How To Use Amazon Inspector: an automated and continual vulnerability management at scale.
What is Amazon Inspector?
Amazon Inspector automatically discovers workloads, such as Amazon EC2 instances, containers, and Lambda functions, and scans them for software vulnerabilities and unintended network exposure.
How it works.
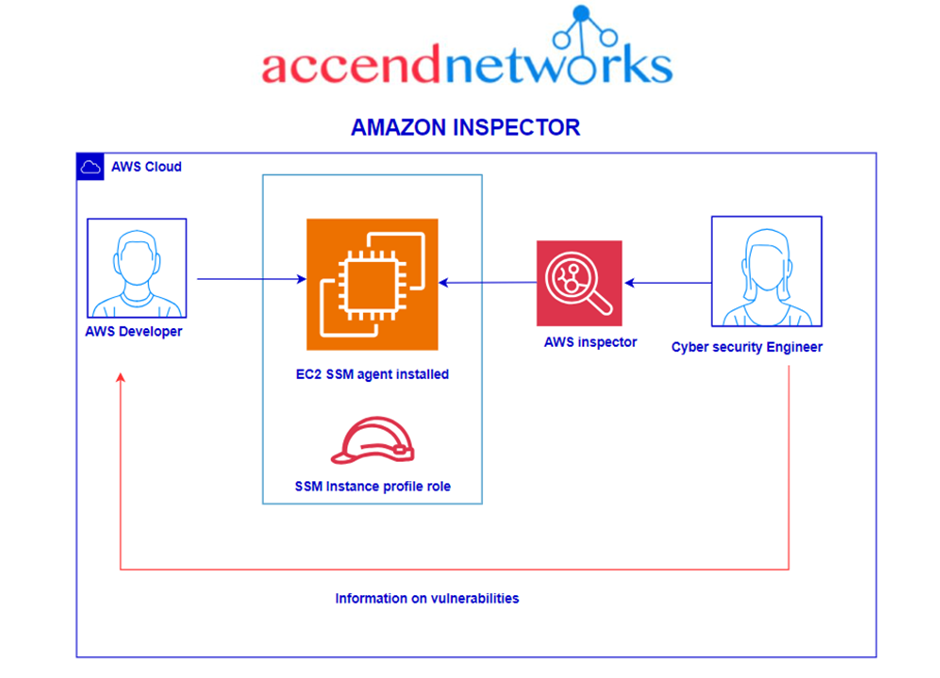
Amazon Inspector is an automated vulnerability management service that scans AWS workloads for software vulnerabilities and unintended network exposure. At a high level, AWS Inspector is dependent on an SSM agent to be installed in the EC2 instance that will be used to scan and report the security findings. Additionally, the EC2 will need a role that grants SSM to the EC2 instance. AWS Inspector uses the SSM agent to connect to the instance. Note that as of November of 2023, there is a new agentless scan option that is in preview.
AWS Inspector can be supported at the organizational level and scan all accounts in the organization; however, the scope of this blog will be a single account.
In this use case, we will see how Amazon Inspector helps to identify the network vulnerability by performing an accessibility check.
Let’s proceed as follows.
Login to your AWS account using your admin account or an account with admin privileges.
Creation of a new IAM role for the EC2 use case
Remember, the AWS Inspector is dependent on an SSM role or a role with SSM permissions to be able to communicate with the SSM agent inside the EC2. Let’s create this role.
