How To Monitor AWS API Activity with AWS CloudTrail

AWS CloudTrail is a service that enables governance, compliance, operational auditing, and risk auditing of your AWS account. AWS CloudTrail is a service that you can use to capture information about the API actions happening in your AWS account, AWS SDKs, command line tools, and other AWS services.
What is CloudTrail?
CloudTrail continuously monitors and logs account activity across all AWS services, including actions taken by a user, role, or AWS service. The recorded information includes the identity of the API caller, the time of the API call, the source IP address of the API caller, the request parameters, and the response elements returned by the AWS service.
Why Use CloudTrail?
Here are some key reasons to use CloudTrail:
Audit Compliance: CloudTrail logs provide detailed records of all API calls, which can be used to audit compliance.
Security Analysis: The API call logs can be analyzed to detect anomalous activity and unauthorized access to determine security issues.
Operational Issues: The activity history can help troubleshoot operational issues by pinpointing when an issue began and what actions were taken.
Resource Changes: You can identify what changes were made to AWS resources by viewing CloudTrail events.
CloudTrail Log Files
CloudTrail log files contain the history of API calls made on your account. These log files are stored in Amazon S3 buckets that you specify. You can define S3 buckets per region or use the same bucket for all regions.
The log files capture API activity from all Regions and are delivered every 5 minutes. You can easily search and analyze the logs using Amazon Athena, Amazon Elasticsearch, and other tools.
The log files capture API activity from all Regions and are delivered every 5 minutes. You can easily search and analyze the logs using Amazon Athena, Amazon Elasticsearch, and other tools.
CloudTrail Events
CloudTrail categorizes events into two types:
Management events
Provides information about management operations performed on resources in your AWS account. These include operations like creating, modifying, and deleting resources.
Data events
Provides information about resource operations performed on or in a resource. These include operations like Amazon S3 object-level API activity.
By default, AWS logs and retains management events for a period of 90 days. but this timeframe might need to be revised for your requirements. To overcome this, you can create a CloudTrail trail, enabling you to log events in S3 for indefinite retention. Each trail you create can be region-specific or it can be applied to all regions. Furthermore, you can leverage CloudWatch events to trigger actions based on API calls that are made and logged in CloudTrail.
By default, AWS logs and retains management events for a period of 90 days. but this timeframe might need to be revised for your requirements. To overcome this, you can create a CloudTrail trail, enabling you to log events in S3 for indefinite retention. Each trail you create can be region-specific or it can be applied to all regions. Furthermore, you can leverage CloudWatch events to trigger actions based on API calls that are made and logged in CloudTrail.
Using information generated by CloudTrail.
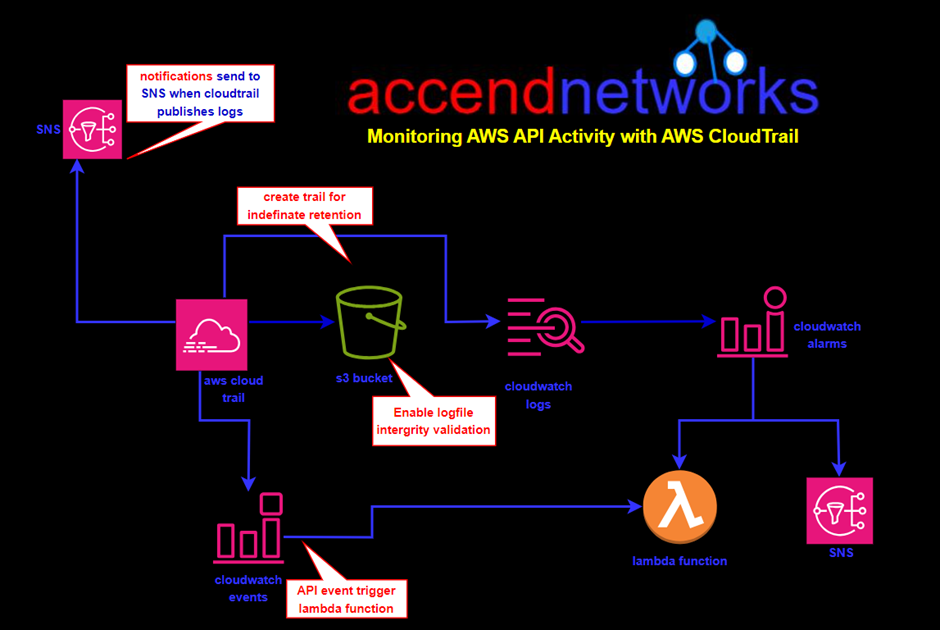
In the above architecture, we have AWS CloudTrail that will log API actions for 90 days. We can then choose to create a trail and log our events to Amazon S3 indefinitely. Furthermore, we can also enable log file integrity validation. This checks whether the events that are being logged have been tampered with or not, hence ensuring the accuracy of logged events for auditing and compliance since we need to ensure that the information is accurate and has not been modified. Additionally, we can also trigger notifications through SNS topics upon log file publication. We can also forward data to CloudWatch logs, enabling actions like setting alarms or using subscription filters. Alarms triggered by CloudWatch logs can execute Lambda functions or notify through SNS topics. Again, forwarding information to CloudWatch Events can trigger Lambda functions based on API actions. So, we see there are lots of ways we can use the information generated by CloudTrail.
