How to Store Secrets with Secrets Manager - Part II

Securing secrets is crucial in modern software development, and AWS Secrets Manager serves as a key solution. As a fully managed service from Amazon Web Services (AWS), it effectively safeguards sensitive information, such as API keys and database passwords.
AWS Secrets Manager enables you to centralize and manage access to sensitive data, reducing the risk of unauthorized access. Additionally, it facilitates regular rotation and auditing of secrets, enhancing overall application security. Moreover, its seamless integration with other AWS services simplifies the implementation of security best practices in your infrastructure.
AWS Secrets Manager enables you to centralize and manage access to sensitive data, reducing the risk of unauthorized access. Additionally, it facilitates regular rotation and auditing of secrets, enhancing overall application security. Moreover, its seamless integration with other AWS services simplifies the implementation of security best practices in your infrastructure.
Task: Creating an RDS Database, Managing Credentials with Secrets Manager, and Auditing with CloudTrail.
We will embark on this task by first creating an RDS Database, ensuring seamless management of credentials through Secrets Manager. Subsequently, dive into auditing processes with CloudTrail to maintain a comprehensive and secure AWS environment.
a) Sign in to AWS Management Console and create an RDS MySQL instance.
b) Store a new secret.
c) Verify the secret created.
d) Using cloud trail to monitor secret manager activities.
We will embark on this task by first creating an RDS Database, ensuring seamless management of credentials through Secrets Manager. Subsequently, dive into auditing processes with CloudTrail to maintain a comprehensive and secure AWS environment.
a) Sign in to AWS Management Console and create an RDS MySQL instance.
b) Store a new secret.
c) Verify the secret created.
d) Using cloud trail to monitor secret manager activities.
Hands-on:
a) Sign in to AWS Management Console and create an RDS MySQL instance.
Log into the AWS management console and in the search box, type RDS then select RDS under services.
Log into the AWS management console and in the search box, type RDS then select RDS under services.
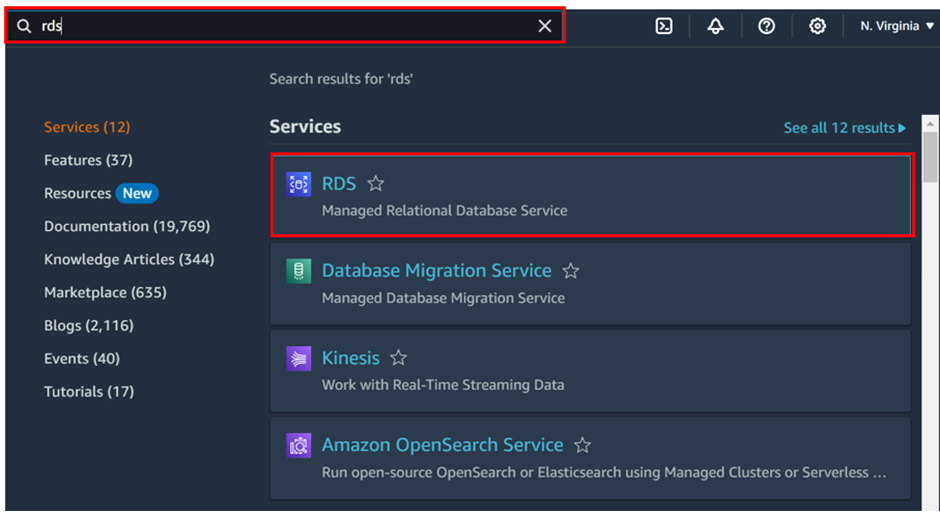
In the RDS console, click on Create Database.