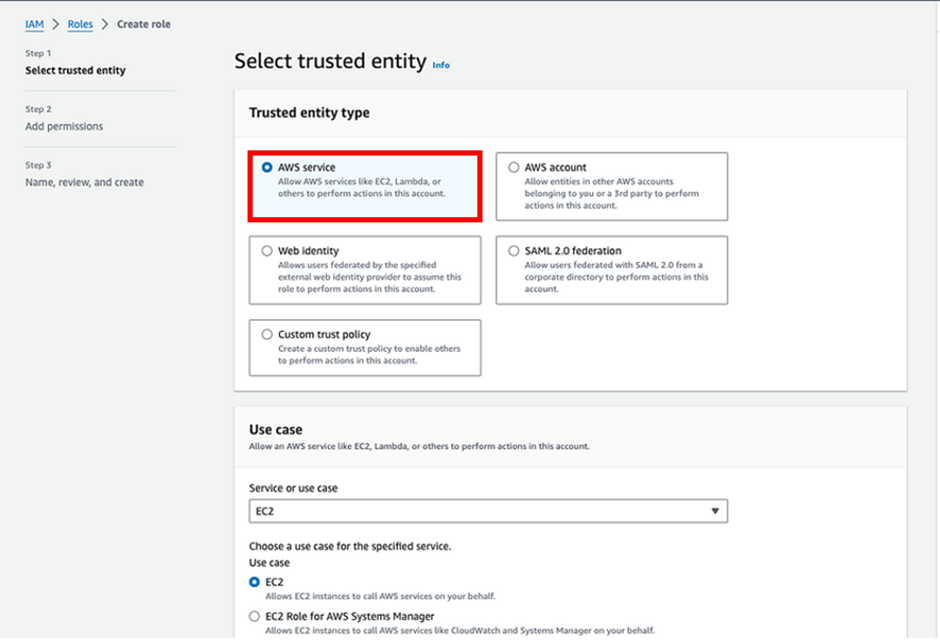
Navigate to IAM, click on Roles then click on the Create role button. You will be prompted to select an entity type, in our case select “AWS service”, and for service select EC2. This will create a trust policy that will allow EC2 to assume it. Click Next.
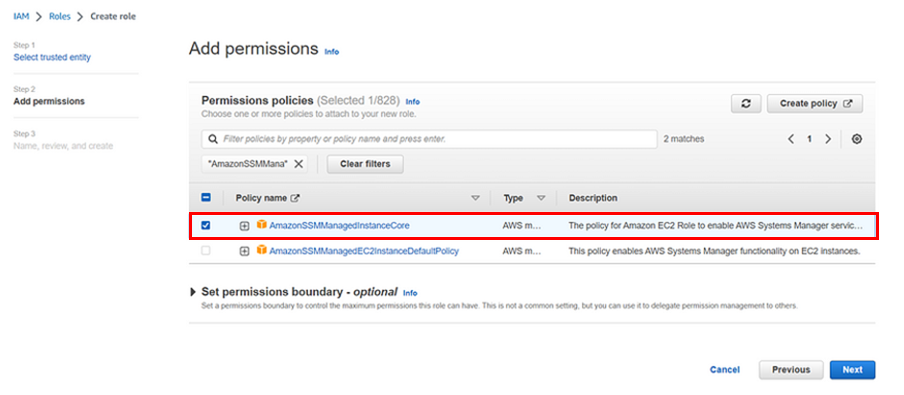
Now we must add permissions to the role that the EC2 will assume. Under the Add permissions config screen, search for AmazonSSMManagedInstanceCore, select it, and click Next.