Hands-on creation of CloudTrail trail.
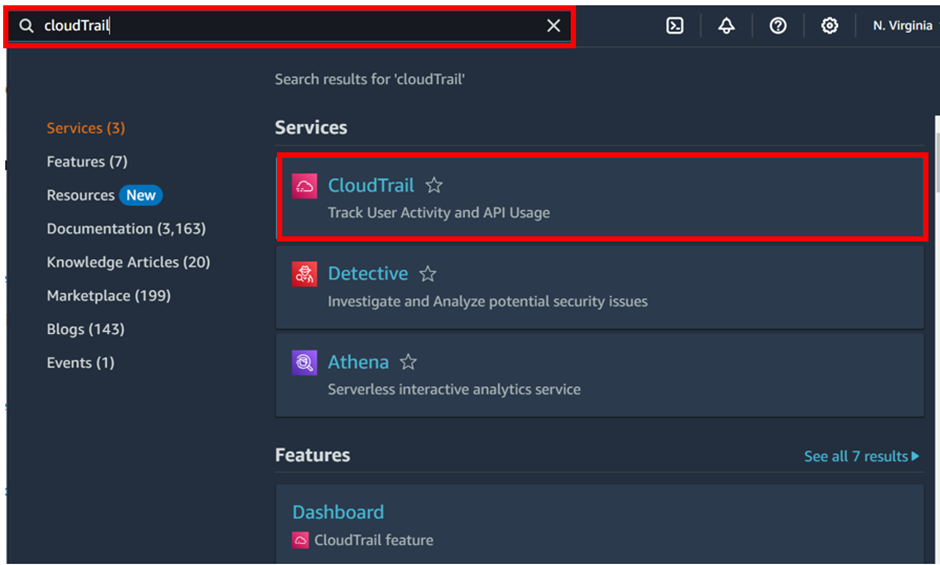
Log into the management console then in the search box under services, type CloudTrail, then select CloudTrail under services.
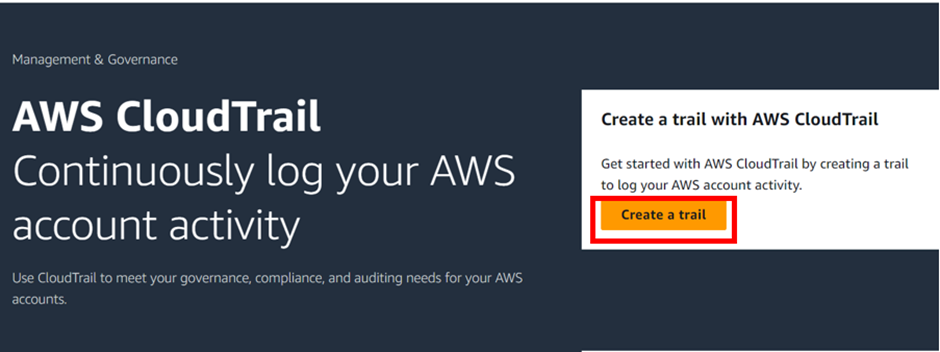
In the CloudTrail dashboard click Create a Trail.