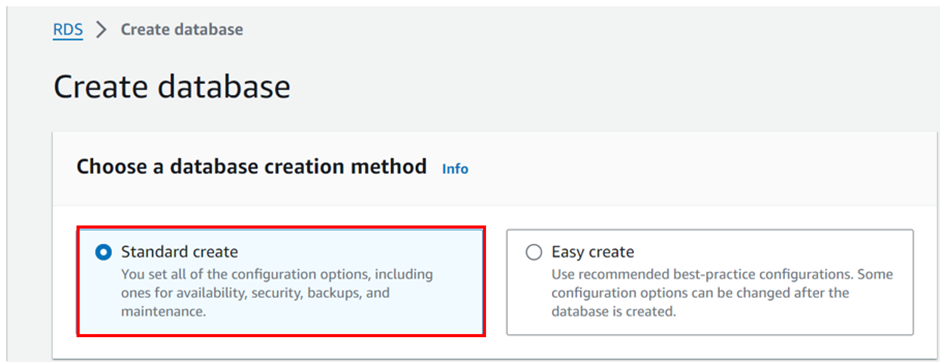
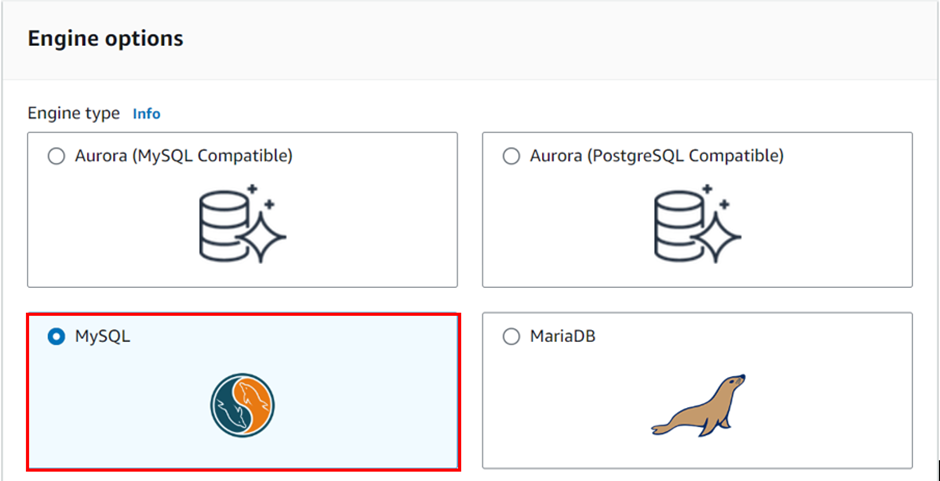
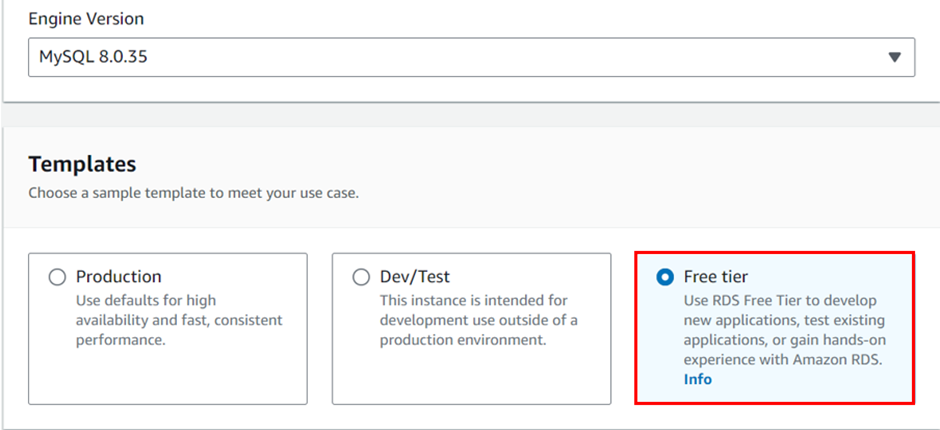
In the Create database screen, select the following:
Choose a database creation method: Standard create
Engine type: MySQL
Templates: free tier
In the Create database screen, select the following:
Choose a database creation method: Standard create
Engine type: MySQL
Templates: free tier
In the settings and DB instance class tab, fill in the details as follows:
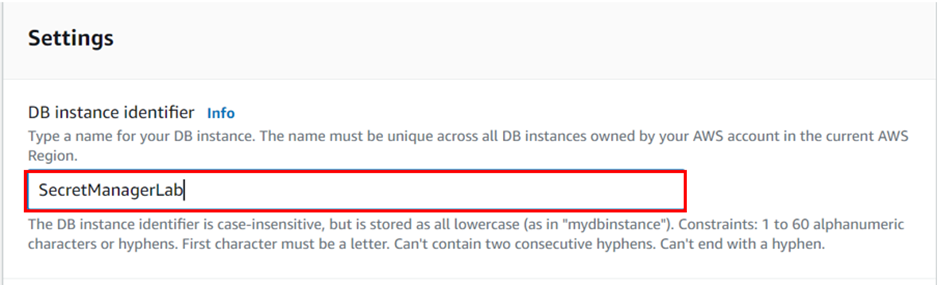
DB instance identifier: SecretManagerLab (any name)
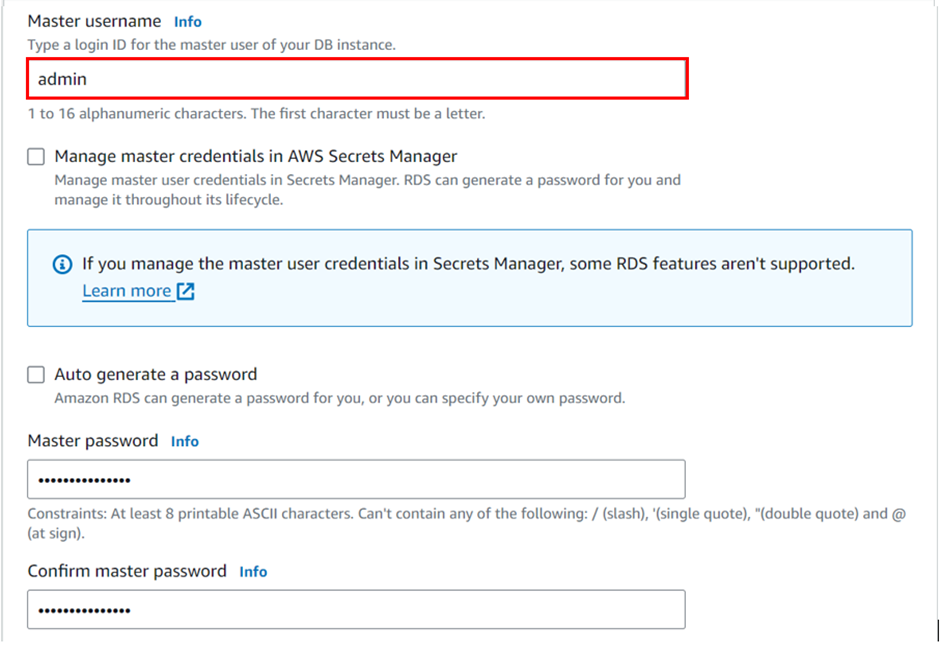
