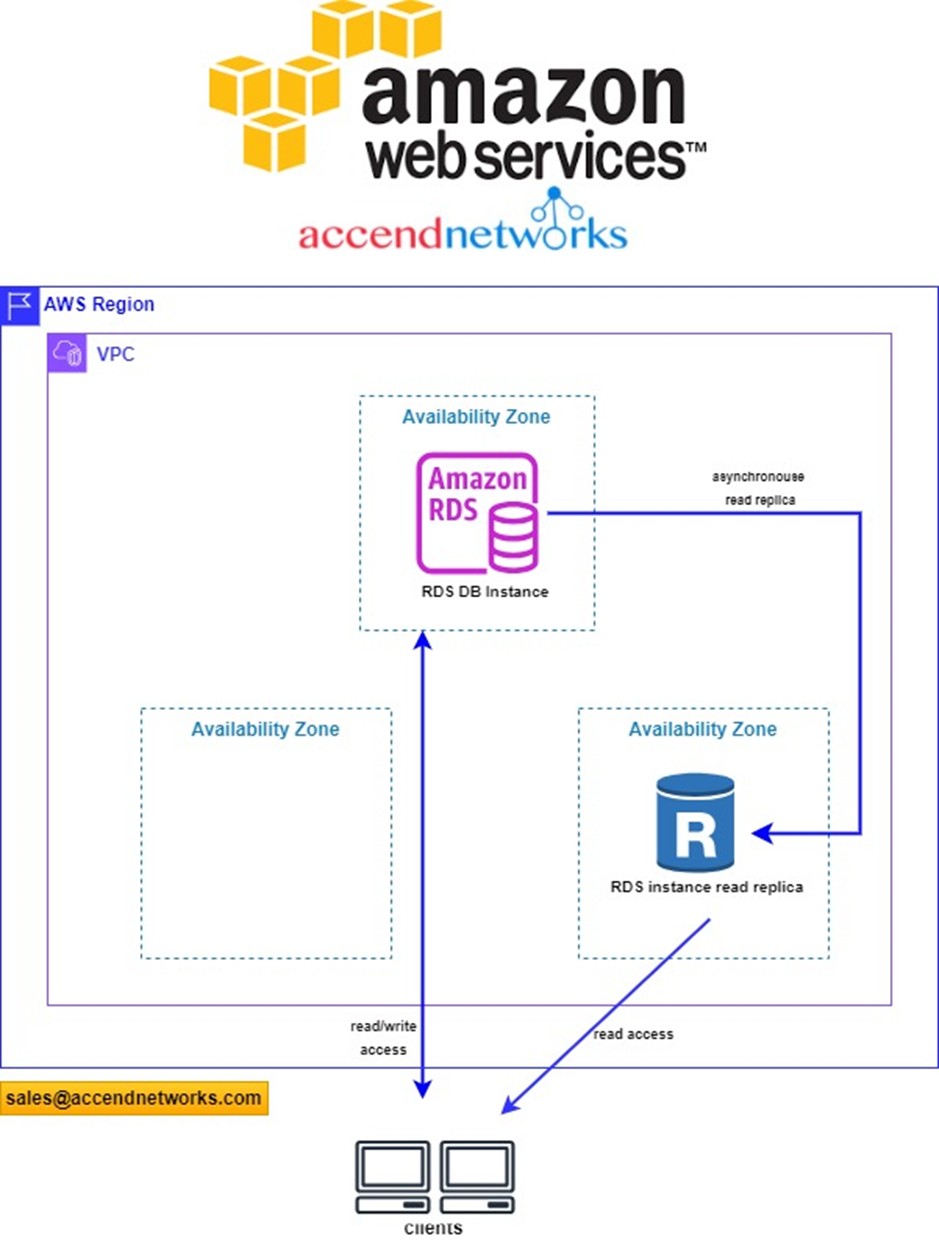
Read MoreBoosting Performance: The Power of Read Replicas in Database Management.
Boosting Performance: The Power of Read Replicas in Database Management....
