Secure File Uploads and Downloads in S3 Using Presigned URLs

Amazon Simple Storage Service (S3) is a highly scalable object storage service used for storing and retrieving large amounts of data. While S3 provides a straightforward way to manage files, ensuring secure access to these files is crucial. One effective method to securely upload and download files from S3 is by using presigned URLs. This article delves into what presigned URLs are, how they work, and a hands-on demo.
S3 Presigned URL
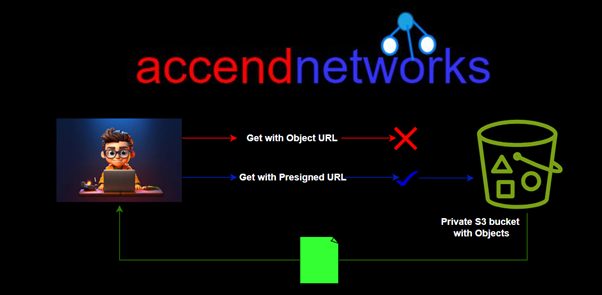
Presigned URLs are URLs that provide temporary access to objects in S3 without requiring AWS credentials directly from the user. When you create a presigned URL, you essentially generate a URL that includes a signature, allowing anyone with the URL to perform specific actions (like upload or download) on the specified S3 object within a limited time frame.
When you create an S3 bucket, it is private by default, and it is up to you to change this setting based on your needs. If you want a user to upload or download files in a private bucket without making the bucket public or requiring AWS credentials or IAM permissions, you can create a presigned URL.
Presigned URLs work even if the bucket is public, but the main purpose of presigned URLs is to help you keep objects private while allowing limited and controlled access when necessary.
Requirements for Generating Presigned URLs
A presigned URL must be generated by an AWS user or an AWS application that has access to the bucket and the object in the bucket at the time of creation. When a user makes an HTTP call with the presigned URL, AWS processes the request as if it was performed by the entity that generated the presigned URL.
Usage and Expiration
Presigned URLs can be shared with temporarily authorized users to allow them to download or upload objects. They can only be used for the method specified when generating the URL. For example, a GET-presigned URL cannot be used for a PUT operation.
There is no default limit on the number of times a presigned URL can be used until it expires.
Get presigned URLs
A GET-presigned URL can be used directly in a browser or integrated into an application or webpage to download an object from an S3 bucket. It can be generated using the AWS Management Console, AWS CLI, or AWS SDK.
In the following, I will demonstrate how to generate a GET-presigned URL using the AWS Management Console.
Generating Get presigned URL with the console
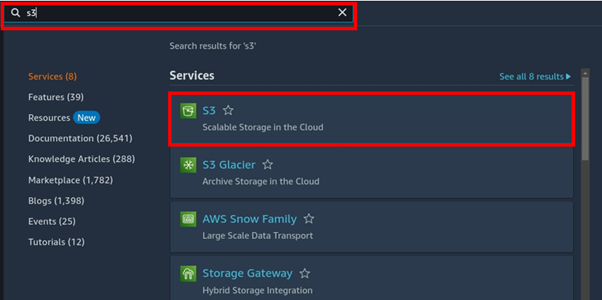
Log in to the management console, in the search box, type s3 then select s3 under services.
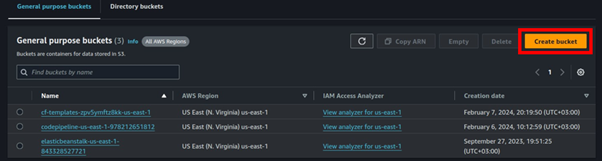
In the s3 UI select Create Bucket.