Master username: admin (any username for your database instance)
Master password: dcVRBrxLbhacVU6 (any password for your instance)
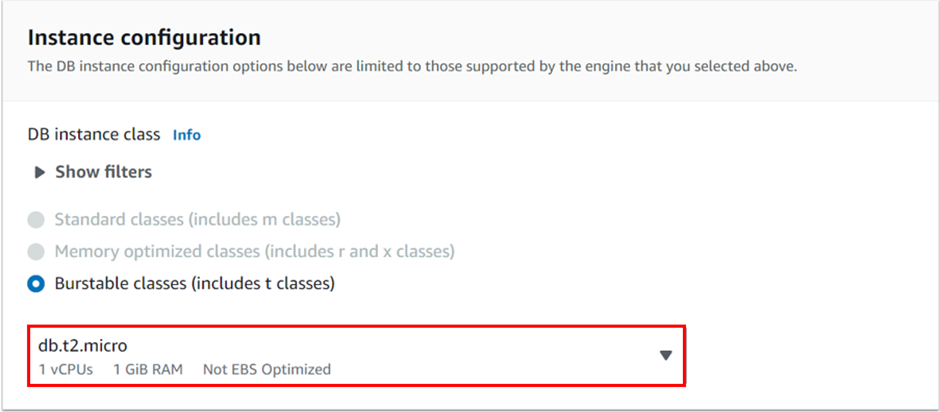
DB instance class: db.t2. micro
Note: Make sure to remember the username and password or simply paste in a text file.
DB instance identifier: SecretManagerLab (any name)
Master username: admin (any username for your database instance)
Master password: dcVRBrxLbhacVU6 (any password for your instance)
DB instance class: db.t2. micro
Note: Make sure to remember the username and password or simply paste in a text file.
