What are Digital Certificates?
Digital certificates are a crucial component of modern cybersecurity and online authentication. They are essentially electronic documents used to verify the identity of individuals, devices, or services on the network. Digital certificates serve several important purposes, with the primary one being the assurance of the authenticity and security of online communications and transactions.
Certificate Authorities (CAs) are entities responsible for issuing digital certificates. CAs are organized into a hierarchical structure, with Root CAs positioned at the top of the hierarchy. When a Root CA signs digital certificates, it employs its private key to create digital signatures. These signatures serve as a cryptographic seal of approval, attesting to the authenticity and integrity of the certificates being signed. The signed certificates, whether they belong to intermediate CAs or end entities, inherit the trust associated with the Root CA.
Types of CAs That Sign Digital Certificates?
Certificates can be signed by one of three types of CAs:
- Public Certificate Authority (CA)
- Private CA
- Self-signed certificates.
Public CA Signed Certificates are perhaps the most familiar type of digital certificate. These certificates are issued by well-known and trusted third-party Certificate Authorities. Certificates signed by Public CAs enjoy widespread recognition and trust across the internet. Web browsers and operating systems come preloaded with the root certificates of these CAs, ensuring that users won’t encounter security warnings when visiting websites secured with these certificates. Public CA certificates work seamlessly across a vast array of devices, browsers, and platforms, ensuring a consistent and secure user experience.
Private CA Signed Certificates are generated and managed by organizations for their internal use. These CAs operate within closed environments. Private CAs provide complete control over certificate issuance and management. This makes them invaluable for securing internal network resources, services, and communications. Using Private CAs can be cost-effective, especially for organizations that require multiple certificates for various internal services. There are no ongoing per-certificate fees. The main drawback of these certificates is that the private root CA must be trusted by all devices that need to build trust relation ship using these certificates.
Self-signed certificates are precisely what the name suggests—they are generated and signed by the entity for which they are intended, without the involvement of any external CA. Self-signed certificates are free to create and use, making them a budget-friendly choice for those on a tight budget. These certificates can be generated and deployed rapidly without the need for external validation, which is ideal for testing and development environments.
There are some limitations with self-signed certificates:
- Limited Trust: Self-signed certificates are not trusted by default in most web browsers and systems. Users will often encounter security warnings when accessing services secured with self-signed certificates.
- Security Risks: Since self-signed certificates do not undergo third-party validation, there is a higher risk of them being used maliciously or mistakenly, potentially compromising security
Follow Recommendations:
As a RADIUS server, ClearPass benefits from digital certificates for mutual authentication to ensure the security and trustworthiness of the authentication and authorization process in network environments. Mutual authentication between the RADIUS server and the client provides several crucial advantages:
- Protection Against Impersonation: Mutual authentication using digital certificates prevents impersonation attacks. Without certificates, malicious parties could potentially impersonate either the RADIUS server or the client, leading to unauthorized access or the interception of sensitive data. Certificates verify the authenticity of both parties involved in the communication, making it significantly more difficult for attackers to impersonate them.
- Enhanced Security: Mutual authentication significantly enhances security by requiring both the server and the client to present valid digital certificates. This means that not only does the client verify the server’s identity (as is the case with one-way authentication), but the server also verifies the client’s identity. This two-way trust ensures that only authorized and trusted parties can participate in the authentication and authorization process.
- Protection Against Man-in-the-Middle (MITM) Attacks: Digital certificates help mitigate MITM attacks, where an attacker intercepts communications between the RADIUS server and the client. In a mutual authentication setup, an attacker would need to possess valid certificates for both the client and the server to successfully impersonate them, making MITM attacks significantly more challenging.
- Identity Verification: Mutual authentication using digital certificates ensures that the client and the RADIUS server verify each other’s identities before proceeding with the authentication process. This adds an extra layer of assurance that the parties involved are legitimate and authorized to access the network resources.
- Secure Key Exchange: During the mutual authentication process, the client and the RADIUS server may also exchange encryption keys securely. This is essential for establishing a secure communication channel for the exchange of sensitive data, such as usernames and passwords. Without mutual authentication, there would be a greater risk of these keys falling into the wrong hands.
- Compliance and Security Best Practices: Many security standards and best practices recommend or require mutual authentication using digital certificates to ensure the security of network access control systems like RADIUS. This includes protocols like EAP-TLS (Extensible Authentication Protocol-Transport Layer Security), which relies on mutual authentication through certificates for secure authentication.