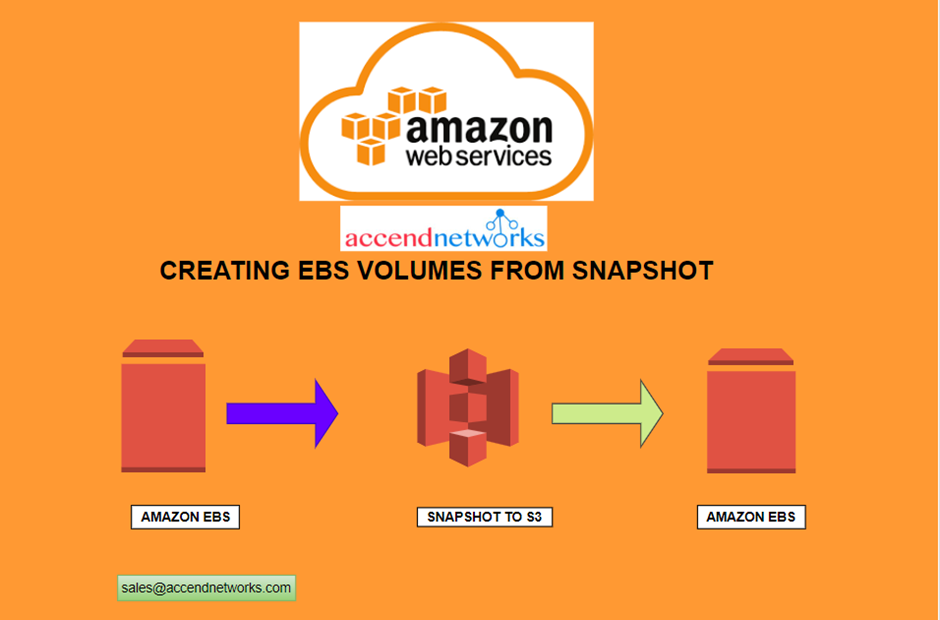
Read MoreCREATING EBS VOLUME FROM SNAPSHOTS AND TRANSFER OF SNAPSHOTS BETWEEN REGIONS.
Creating EBS Volume From Snapshots And Transfer Of Snapshots Between...
Read MoreDeployment of SDDC using VMware Cloud on AWS Services
Deployment of SDDC using VMware Cloud on AWS Services VMware...
Read MoreUnlocking the Power of AWS EBS Volumes: A Comprehensive Introduction
Unlocking the Power of AWS EBS Volumes: A Comprehensive Introduction....
Read MoreUnderstanding AWS Security Groups and Bootstrap Scripts
Understanding AWS Security Groups and Bootstrap Scripts: Enhancing Cloud Security...
Read MoreLeveraging AWS IAM Roles for Secure and Efficient Cloud Resource Management
Leveraging AWS IAM Roles for Secure and Efficient Cloud Resource...
Read MoreTurbocharge Your Amazon S3: Performance Enhancement Guidelines.
Turbocharge Your Amazon S3: Performance Enhancement Guidelines. INTRODUCTION Amazon S3,...