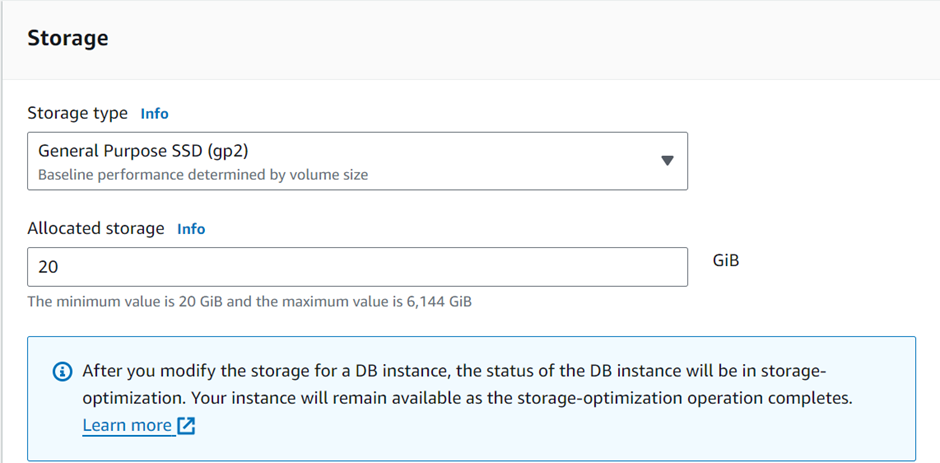
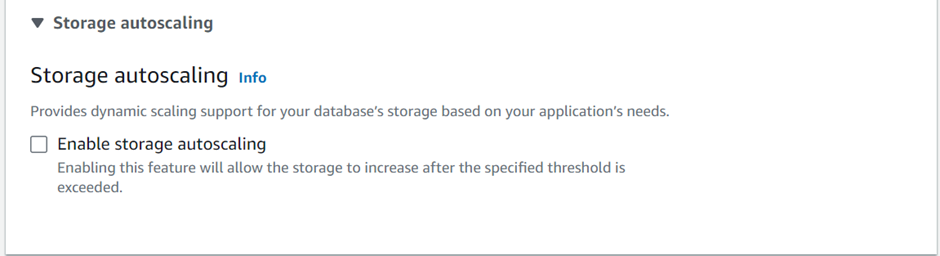
In the Storage tab, keep everything as default and make sure to undo the checkbox for Enable storage autoscaling.
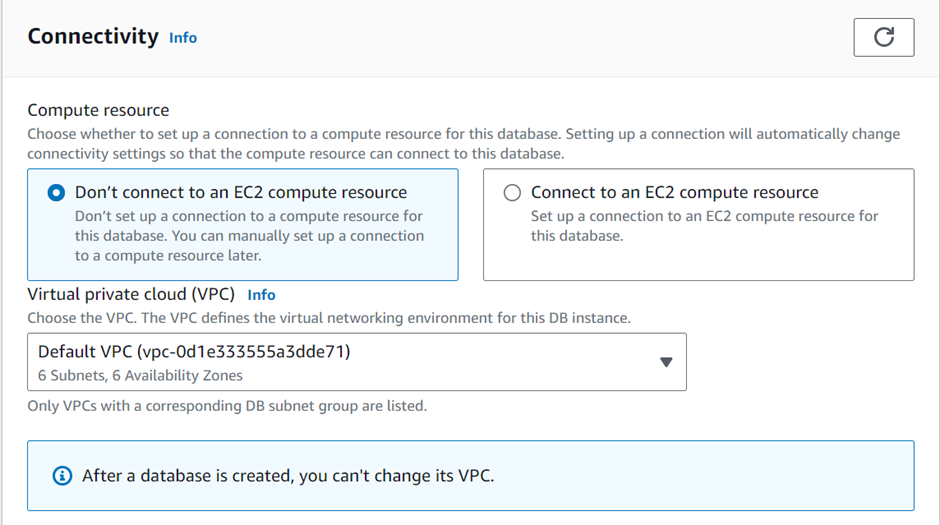
In the connectivity tab, make sure that the public access is set to No.
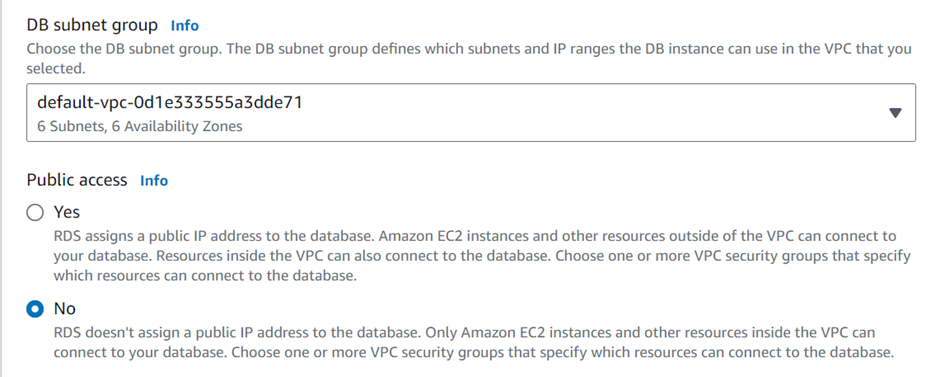
Keep everything else as default. After this click Create Database.
