EC2 Instance Connect Endpoint: Secure Access to Private Subnet Instances Without Internet
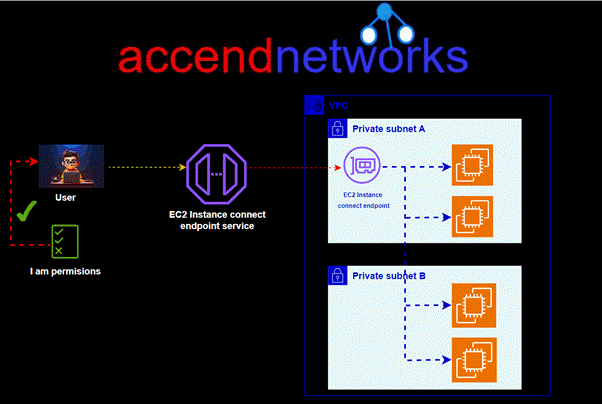
Amazon Web Services offers EC2 Instance Connect Endpoint. This powerful feature enables secure SSH access to private EC2 instances with private IP addresses without the need for managing SSH keys or bastion hosts. With EC2 Instance Connect Endpoint, we can establish SSH and RDP connectivity to our EC2 instances without relying on public IP addresses. This means we can have remote connectivity to instances in private subnets without the need for public IPv4 addresses.
What is an EC2 instance connect endpoint?
EC2 Instance Connect Endpoint allows you to connect to an instance without requiring the instance to have a public IPv4 address. You can connect to any instances that support TCP.
EC2 Instance Connect Endpoint combines AWS Identity and Access Management (IAM) based access controls with network-based controls such as Security Group rules. This combination allows you to restrict access to trusted principals and provides an audit trail of all connections through AWS CloudTrail.
Traditional way of accessing EC2 instance in the private subnet
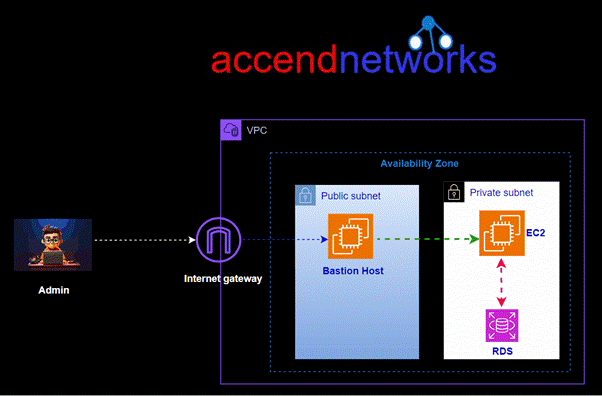
In the past, customers had to create Bastion Hosts to tunnel SSH/RDP connections to instances with private IP addresses. However, this approach required additional operational overhead for patching, managing, and auditing the Bastion Hosts, as well as incurring extra costs. EC2 Instance Connect Endpoint eliminates these costs and operational burdens associated with maintaining bastion hosts.
Additionally, the service facilitates detailed auditing and logging of connection requests, providing administrators with a comprehensive overview of who is accessing resources and when. This feature is invaluable for security and compliance monitoring, enabling a proactive approach to managing and mitigating potential security risks.
How it works
First, we create an EC2 Instance Connect Endpoint in a subnet in our VPC then, when you want to connect to an instance, you specify the ID of the instance. You can optionally provide the EC2 Instance Connect Endpoint. The endpoint acts as a private tunnel to the instance.
Once you create an EC2 Instance Connect Endpoint in a subnet, you can use the endpoint to connect to any instance in any subnet in your VPC provided our VPC is configured to allow subnets to communicate.
Let’s now dive into the hands-on, we will start by creating an EC2 instance.
Log in to the AWS console as a user with admin user privileges, or make sure you have the necessary permissions.
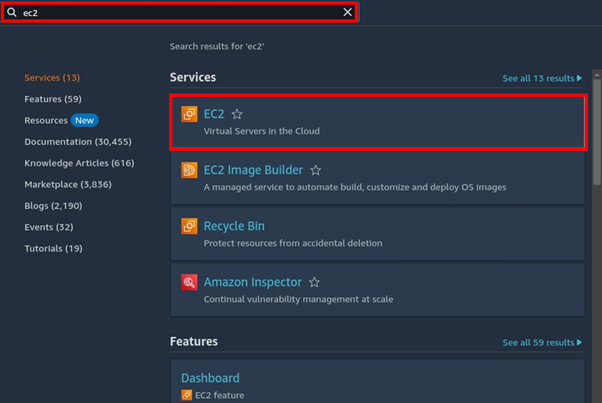
In the search bar, type EC2 then select EC2 under services to go to the EC2 console.