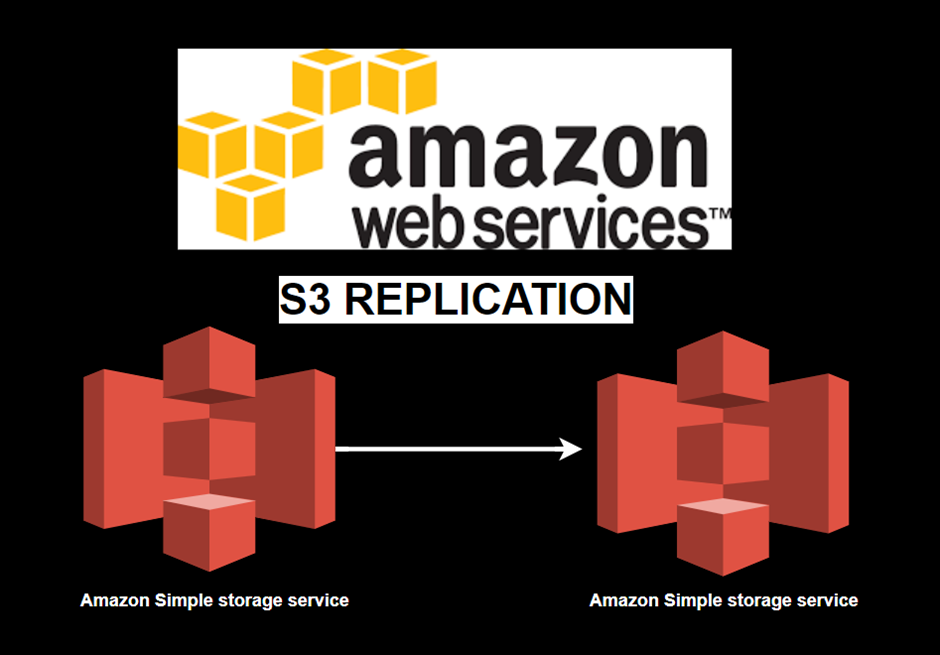
Read MoreMastering Data Redundancy: Amazon S3 Replication Demystified.
Mastering Data Redundancy: Amazon S3 Replication Demystified. In today’s data-driven...
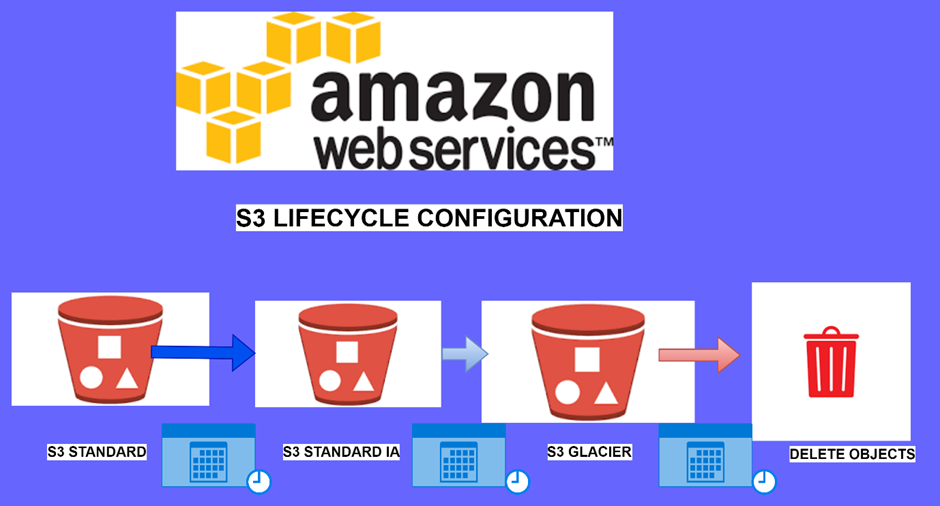
Read MoreMaximizing Efficiency and Cost Savings with AWS S3 Lifecycle Management
Maximizing Efficiency and Cost Savings with AWS S3 Lifecycle Management...
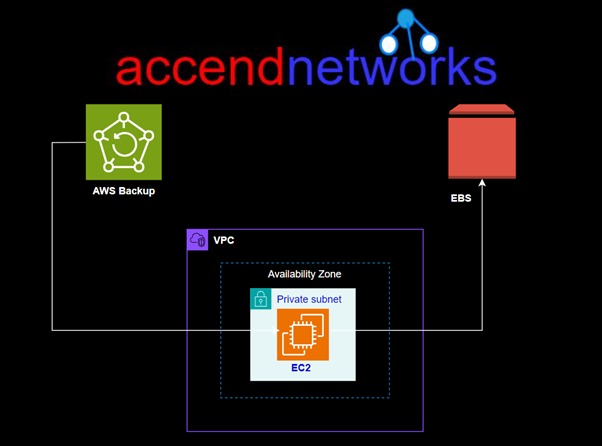
Read MoreMastering Data Protection: AWS Backup.