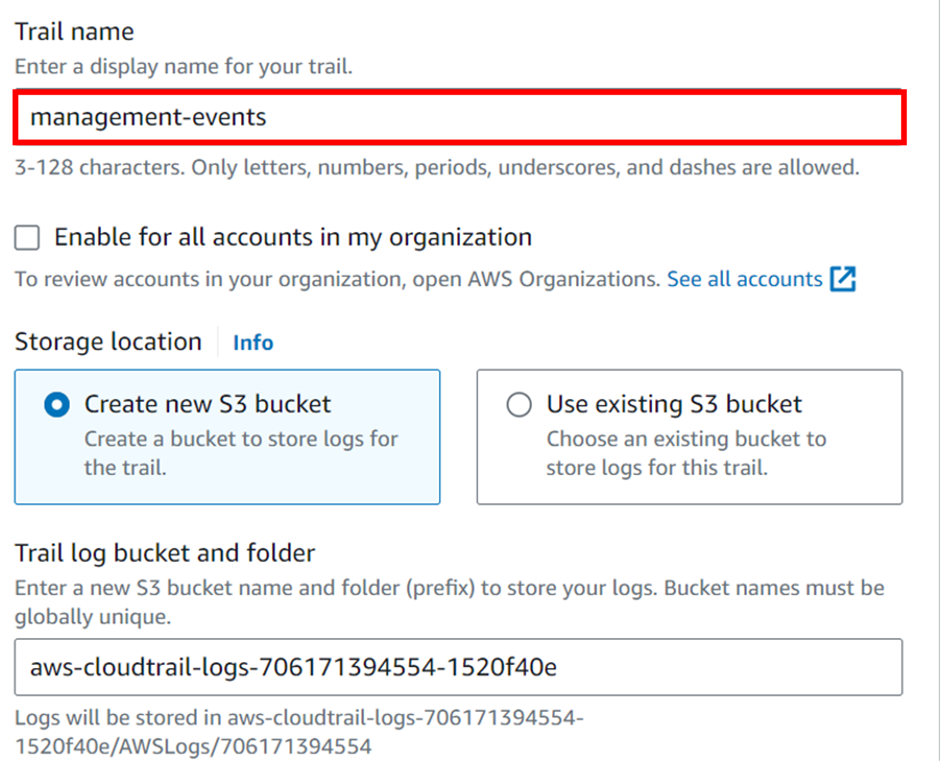
Under trail name, give it a name and call it management events. We will create this trail only for this account so we will not tick the box for enable for all accounts in my organization.
It’s going to need a storage location, and by default, it will create an S3 bucket. And give it a unique name. So, we will leave that as the default.
It’s going to need a storage location, and by default, it will create an S3 bucket. And give it a unique name. So, we will leave that as the default.
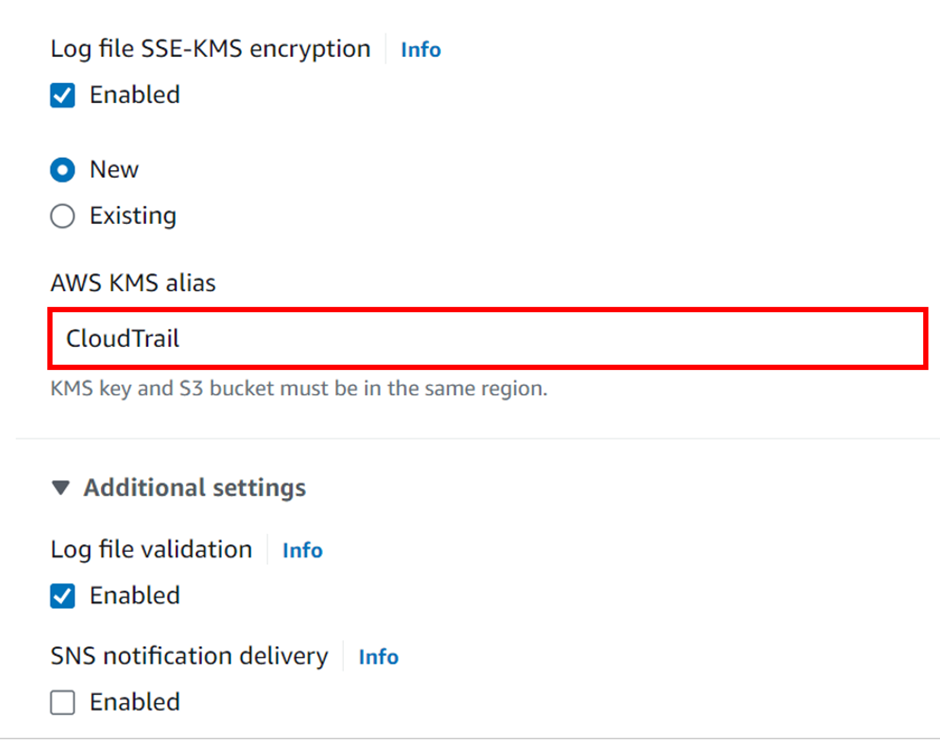
To encrypt the information in your bucket select the new key and call it CloudTrail.