It takes some time for your database to be created.
We’ve created an RDS MySQL instance successfully!
It takes some time for your database to be created.
We’ve created an RDS MySQL instance successfully!
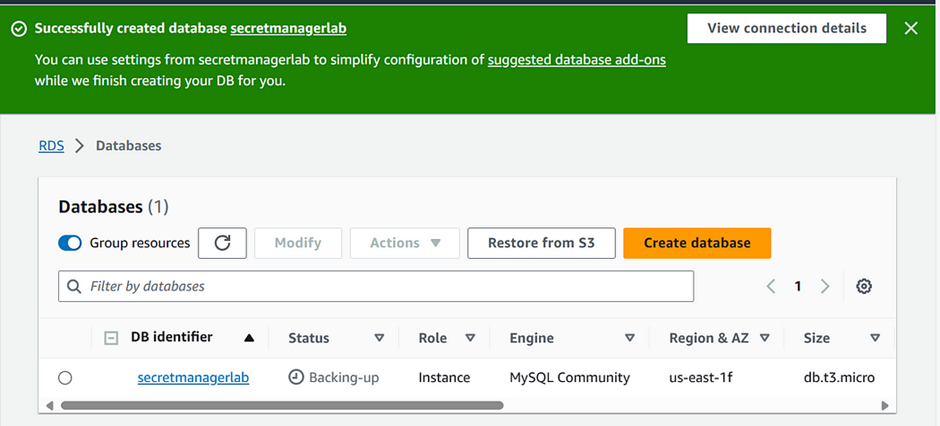
b) Store a new secret.
In the search box, type secrets manager and select secrets manager under services.
In the search box, type secrets manager and select secrets manager under services.
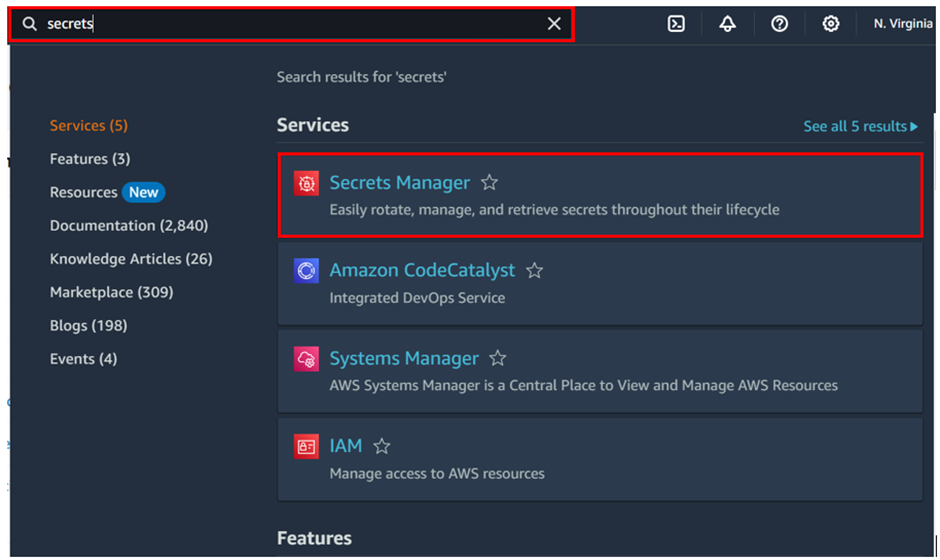
In the AWS Secret Manager dashboard, click on Store a new secret.