- Protection of Sensitive User Data: RADIUS servers often handle sensitive user data, including usernames and passwords. Mutual authentication using digital certificates helps safeguard this sensitive information by ensuring that it is transmitted securely between trusted parties.
ClearPass Seld-Signed Certificate Renewal?
Although public or private Cas are recommended in many cases for ClearPass EAP or HTTPS services, there are cases where self-signed certificate provides some advantages like ease of generation and renewal. In this article I am explaining the steps required to renewing/issuing-a-new self-signed certificate for different ClearPass certificates:
1- Login to ClearPass Policy Manager from WebUI.
2- From the left side menu, click on administration.
3- From the “Administration” sub-menu go to Administration Certificates Certificate Store.
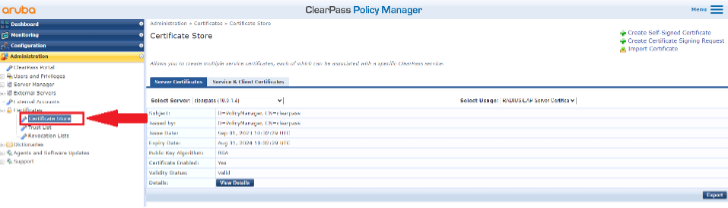
4- From this page you can see current certificates for different usages. You can select a combination of server (if you have multiple servers in a cluster) and usage. Usage can be one of the following options in ClearPass 6.9