Mastering Data Protection: AWS Backup. In the ever-evolving digital landscape,...
Read MoreA Comprehensive Guide to Creating and Managing Security Groups for Your Amazon EC2 Instances
A Comprehensive Guide to Creating and Managing Security Groups for...
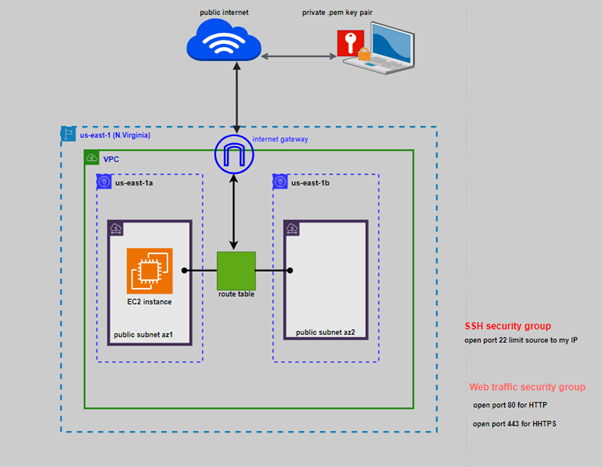
Read MoreEMBARK ON YOUR CLOUD JOURNEY – A GUIDE TO CREATING A NEW AMAZON EC2 INSTANCES
EMBARK ON YOUR CLOUD JOURNEY – A GUIDE TO CREATING...
Read MoreZero Trust Network Access (ZTNA) Best Practices Guide
Zero Trust Network Access (ZTNA) Best Practices Deployment Guide ...
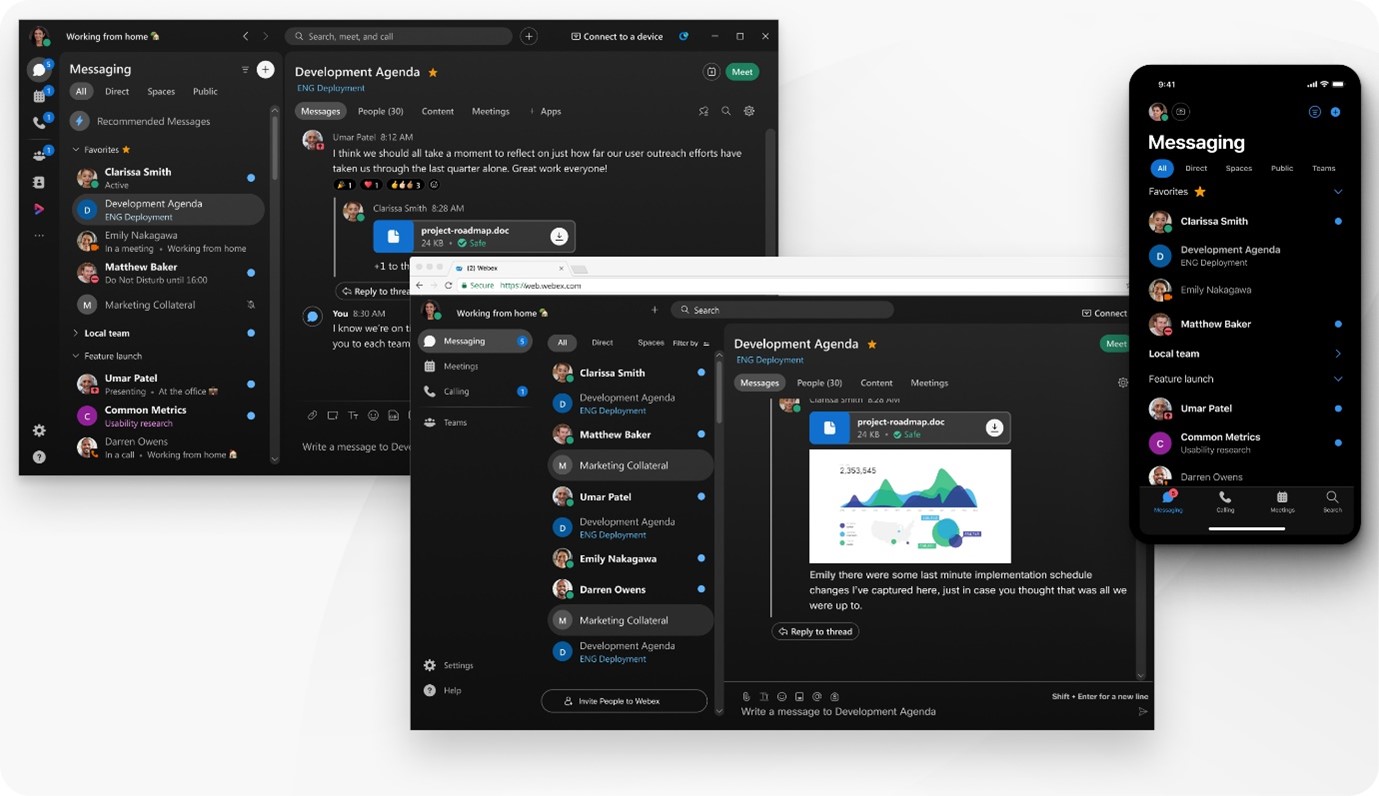