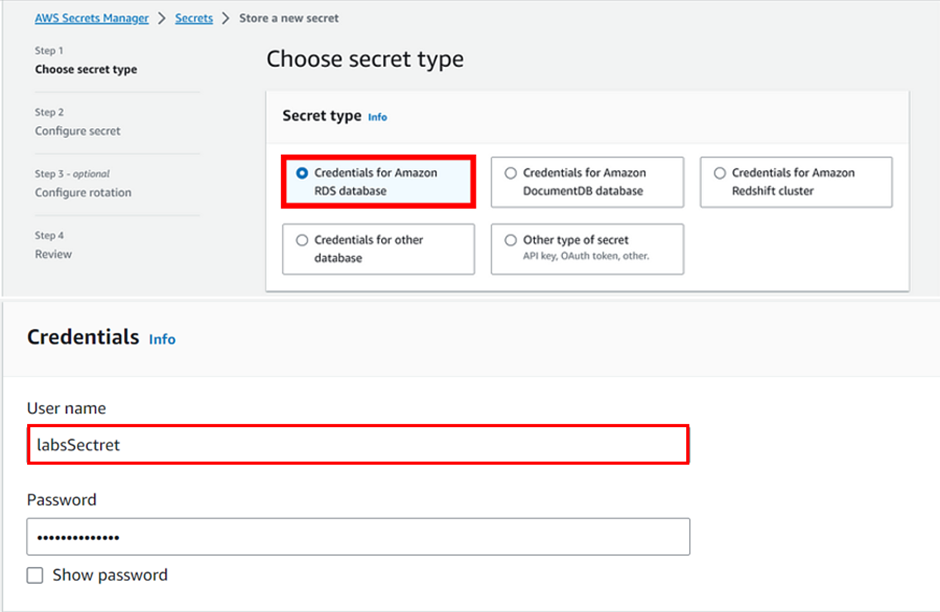
Now in Secret type, please select Credentials for Amazon RDS database and enter the following details:
User name: (username of our database instance, here we used admin)
Password: (password of our db instance, here we used dcVRBrxLbhacVU6)
Encryption key: (keep it as default)
User name: (username of our database instance, here we used admin)
Password: (password of our db instance, here we used dcVRBrxLbhacVU6)
Encryption key: (keep it as default)
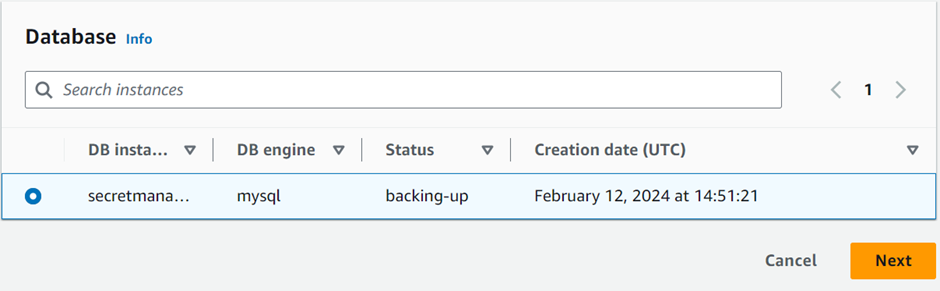
Select the database instance you created in the previous step, (named SecretManagerLab) and click next.
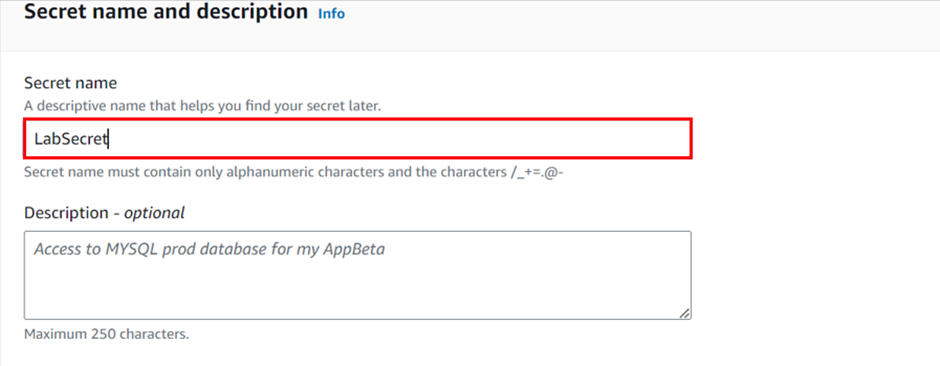
On the next screen, give the Secret name as any name (LabSecret ) and keep everything else as default. Click next.
Secret ‘LabsSecret’ has been stored, with Secret Manager.
Secret ‘LabsSecret’ has been stored, with Secret Manager.