- RADIUS/EAP
- HTTPS(ECC)
- HTTPS(RSA)
- RadSec Server
- Database Server
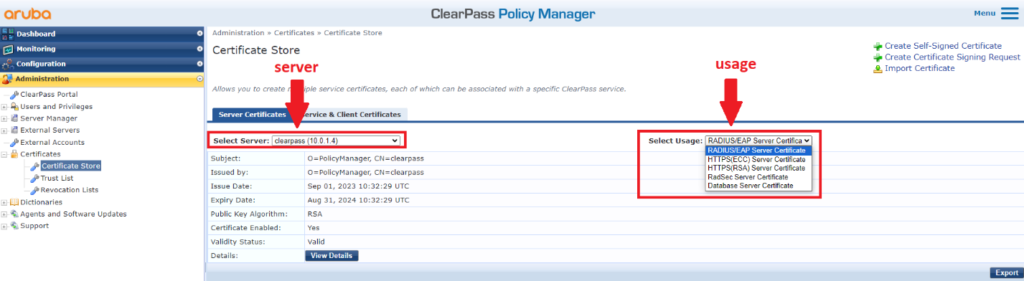
5- Select the certificate you want to reissue/renew and verify issue and expiry dates.
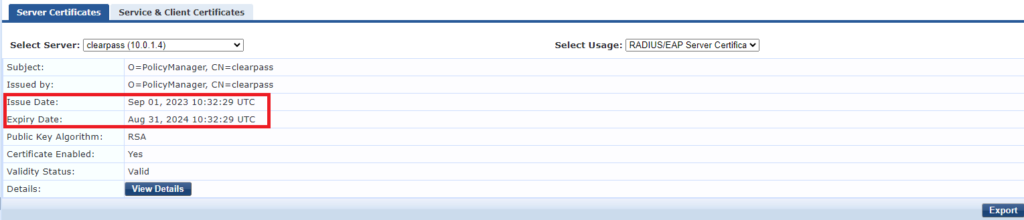
6- You can export the certificate from this page, you can also view details (I suggest you capture the current details if you want the new certificate to match the current one)
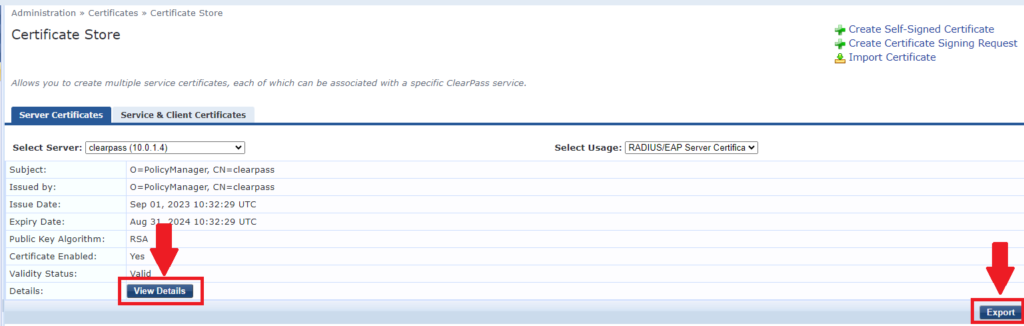
7- If any certificate is about to expire, click on “Create Self-Signed Certificate”
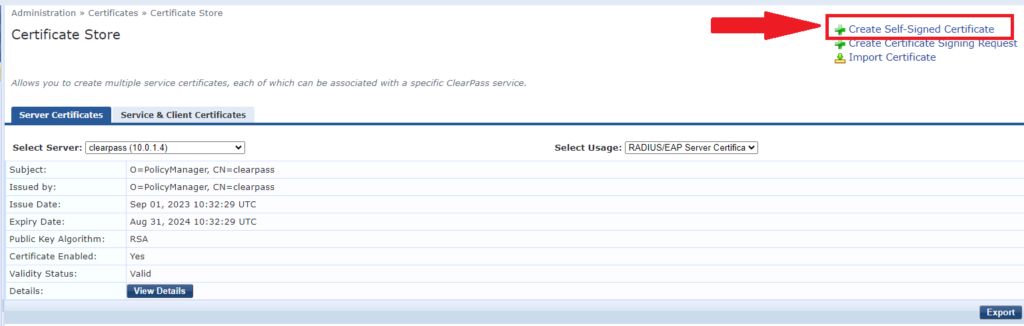
8- Select “Server Certificate”
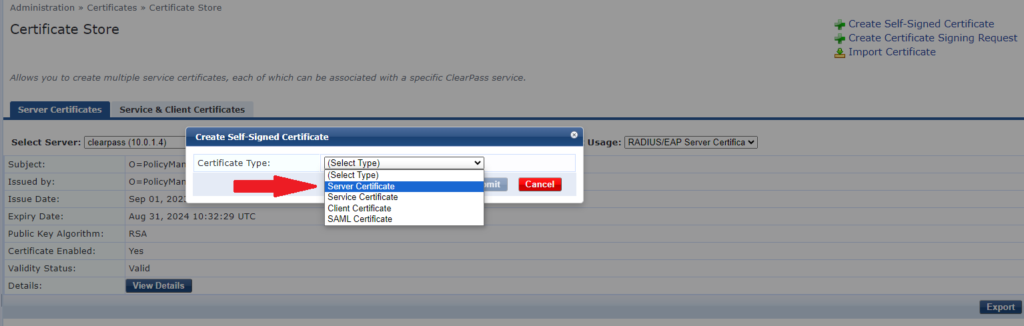
9- Select the server and usage you want and fill the details (you can follow the same values as current certificate or use the values that matches your organization better). Please note:
- You need to provide private key password. You need to take note of this password and store it in a safe place for any future retrieval.
- The maximum number of days of validity is 2000 days
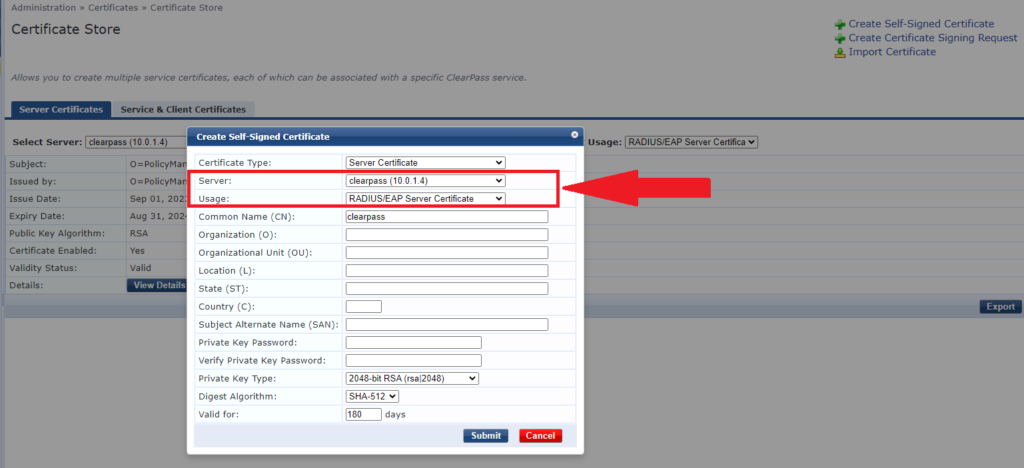
10- After filling all required fields, click on submit.
