Protecting Applications with AWS Shield
DDoS (Distributed Denial of Service) attacks are still a big threat to online businesses. Attackers use millions of tonnes of traffic to bring down a victim’s web applications from multiple sources.
What is AWS Shield?
AWS Shield is a managed solution for preventing DDoS attacks basically on AWS-hosted applications. It inspects traffic in real-time and applies mitigation strategies automatically in order to avoid performance degradation.
Meanwhile, it inspects incoming requests fast and blocks harmful traffic using a multivariate method (based on traffic signatures, anomaly algorithms, packet filtering, and other techniques).
Types of AWS Shields:
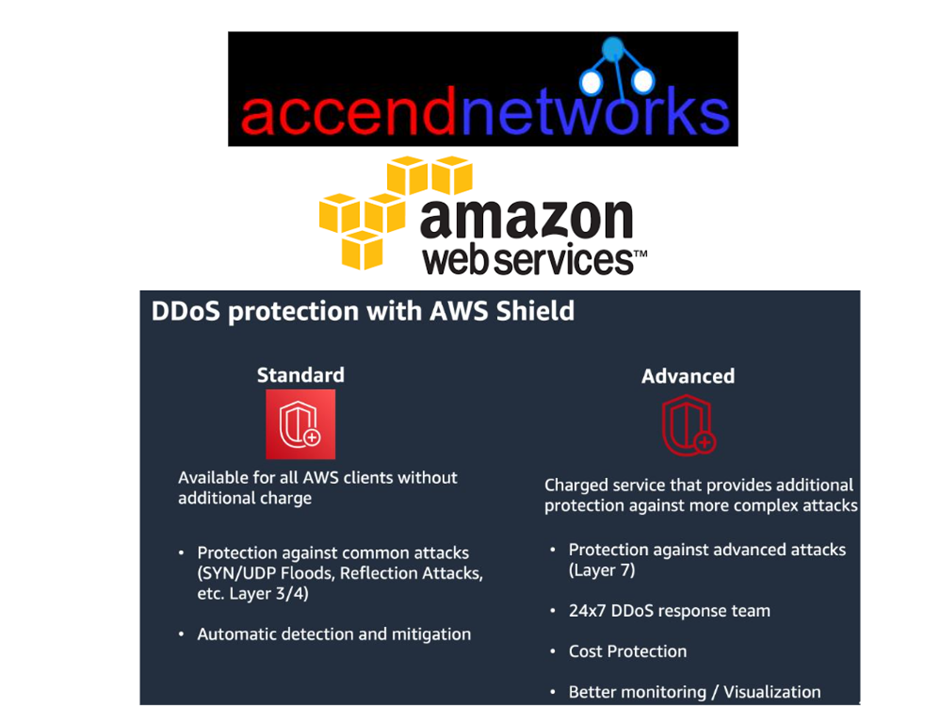
AWS Shield Standard (Free Service)
It is a free service offered to all AWS customers. It guards you against 96% of today’s most prevalent attacks, such as SYN/ACK floods, Reflection attacks, and HTTP slow reads.
AWS Shield Advanced (Paid Service)
It is a paid service that adds volumetric DDoS mitigation, sophisticated attack detection, and mitigation for attacks at the application as well as network layers to AWS Shield.
You also have access to DDoS Response Team (DRT) 24*7 for tailored mitigation during attacks.
How does AWS Shield Work?
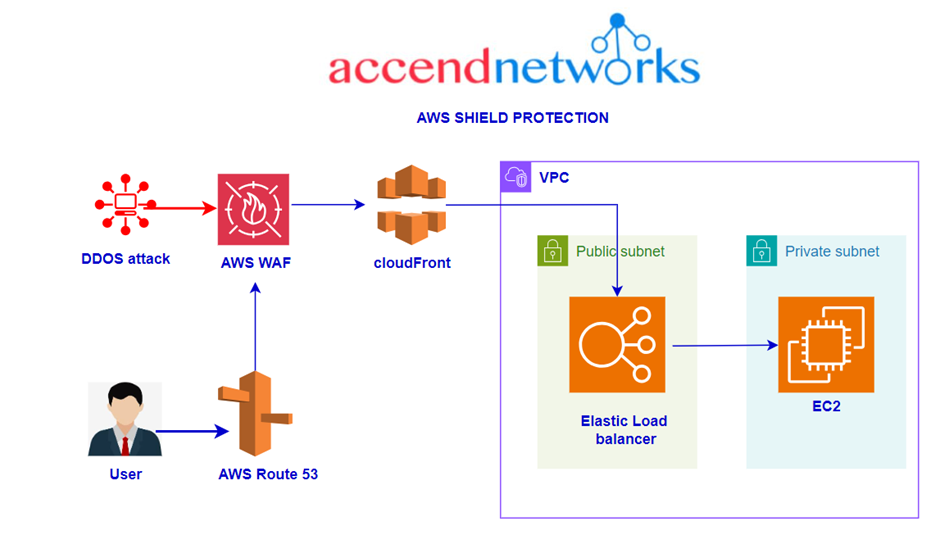
At the network and transport layers as well as the application layer, AWS Shield Standard and AWS Shield Advanced provide protection against DDoS attacks on resources.
Meanwhile, it provides automatic protection to all customers who use services like Amazon CloudFront, Amazon Route 53, and Elastic Load Balancer at no additional cost.
It enables organizations to build custom web access control lists (web ACLs) that can include traffic inspection conditions that become rules. There is a corresponding action for each rule (allow, block, or count).
The count mode can assist organizations in observing traffic patterns and determining whether to implement a given rule in allow or block mode.
The rate-limiting feature is one of the clearest examples of this. If an IP address receives more than two thousand requests in a five-minute period, it will be automatically blocked using this feature.
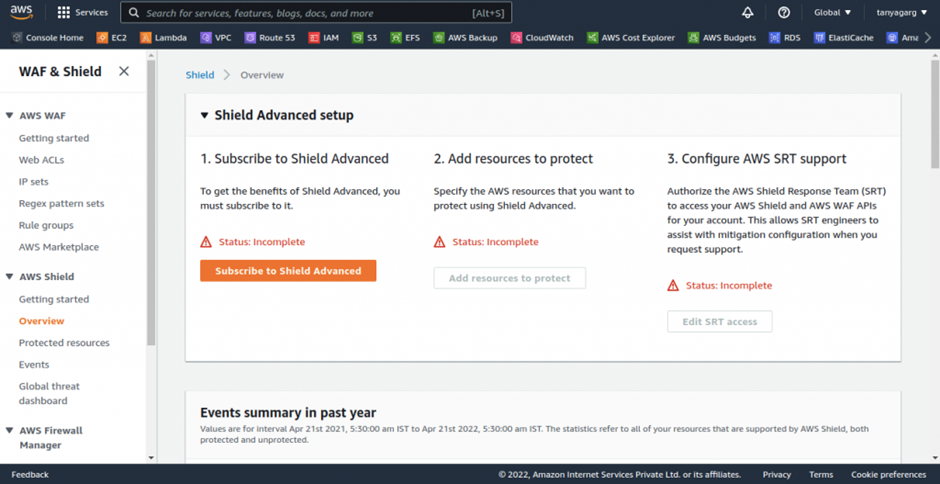
How To Setup AWS Shield
follow these steps in order to configure AWS Shield to your AWS account.
Sign in to the AWS Console. In the search box, type shield then select WAF and Shield under services.
In the left side of the navigation pane Under Shield, click on ‘Getting started’.