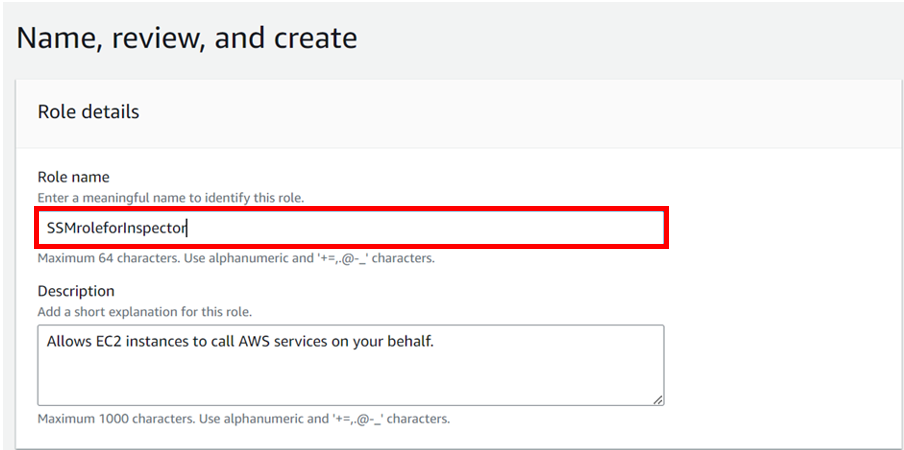
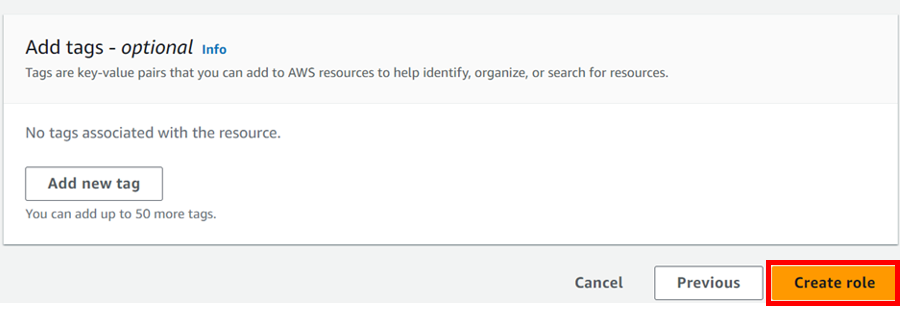
In the next window, give the role a name (SSMRoleForInspector) and click Create role.
Creation of EC2 Instance
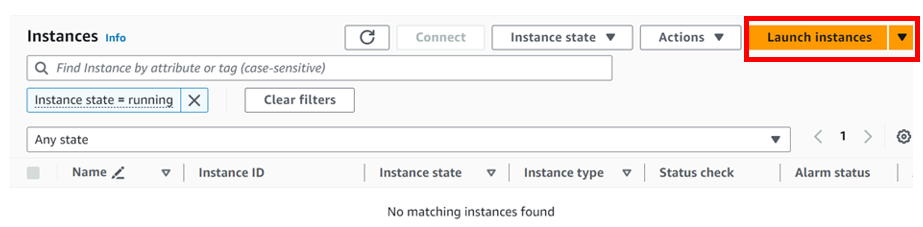
Go to the AWS Management Console, select instances in the EC2 console, then click Launch instances in the instances dashboard shown below.
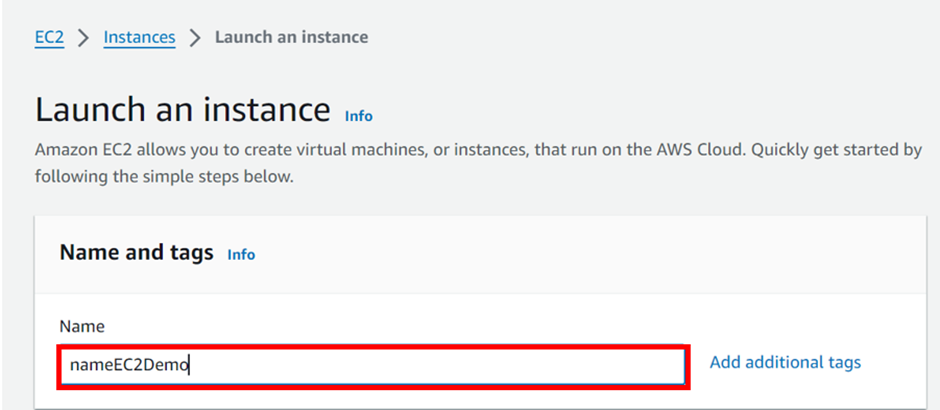
Add the Name as nameEC2Demo, and under instance type, select t2. Micro which is free tier eligible. Scroll down.