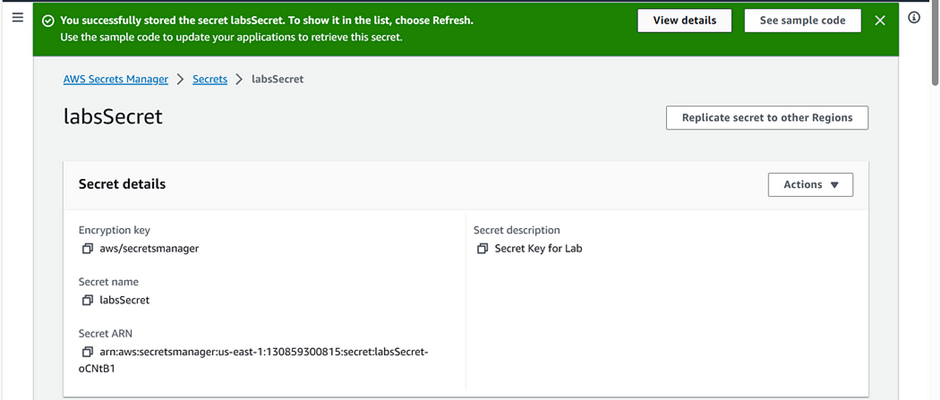
c) Verify the secret created.
Once the secret is created and rotation is configured click on the secret name [LabsSecret]
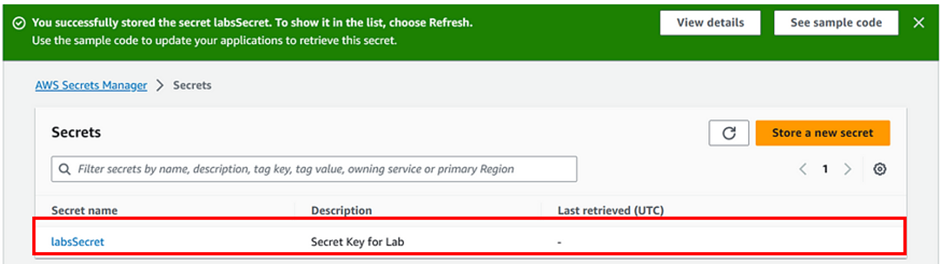
Now click on the Retrieve secret value button
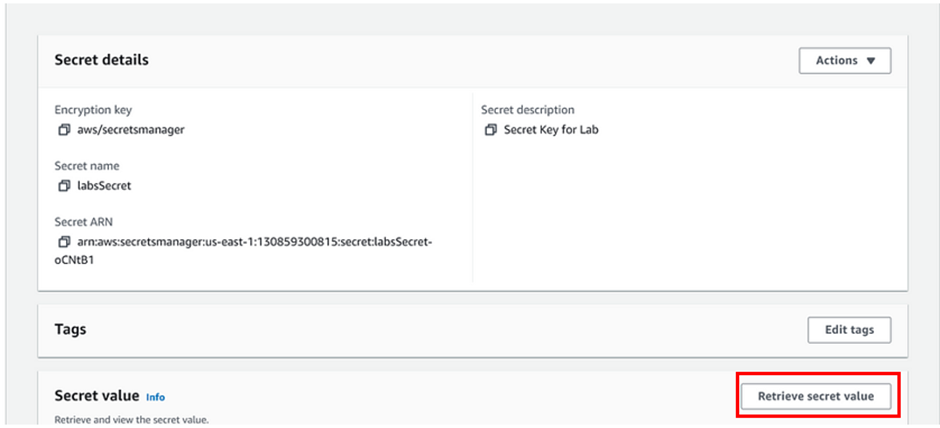
We can see the details of our secret value including the password.
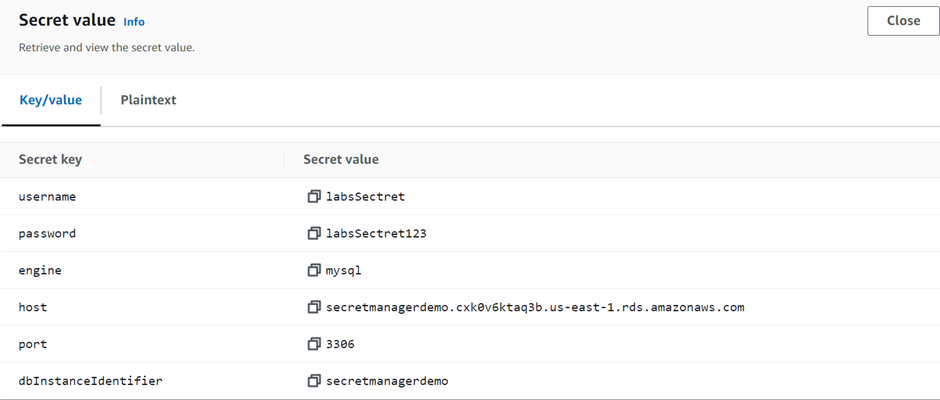
d) Using cloud trail to monitor secret manager activities.