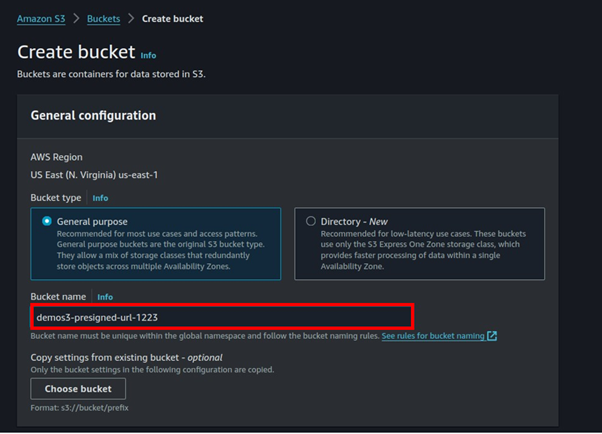
In the create bucket UI, select a unique name for your bucket then Scroll down.
Make sure all public access is blocked.
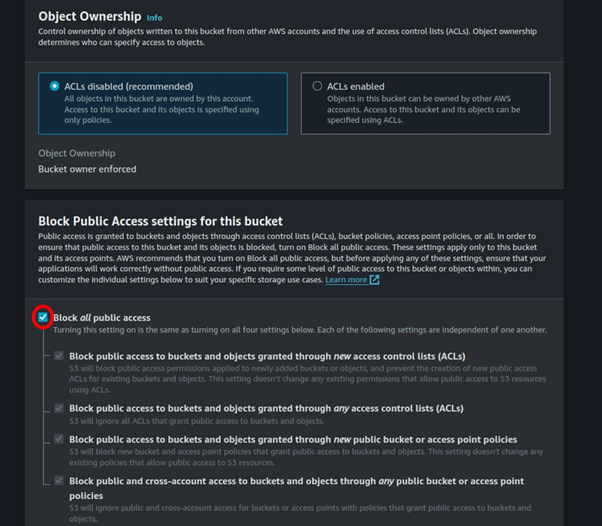
We will leave the remaining settings as default, then scroll down and click Create Bucket.
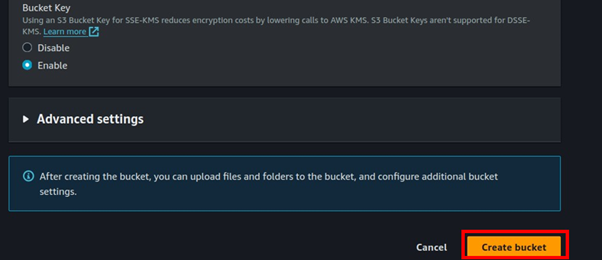
Our s3 bucket has been successfully created.
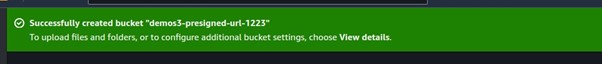
Select your bucket then select upload.
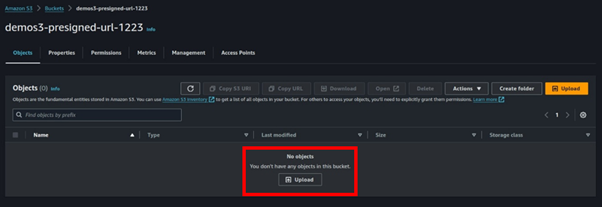
In the upload UI, select add files
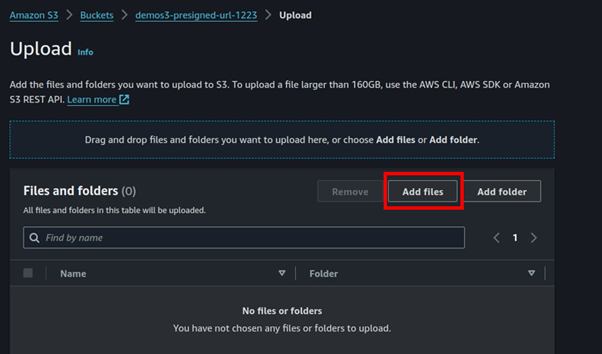
Select your file then click Upload.