Logfile validation is enabled by default Scroll down.
Logfile validation is enabled by default Scroll down.
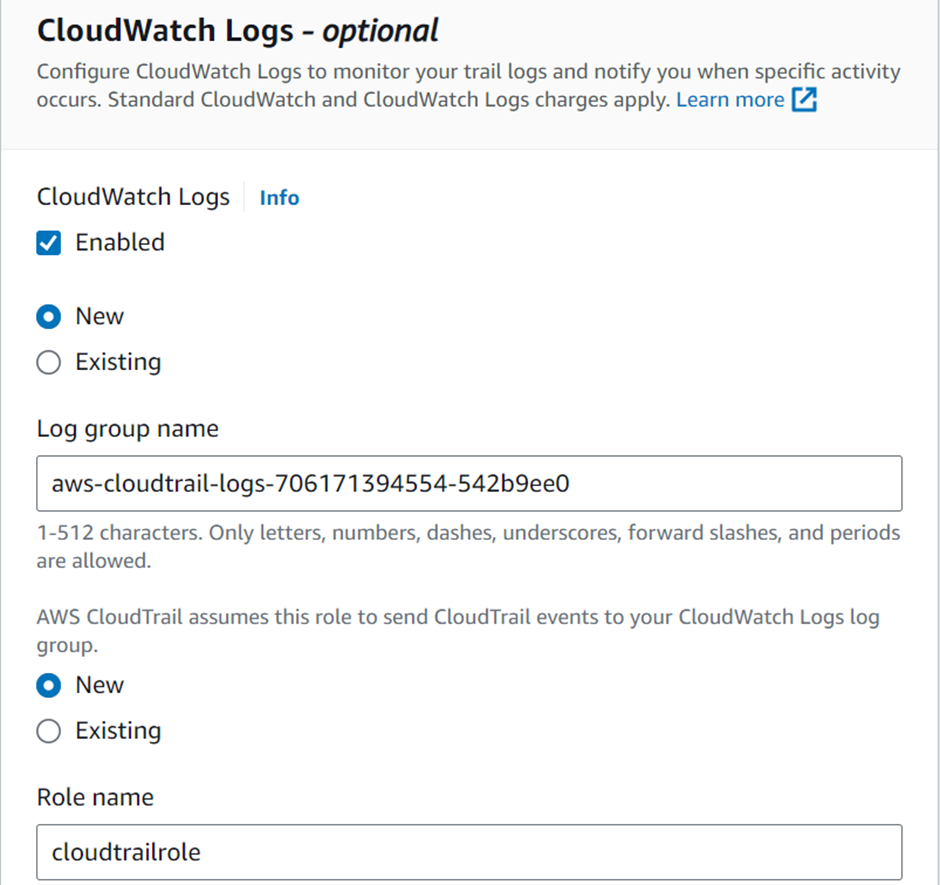
Under CloudWatch, enable it. CloudTrail will need a role to send a trail to CloudWatch so select a new role and give it a name then scroll down and click next.
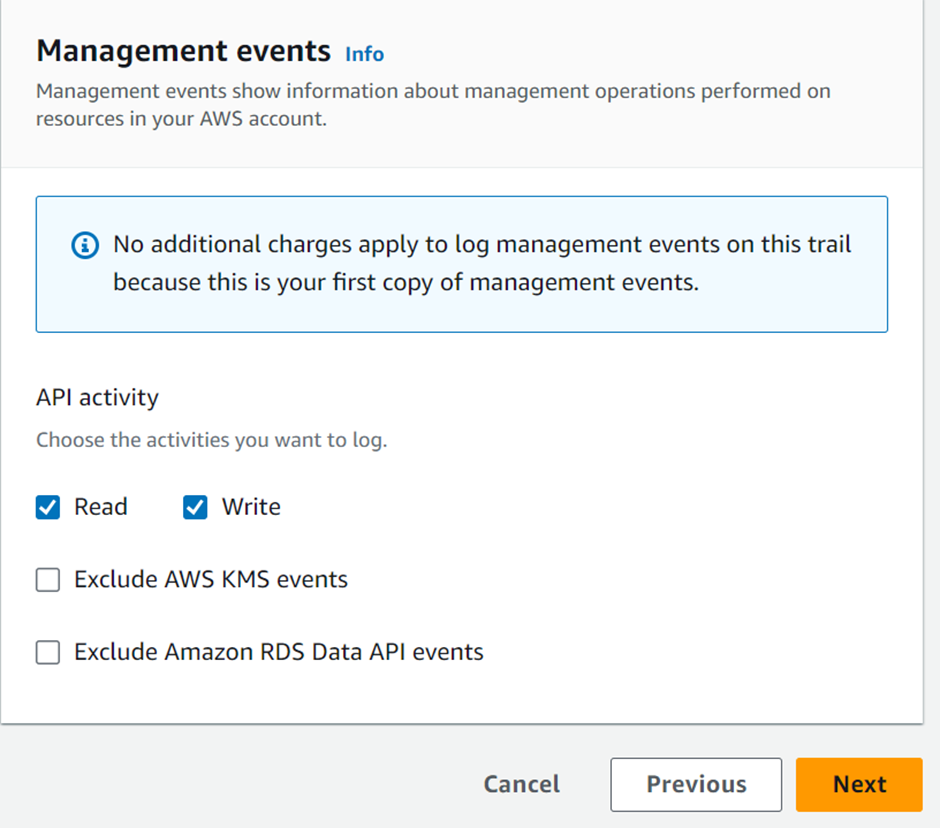
Under the type of event, we will move with the management events.