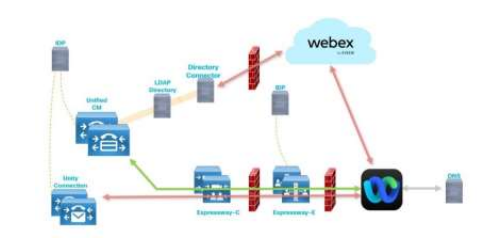
Read MoreCisco WebEx Hybrid Solutions
Cisco WebEx Hybrid Solutions By connecting existing network resources and...
Read MoreFull-Service It Solutions Provider Specilizing In Cybersecurity
Paula Wong, CEO and Founder Built my first computer at...
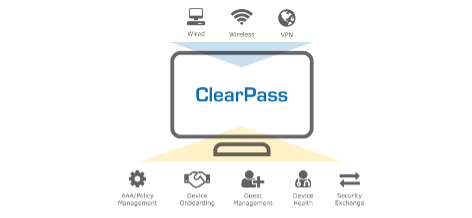
Read MoreClearPass Self Signed Certificate
What are Digital Certificates? Digital certificates are a crucial component...
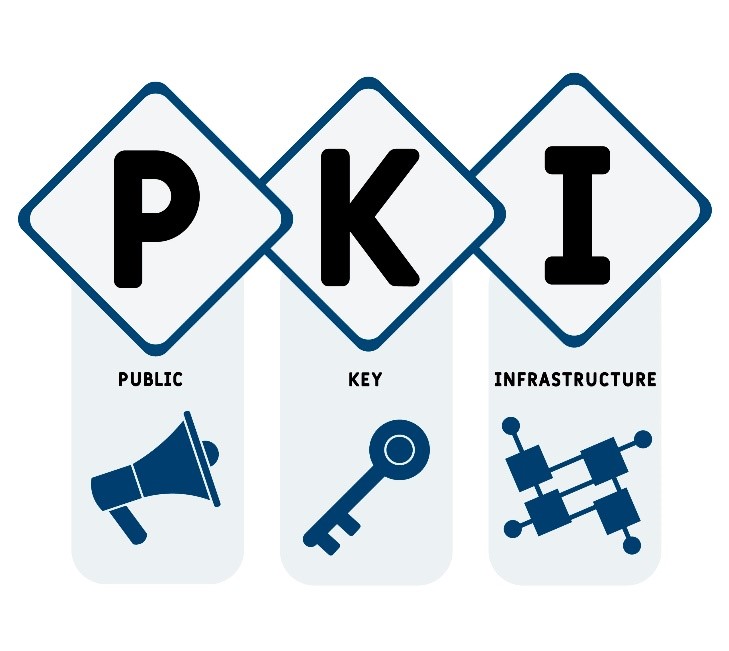
Read MorePKI – Public Key infrastructure
Public Key infrastructure 1. How you can make it healthier...