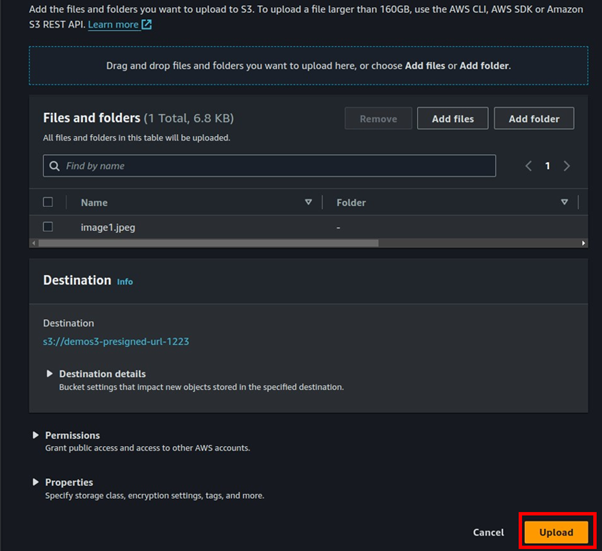

Once our object has been successfully uploaded, remember our bucket is private since we blocked all public access.
Click the object you uploaded select the object URL then paste it into your Favorite browser.
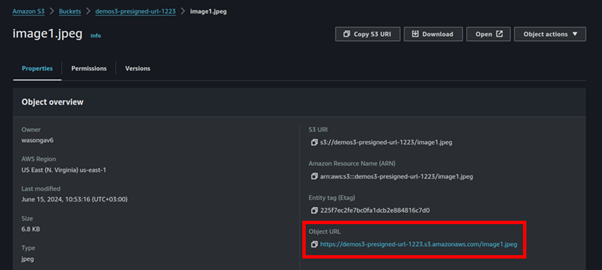
This was expected, we could not access our object since our bucket is private. We will now leverage the s3 presigned URL to securely access our object without making our bucket public.
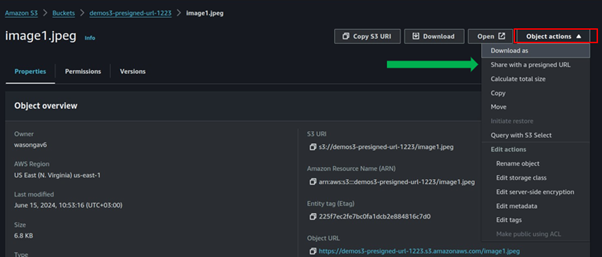
Still, in the object UI, select the drop-down object action. Then select Share with the presigned URL.
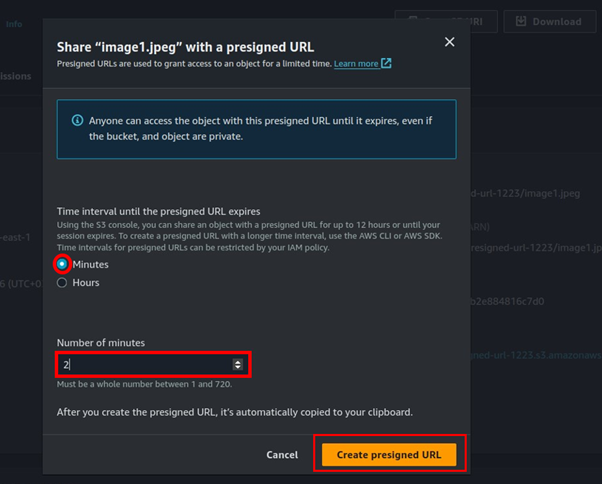
For time interval until the URL expires can be minutes to several hours, for this demo I will only give it 2 minutes. So, select minutes then for number of minutes, select two then click Create presigned URL.