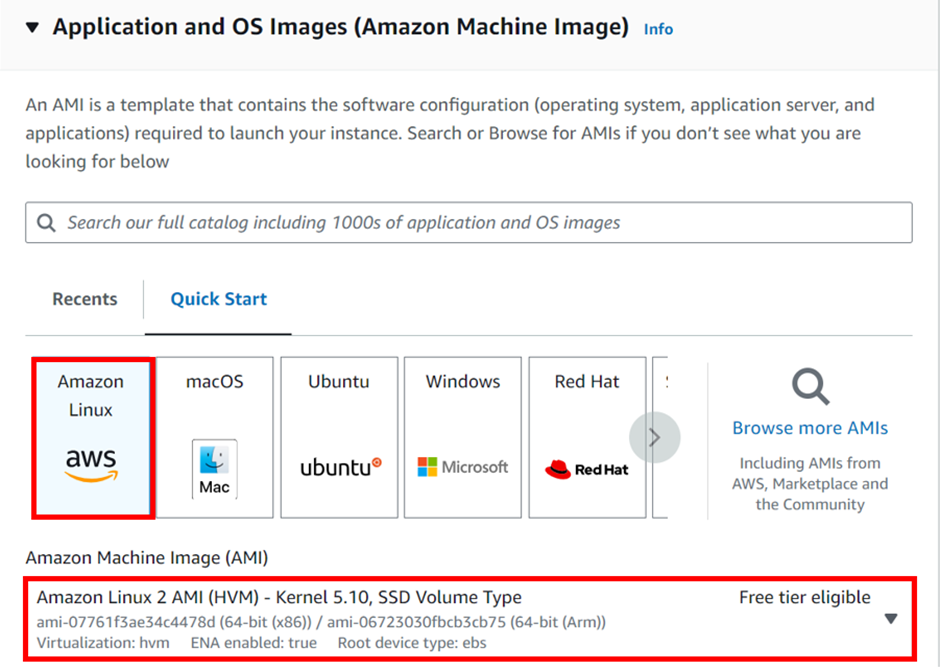
Under application and OS, select the QuickStart tab then select Amazon Linux. Under AMI select Linux 2 AMI this is also free tier eligible.
Scroll down to the firewall and security section, Select the existing security group then choose the default security group. Click on the launch instance.
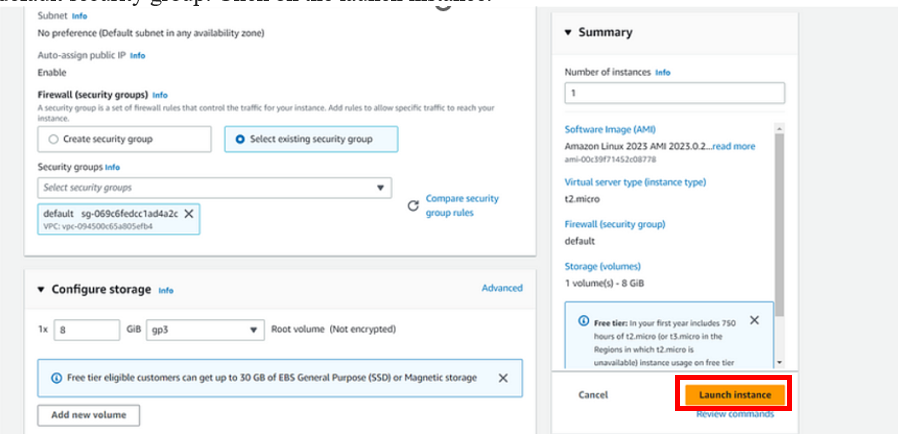
Attach the SSM agent role to the EC2 instance.
Select your instance, click on Actions, then click Security, and then click on Modify IAM role.
