Unlocking the Power of AWS Key Management Service (KMS) Part One

In today’s digital error, robust security solutions are essential as businesses migrate to the cloud. Encryption is essential for protecting sensitive data in transit and at rest. Amazon Web Services (AWS) provides a comprehensive encryption solution with its Key Management Service (KMS). In this article, we’ll explore what AWS KMS is, its features, and how it can enhance your security posture. stay tuned.
What is AWS KMS?
AWS Key Management Service (KMS) is a managed service that makes it easy to create and control the cryptographic keys used to encrypt your data. It integrates with other AWS services to simplify the encryption of your data across AWS.
Key Features of AWS KMS
Centralized Key Management: AWS KMS allows you to manage your encryption keys centrally, giving you full control over their lifecycle. You can create, rotate, disable, and delete keys as needed, all from a single management console.
Integration with AWS Services: KMS is deeply integrated with many AWS services, including Amazon S3, Amazon EBS, Amazon RDS, and AWS Lambda, among others. This integration simplifies the process of encrypting data stored in these services.
Scalability: AWS KMS is built to scale with your needs. Whether you’re managing a handful of keys or thousands, KMS provides the infrastructure to handle your requirements efficiently.
Access Control and Policies: AWS KMS provides fine-grained access control through AWS Identity and Access Management (IAM) policies and KMS-specific key policies. This ensures that only authorized users and services can access your keys.
Audit and Compliance: AWS KMS integrates with AWS CloudTrail to log all key usage and management activities. This audit trail helps you meet compliance requirements and gain visibility into how your keys are being used.
Automatic Key Rotation: To enhance security, AWS KMS supports automatic key rotation. You can set policies to rotate your keys on a regular schedule without disrupting your applications.
How AWS KMS Enhances Security
Data Encryption: At its core, AWS KMS provides the ability to encrypt data using symmetric (AES-256) and asymmetric encryption keys. Symmetric keys are used for a wide range of encryption tasks, while asymmetric keys can be used for tasks like digital signing and key exchange.
KMS Keys
KMS keys are divided into two types of keys.
- Master Key
- Data Key
Master Key: Also known as Customer Master Key (CMK). It is used to generate encrypted data keys so that encrypted keys can be securely stored by your service.
The maximum size of data that can be encrypted using the master key is 4KB. CMK is created within the KMS and cannot leave the KMS console unencrypted.
AWS KMS also supports multi-region CMKs, which let you encrypt the data in one AWS Region and decrypt it in a different AWS Region.
The Customer Master Key itself is classified into three types:
- Customer Managed CMK: In this, you are in full control of creating, managing, and deleting the keys. It provides complete granular-level access control. The responsibility of managing the keys includes creating, granting, and enabling key policies, adding tags, and rotating the key.You are the master of your key.
- AWS Managed CMK: These CMKs are created, managed, and used on your behalf by an AWS service that is integrated with AWS KMS. You can view and track their usage but cannot delete or do modifications.
- AWS-owned CMK:These CMKs are completely owned and managed by AWS for use in multiple AWS accounts. You have no control over them. You cannot view, manage, or use AWS-owned CMKs or audit their use.
Data Key
Data Keys are the encryption keys that you can use to encrypt and decrypt data outside the KMS. It can encrypt and decrypt large volumes of data in other AWS Services such as EBS, S3, EFS, etc. CMK is used to generate, encrypt, and decrypt data keys.
Encryption of Data using KMS
The process of encryption of data using KMS is also known as Envelope Encryption or KMS Two Tier Architecture.
Envelope Encryption