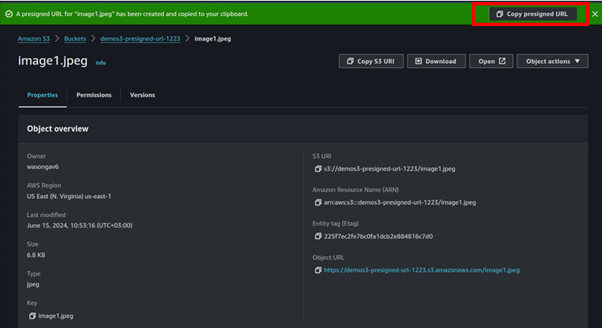
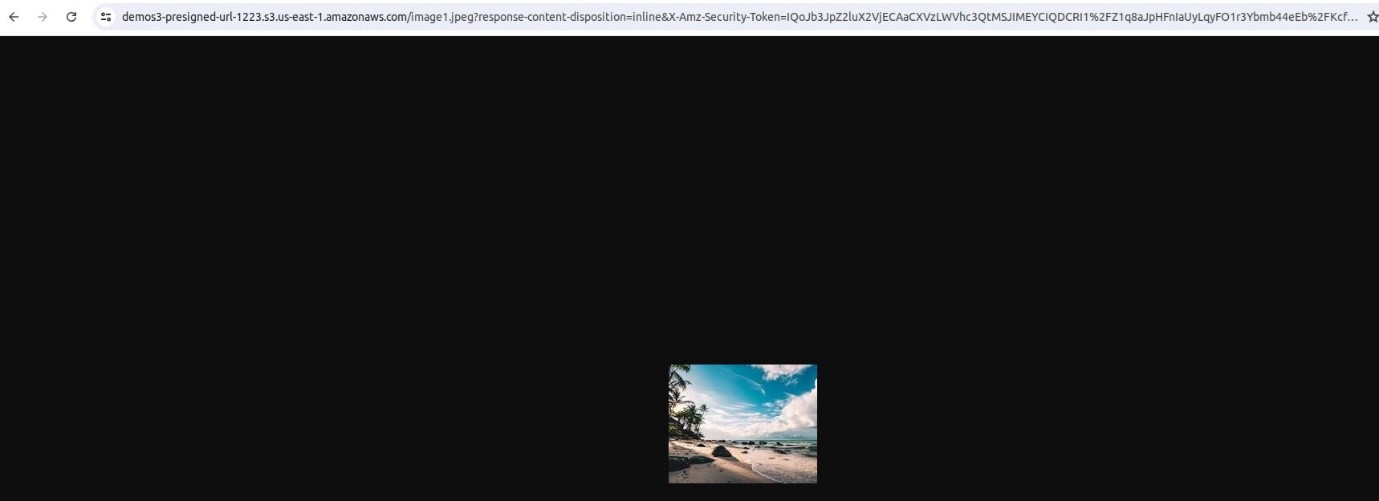
The presigned URL is successfully created, copy the presigned URL then paste it to your browser.
Success now we can access our object.
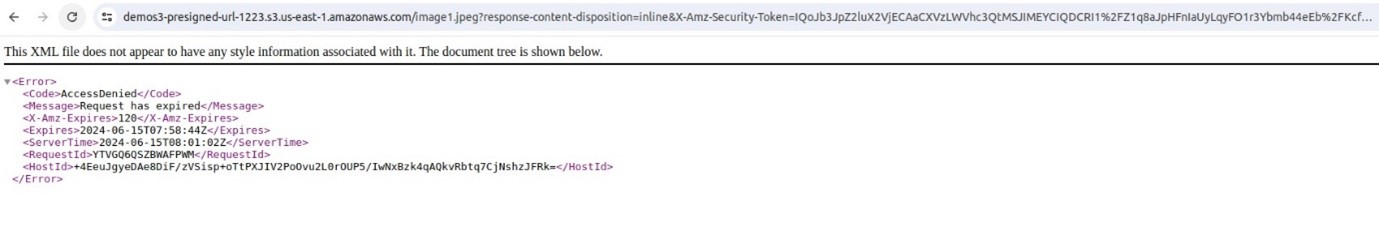
Since we only gave two minutes for this demo, attempting to access our private object using the presigned URL after it has expired will result in an access denied message as shown bellow.
S3-presigned URLs provide a secure and efficient way to grant temporary access to Amazon S3 objects without exposing AWS credentials. They are easy to implement, allowing controlled, time-limited access for specific operations. This feature enhances data sharing and access management, ensuring security and flexibility in handling S3 resources.
This brings us to the end of this blog. Clean up.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com.
Thank you!