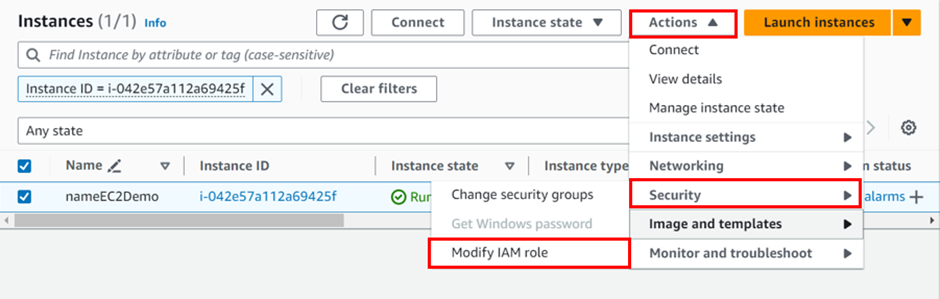
Within the Modify IAM role screen, select the role you created earlier. In my case, I am selecting SSMRoleForInspector Click on Update IAM role.
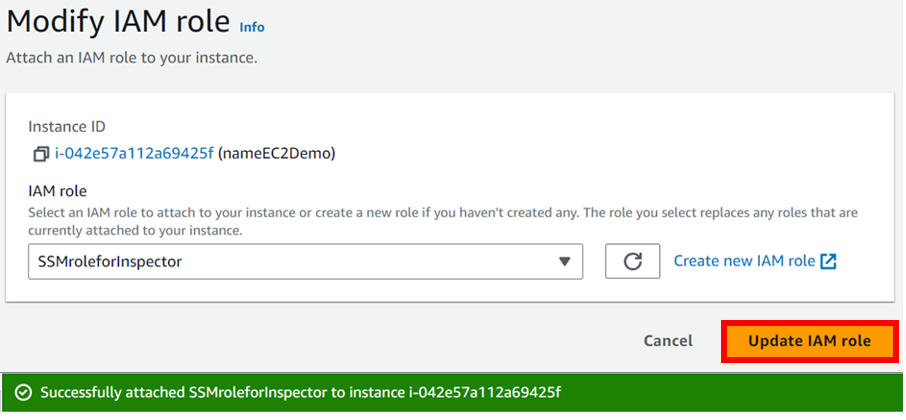
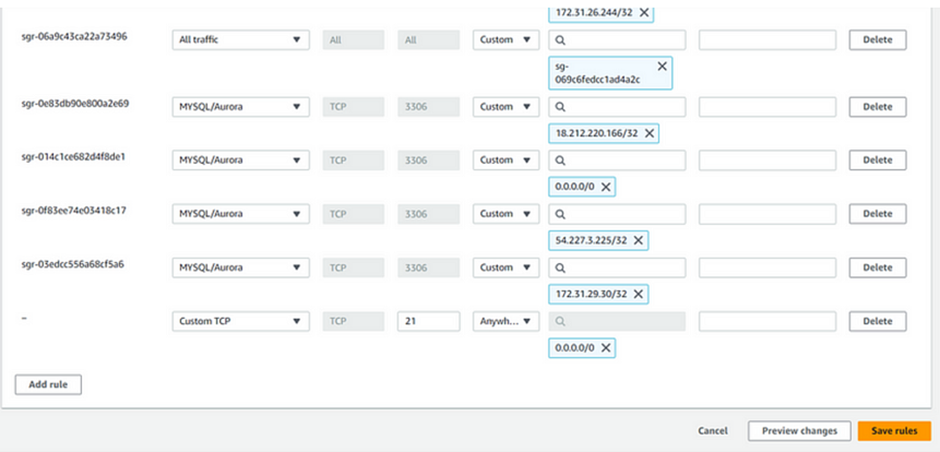
Select your instance then move to the security tab, Select the default security group. Then click edit the inbound rule.