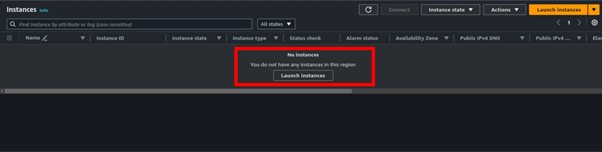
On the left side of EC2 UI, select instances then click launch instances.
Fill in your instance details. select the QuickStart tab then select Amazon Linux AMI. Scroll down.
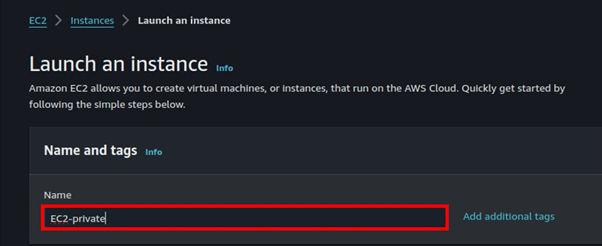
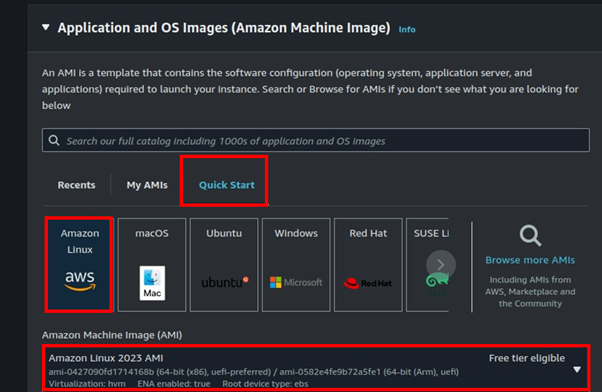
Select t2. Micro, free tier eligible. Under key pairs, we will not need them so select the drop-down button then select move without key pair.
Move to the networking tab then click edit.
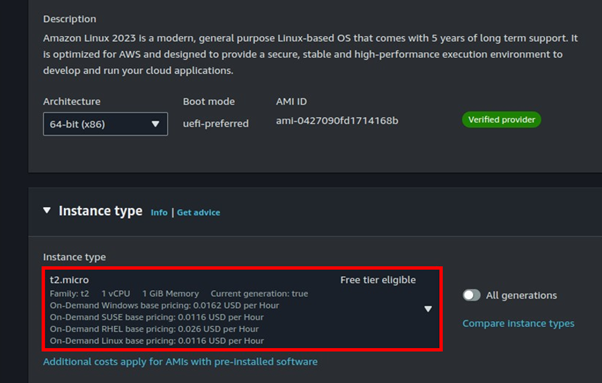
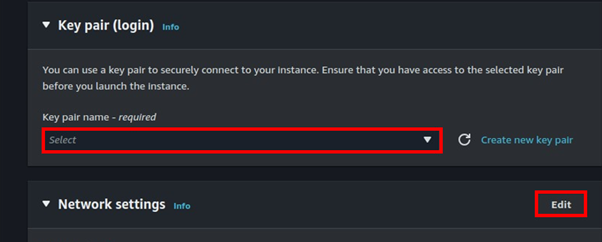
We will leverage the default VPC. Select your preferred subnet then under Auto-assign public IP, select the drop-down button and select disable. You create a security group or select one with SSH port 22 open.
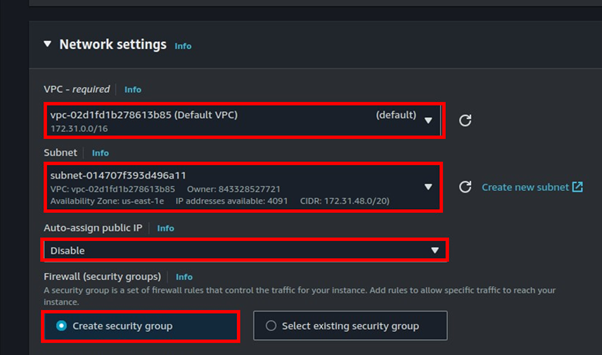
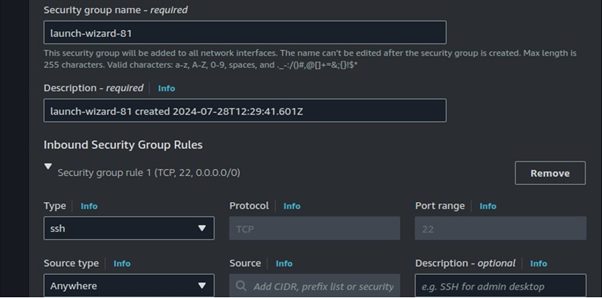
Scroll down and select Create instance.
