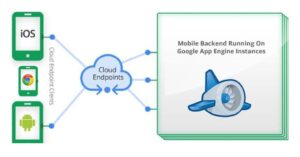
Apple iOS, Androids, Apple iPAD, Chromebooks, and other tablets are the common Google cloud endpoints found today. Servers, laptops, and desktops are also cloud endpoints because they access the same cloud environment, but users tend to think differently.
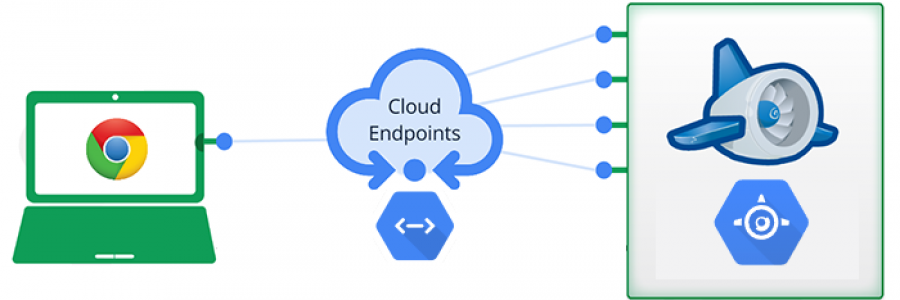
Below is an example of cloud endpoints connecting to a Google cloud-based computing environment :
We have helped many clients with cloud services such as deploying and configuring Palo Alto Networks’ Prisma SaaS, formerly Aperture, building a virtual private cloud (VPC) from their on-premise gateways to a cloud platform on Microsoft Azure or Amazon AWS, setting up and configuring different Meraki appliances such as cloud-based firewalls, routers, switches, and access points, and migrating emails from different hosting platforms to Google Suite for Business Enterprise.
Part of the above projects above include configuring and ensuring that the cloud endpoints are able to access the new environment. In the case of a Google cloud platform such as Google Suite, the endpoints need to be configured with a proper setting to secure access to the Google cloud-based email. Each user account is created with a unique email ID and password. Customers are advised to enable two-factor authentication, which is now mandated by the Google cloud computing team.
Microsoft Azure, Amazon AWS, and Google Cloud are the top three cloud providers. A cloud computing environment such as the one from Google cloud enables users to quickly set up their new infrastructure and provides a cheaper solution as well. Administer can manage the configuration panel through the Google cloud console, which can be accessed by any cloud endpoint that can access the Google environment. This often usually only requires the administer to have internet access, along with an administrative credential.
Clients should be aware that security is critical when cloud endpoints connect to the cloud- based platform, as such Google cloud, to avoid any unwanted intrusion. They should take note of enabling two-factor authentication, a long and unique password (choosing a password that is different from other applications), changing the password often and/or as required by the client’s compliance regulation, and have their security policy checked and configured. This is something our security consultant can help with, especially if the client wishes another pair of eyes to check that the settings are configured correctly.
Another request we’re getting is configuring and installing the Google Cloud Anthos GKE. This is hosted on the Google Cloud computing environment. Anthos GKE is a hybrid cloud software that allows interconnectivity between Google Kubernetes Engine (GKE) to an on-premises data center. After the installation of GKE on-prem, the client can then use Google Connect to view and sign into their on-premises and on-cloud Kubernetes clusters from the same interface as Google Cloud Console. This project is a fairly complex setup as different stages are needed, and strict network requirements need to be in place for the GKE environment to work properly.
Ease of use and mobility are the top two reasons for which clients move to a cloud environment. They can access the new environment using a variety of cloud endpoints available today.
We have certified Google consultants on staff to help our clients with their cloud projects. It could be an email migration project, spinning up a new virtualized environment, assessing a current security setup, and configuring access for different cloud endpoints. The cloud environment can be located in California or anywhere throughout the United States.
We can help customers with subscribing to the different cloud services that Google provides or just use our service after purchases have been made.
Reach out to us today at 408-784-2345 local or 855-8ACCEND national to have a specialized cloud expert get back to you about your cloud project.