Search for CloudTrail in the search then select it under services.
Search for CloudTrail in the search then select it under services.
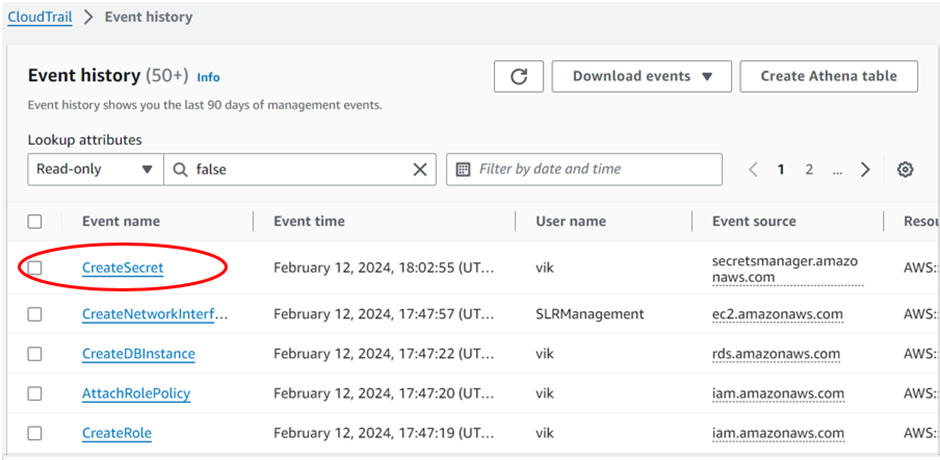
In the lookup attributes, select Event name and Enter event name as GetSecretValue.
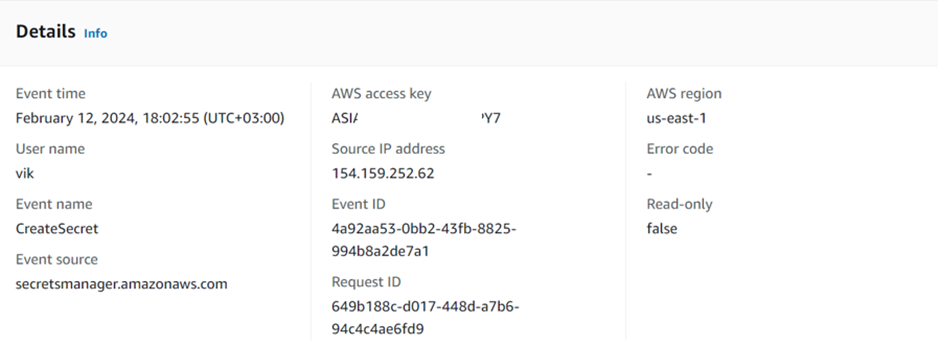
You can see the user’s name of all the users who tried to access the secret and the event time.
You can see the user’s name of all the users who tried to access the secret and the event time.
AWS Secrets Manager is a service provided by Amazon Web Services (AWS) that helps you manage and protect sensitive information such as passwords, API keys, and other credentials. It allows you to securely store, access, and rotate these secrets, reducing the risk of unauthorized access and improving overall security for your applications and services.
AWS CloudTrail is an AWS service that helps you enable operational and risk auditing, governance, and compliance of your AWS account. Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail.
This brings us to the end of this demo. Make sure to pull down everything.
If you have any questions concerning this article or have an AWS project that requires our assistance, please leave a comment below or email us at sales@accendnetworks.com.
Thank you!
AWS CloudTrail is an AWS service that helps you enable operational and risk auditing, governance, and compliance of your AWS account. Actions taken by a user, role, or an AWS service are recorded as events in CloudTrail.
This brings us to the end of this demo. Make sure to pull down everything.
If you have any questions concerning this article or have an AWS project that requires our assistance, please leave a comment below or email us at sales@accendnetworks.com.
Thank you!

Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
I don’t think the title of your article matches the content lol. Just kidding, mainly because I had some doubts after reading the article.