you will be brought to the AWS shield dashboard, then on the right side of the dashboard under Get started with shield advanced, click subscribe to shield advance.
In order to Subscribe to AWS, Shield Advanced, we need to accept all the terms & conditions.
Check all checkboxes to proceed further and then click on the ‘Subscribe’ button.

As a result, we have successfully subscribed to Advanced protection.
Now, we can proceed further ‘Add resources to Protect’.

Now, click on ‘Add resources to Protect’ to add resources.

Here, we can choose the Region and then can choose the Resource type that you want to protect and can click on Load more resources to add other resources.

NOTE: Membership alone does not grant access to all of the features, such as the AWS SRT (Shield Response Team), which can provide immediate support during an assault (including proactive event response, i.e. they will start to mitigate the attack as soon as they notice it). You must sign up for Enterprise or Business support to further receive SRT help.
This brings us to the end of this blog, thanks for reading and stay tuned for more.
Conclusion
AWS Shield stands as a critical component in the range of tools and services available to businesses and organizations seeking robust protection against Distributed Denial of Service (DDoS) attacks. By leveraging AWS Shield’s advanced capabilities, businesses can fortify their defences, mitigate potential disruptions, and maintain the integrity and availability of their applications and data in the face of evolving cyber threats.
If you have any questions concerning this article or have an AWS project that requires our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com.
Thank you

Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Thank you for your sharing. I am worried that I lack creative ideas. It is your article that makes me full of hope. Thank you. But, I have a question, can you help me?
Thanks for sharing. I read many of your blog posts, cool, your blog is very good.
Can you be more specific about the content of your article? After reading it, I still have some doubts. Hope you can help me.
Your article helped me a lot, is there any more related content? Thanks!