While our instance is launching let’s move to the VPC dashboard.
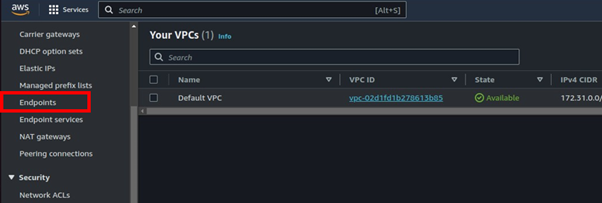
On the left side of the VPC UI, select endpoints.
Select Create Endpoint.
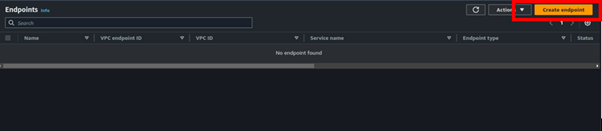
Provide the name of your endpoint. Under the service category, select the radio button for the EC2 Instance connect endpoint.
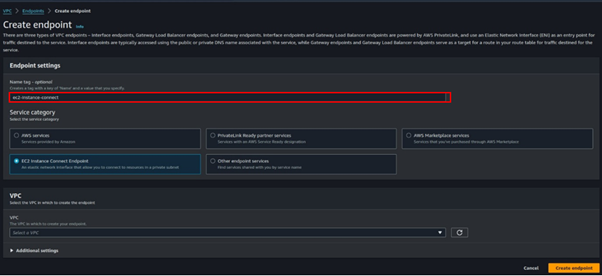
For VPC, select the drop-down button and select your VPC. Again, for subnets select the subnet where you launched the Instance. These are the only required settings. Click Create Endpoint.
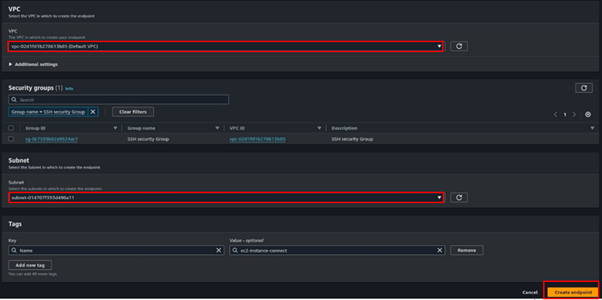
After successful creation, it will take a couple of minutes in the pending state and then become available.
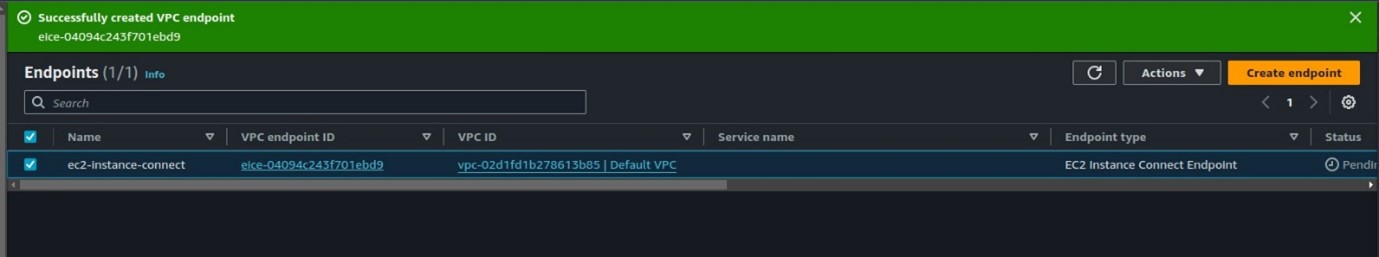
After waiting for a few minutes, our endpoint is now available.
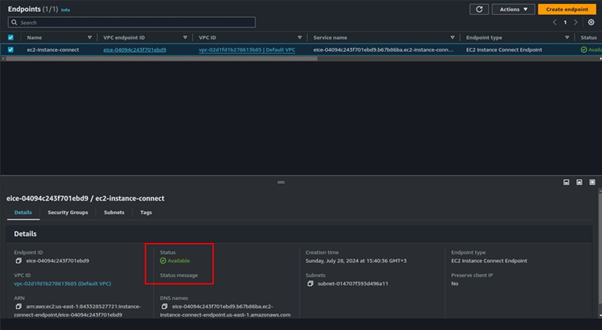
Go back to the EC2 instance dashboard, select the instance you created then select Connect. You will be brought to the connect instance dashboard.