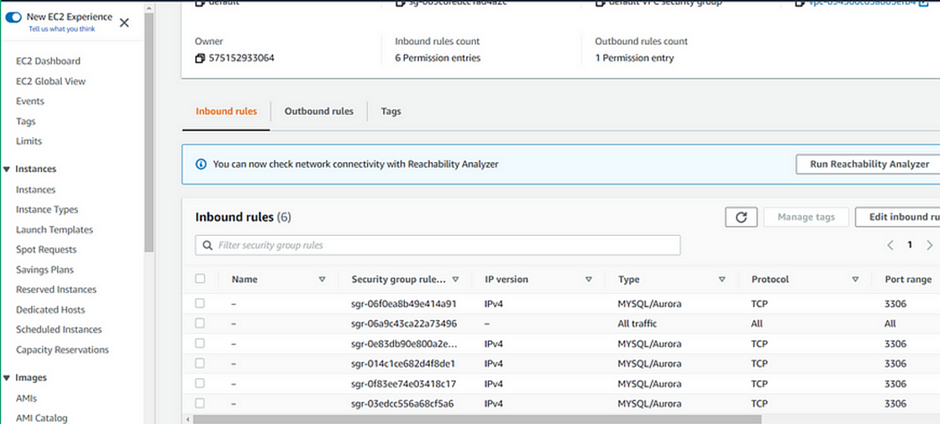
Click Add a new rule and open the port21 to anywhere from the internet then click Save rule.
Note: Port 21 is not recommended to keep open on our instances. We are inducing a security thread here.
Running an Amazon Inspector -To Discover the security vulnerabilities.
Go to the management console under services and select Amazon Inspector. Then click Get Started.
Activate Inspector and view your permissions.
Once Inspector is activated, we will get a green banner as our first scan is underway.
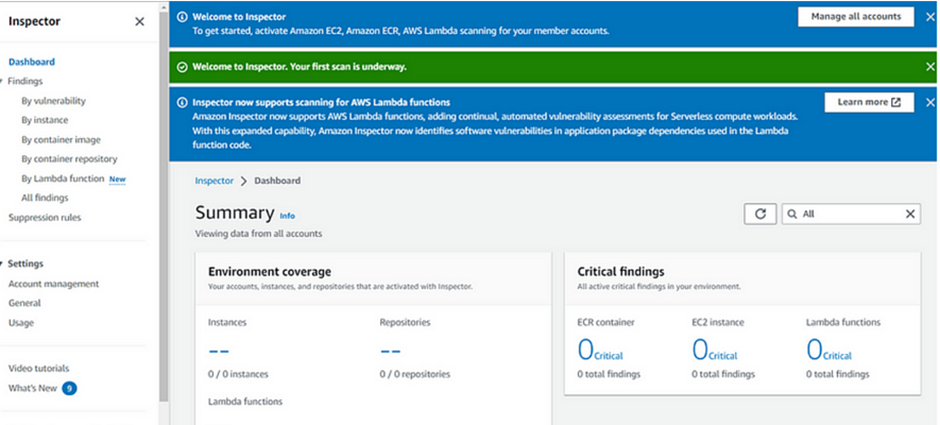
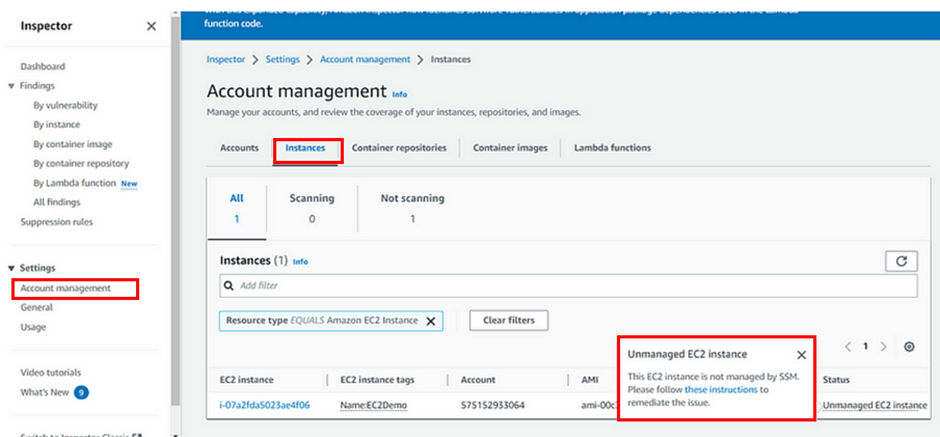
Go to Account Management, then move to the Instances tab and select unmanaged instances. You will see the below message.