KMS employs a technique known as envelope encryption, where data is encrypted with a data key, which in turn is encrypted with a master key stored in KMS. This approach minimizes the exposure of the master key and enhances security.
Encryption Process
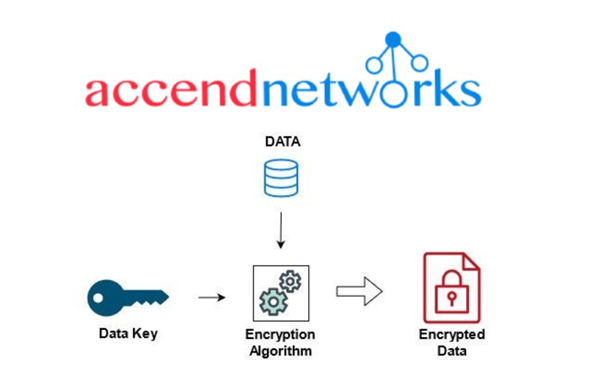
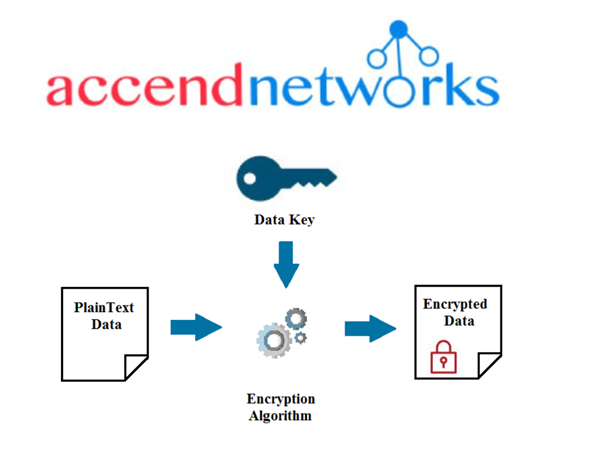
Step: 1 Plaintext data will be encrypted using a data key and result in encrypted data.
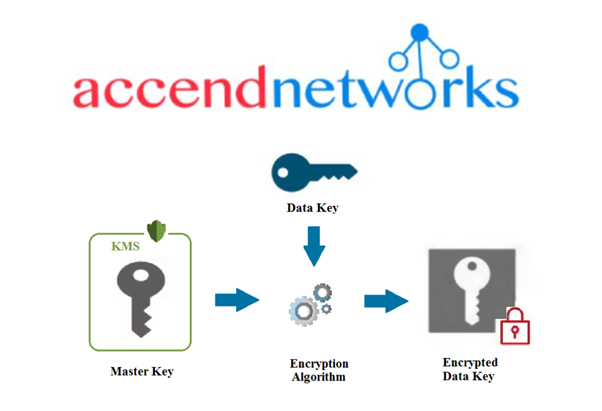
Step: 2 The Data key will be encrypted using a master key (CMK) and result in an encrypted data key.
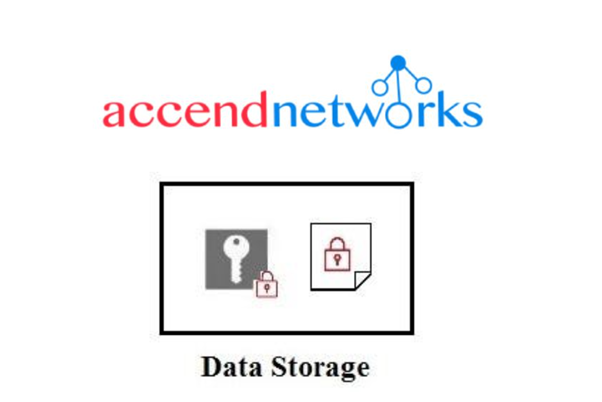
Step: 3 Now encrypted data key is stored together with the encrypted data.
Step: 4 Later, the Data key will be deleted.

Decryption Process
Step: 1 For decryption of data you require a data key which can be obtained by asking the master key to decrypt the encrypted data key.
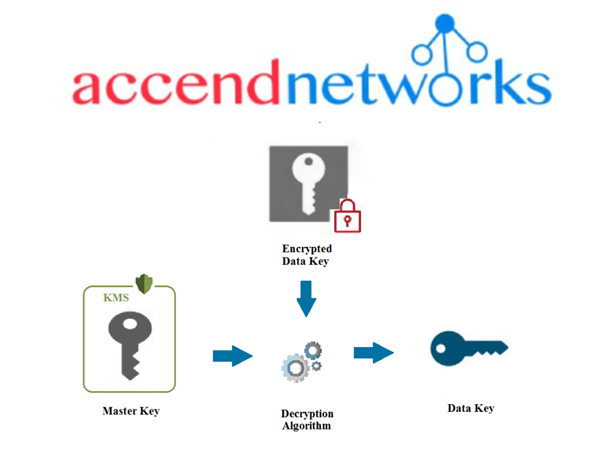
Step: 2 After decryption of the encrypted data key we obtained a data key which is now used to decrypt the data.
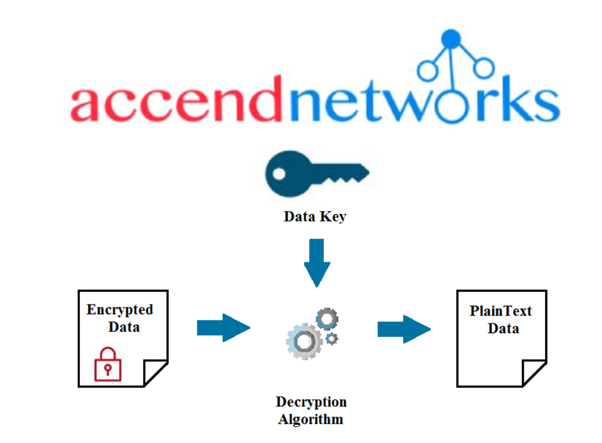
Conclusion
In summary, AWS KMS is a robust tool for managing your encryption keys, enhancing your security posture, and ensuring compliance with industry standards and regulations.
This brings us to the end of this blog, thanks for reading, and stay tuned for more.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com.
Thank you!

Your point of view caught my eye and was very interesting. Thanks. I have a question for you.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me? https://accounts.binance.com/en-NG/register?ref=JHQQKNKN
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Your article helped me a lot, is there any more related content? Thanks!
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Your article helped me a lot, is there any more related content? Thanks!
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article. https://www.binance.com/en/register?ref=JHQQKNKN