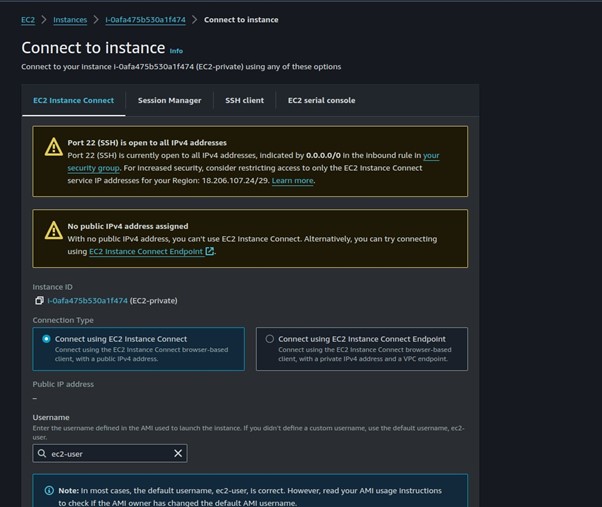
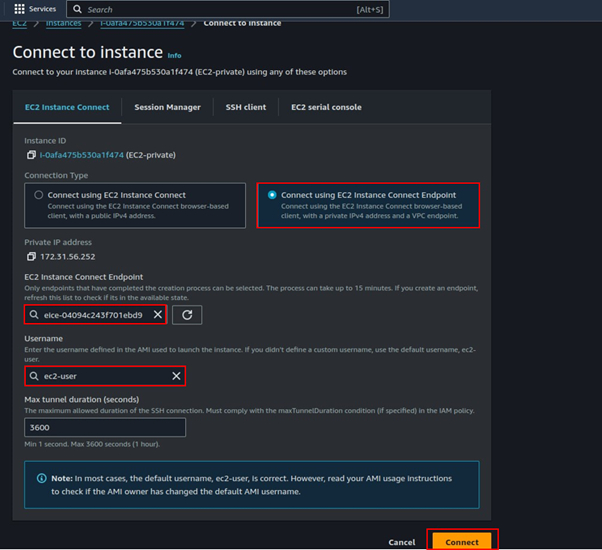
Select the radio button on connect using EC2 Instance connect Endpoint. Fill in the required details. select the endpoint you created. The user name for amazon Linux user is ec2 -user. Click connect.
Success we are in our EC2 instance, and we can see the IP address is the private one.
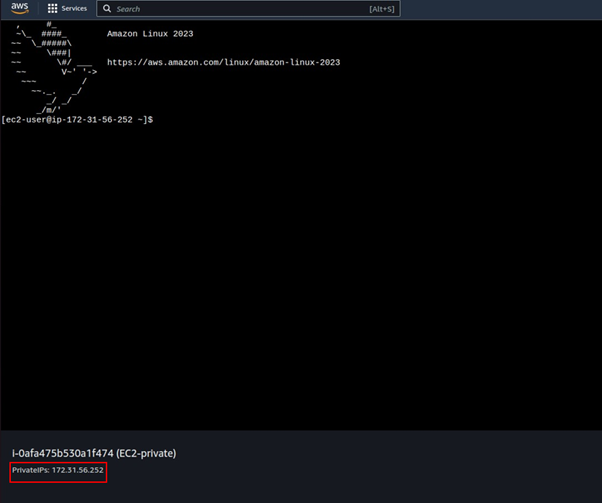
We have managed to connect to an EC2 instance in the private subnet with a private IP address. Objective achieved.
We can also use the below command to connect to the instance in our terminal. Make sure you have AWS CLI installed and configured.
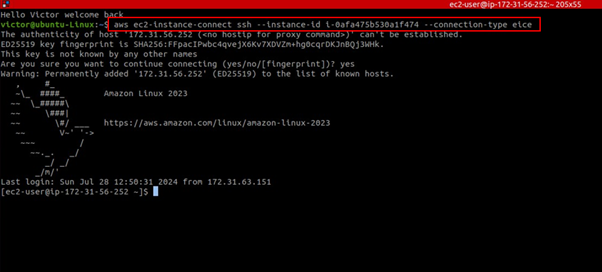
This brings to the end of this blog, bring everything down.
Conclusion
EC2 Instance Connect Endpoint provides a secure solution to connect to your instances via SSH or RDP in private subnets without Internet Gateways, public IPs, agents, and bastion hosts.
Thanks for reading and stay tuned for more.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com.
Thank you!