This means this instance is not managed by SSM. Please click on the instructions hyperlink to remediate the issue.
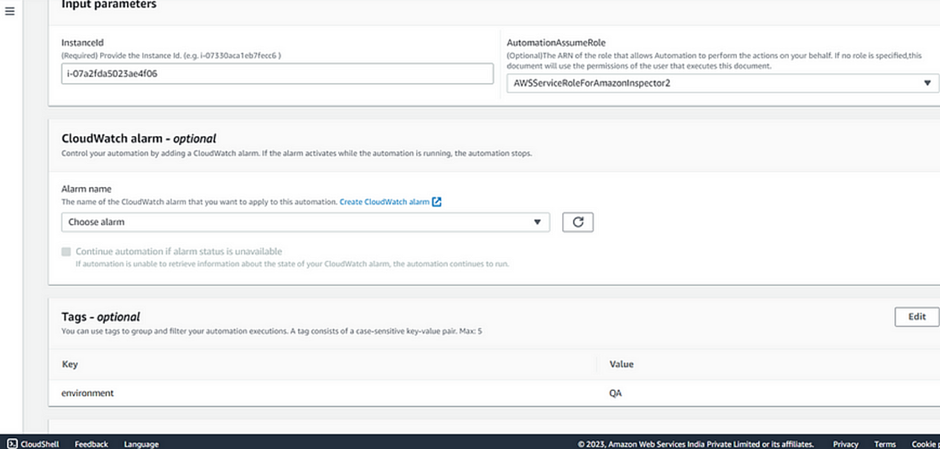
Eventually, it will redirect to AWS Systems Manager, in input parameters, choose the instance ID and Click Execute.
Once execution is completed, Go to Amazon Inspector and select the instance findings.
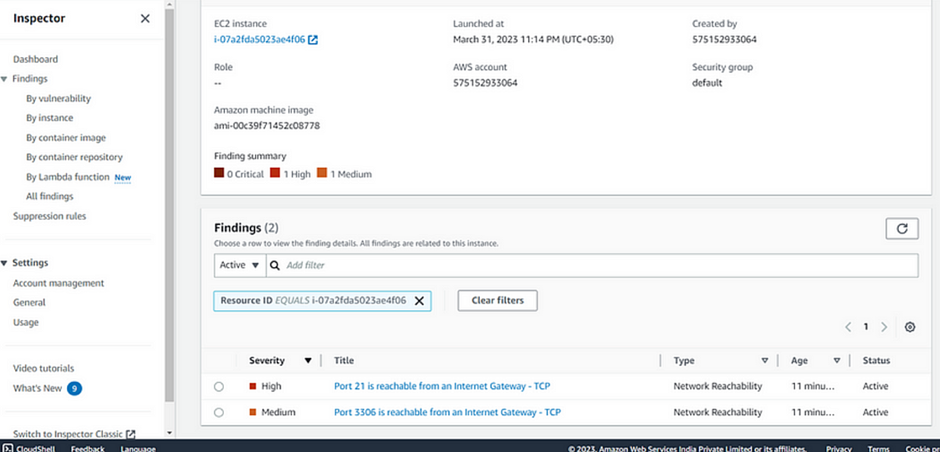
Go to findings, where you will see the induced security thread as high.