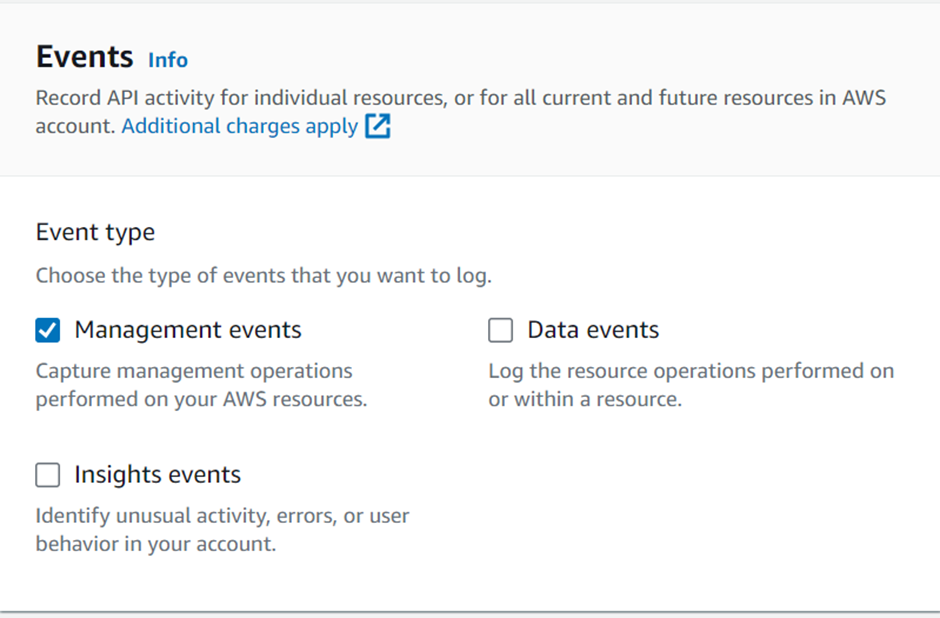
API activity will be read and write then click next, review and click create a trail.
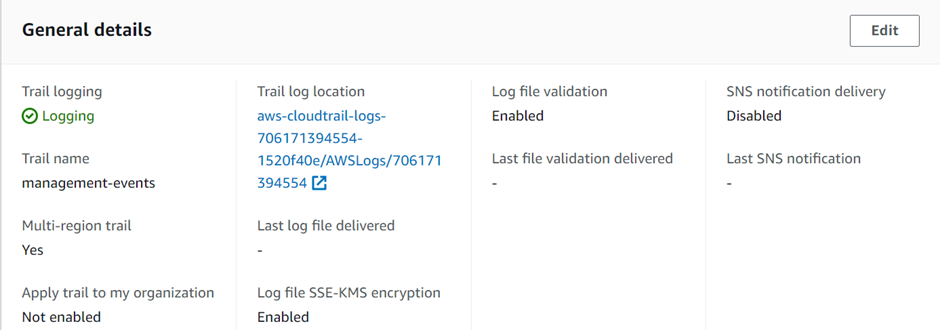
We have successfully created a trail and we can see its status is logging.
This brings us to the end of this blog. Cleanup.
Stay tuned for more.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at [email protected].
Thank you!