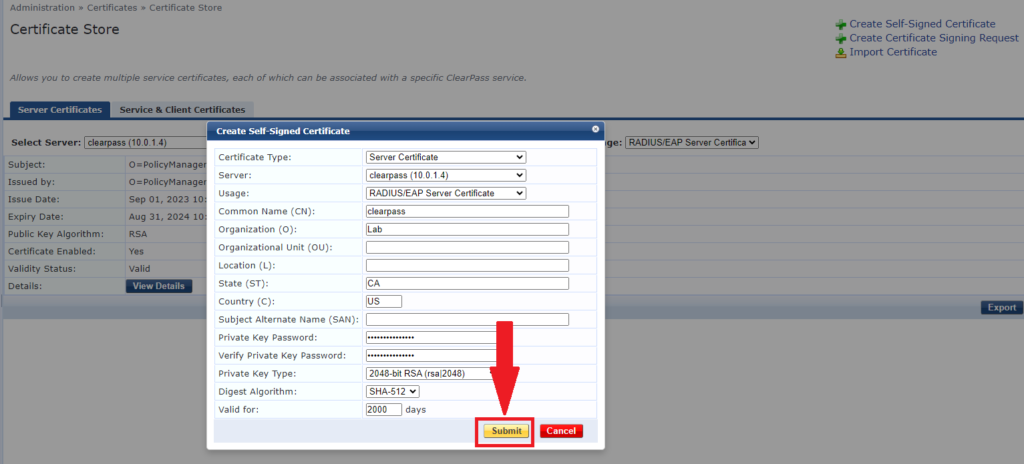
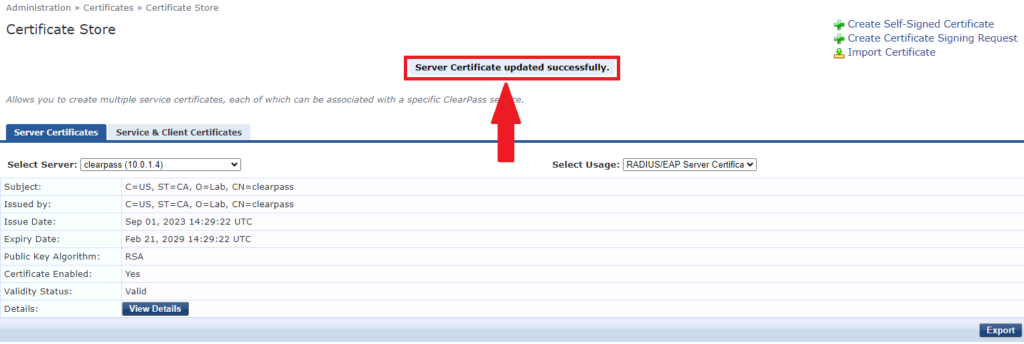
11- Review the new certificate. If all good click on install
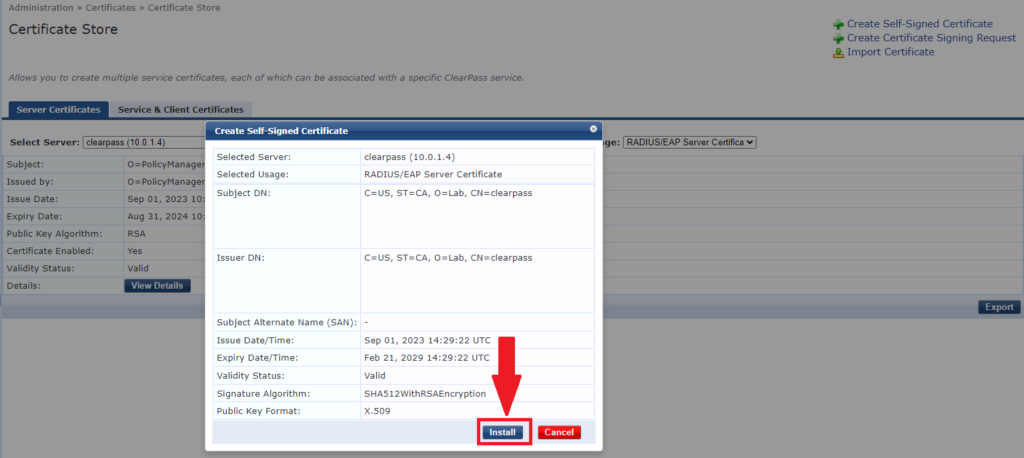
12- Make sure the certificate is updated successfully. Verify new certificate details.