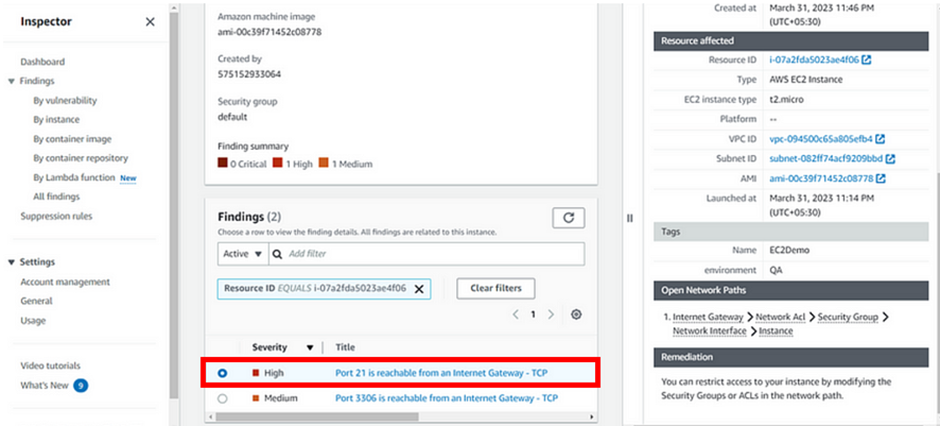
Go to EC2 Instances, Inbound security group, and delete the induced port21. Click Save rules.
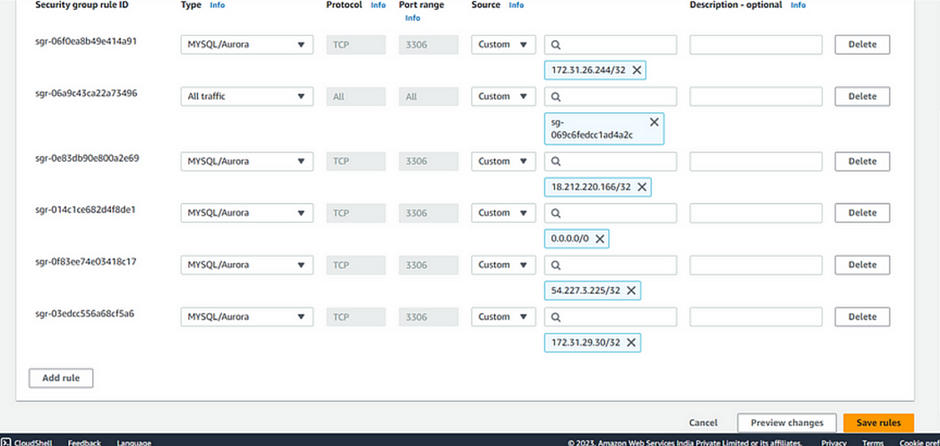
To review the findings again, Go to Account Management, Instances, and select unmanaged instances. Follow the instructions like giving out instance ID etc. Click execute.
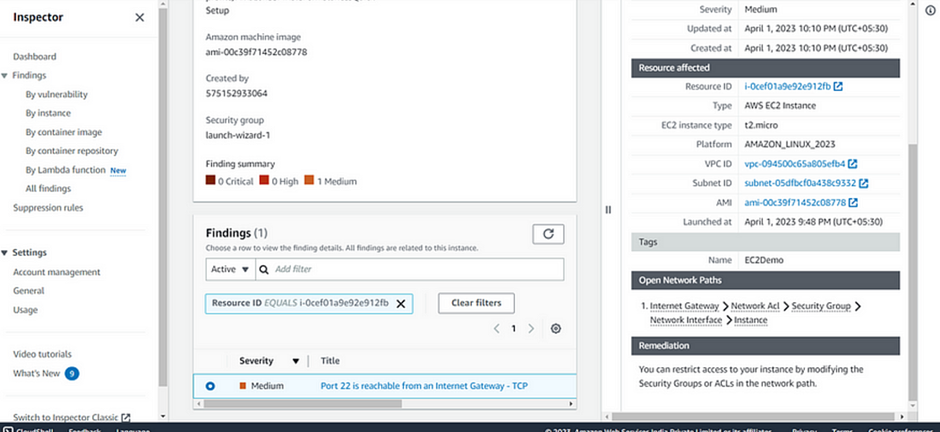
With this, we have seen now how Amazon Inspector helps to find the Network Reachability vulnerability.
To avoid billing, terminate the instances that you had created and make sure you deactivate the Amazon inspector for all instances.
This brings us to the end of this demo. Stay tuned for more.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com.
Thank you!

Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Your article helped me a lot, is there any more related content? Thanks!
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?