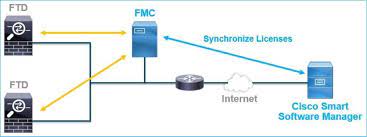
Read MoreConfiguring IP on Cisco Secure Firepower Threat Defense (FTD) & Adding a Secure Firepower Management Center (FMC)
Configuring IP Cisco Secure Firepower Threat Defense (FTD) & Adding...
Read MoreMigrating from Cisco AireOS 3504 WLC to Cisco Catalyst 9800 Controller
Migrating from Cisco AireOS 3504 WLC to Cisco Catalyst 9800...
Read MoreQ&A With Accend Networks
Q&A With Accend Networks Safety Detectives: Please share your company...
Read MoreCloud Hosting Services Vs On-Premises IT Solutions
A lot of companies and people have been talking about...
Read MoreAdvanced Network Services | Dynamic Network Services
Accend has been providing advanced network services for clients for...
Read MoreGlobal Security Solutions | Advanced Security Solutions
Accend has been a Global Security Solutions provider for several...
Read MoreSolarwinds Network Monitoring | Network Monitoring System
Several of our mid-size, municipal and federal clients have required...
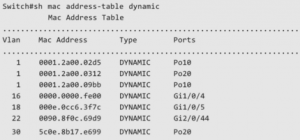
Read MoreHow to Locate a Host On a Switch Given Its MAC Address
One of the most helpful troubleshooting methods for any IT...
Read MoreVmware Service Provider | Vmware Cloud Services
For over a decade, Accend has helped countless businesses maximize...
Read MoreNetwork Consultant Company | Network Services California
Are you inundated with IT projects and not sure whom...
Read MoreGoogle Cloud Endpoints | Google Cloud Services
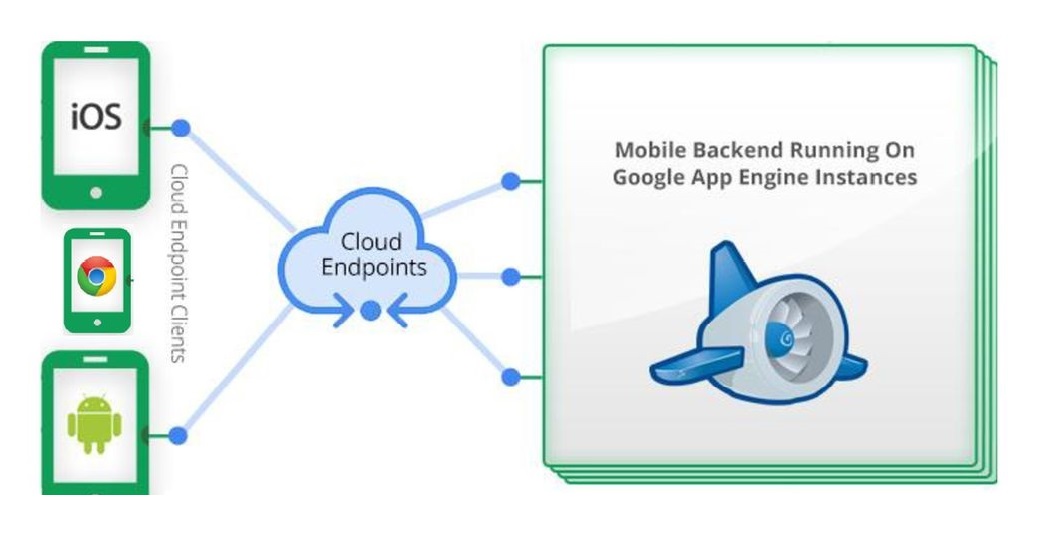
Apple iOS, Androids, Apple iPAD, Chromebooks, and other tablets are...
Read More