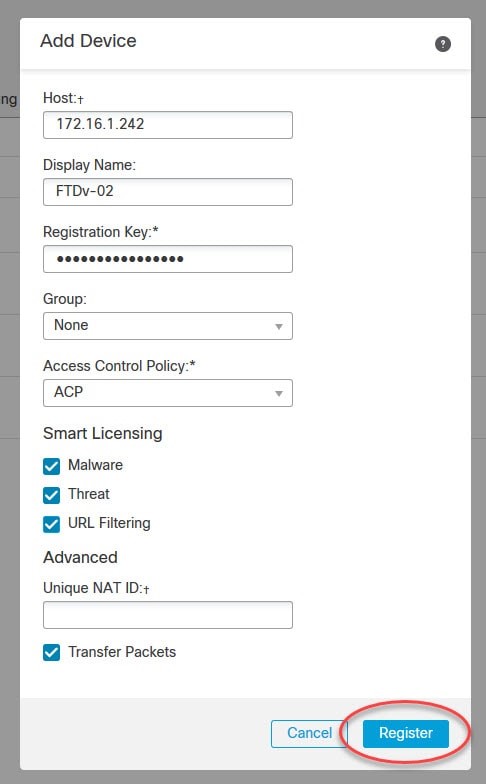
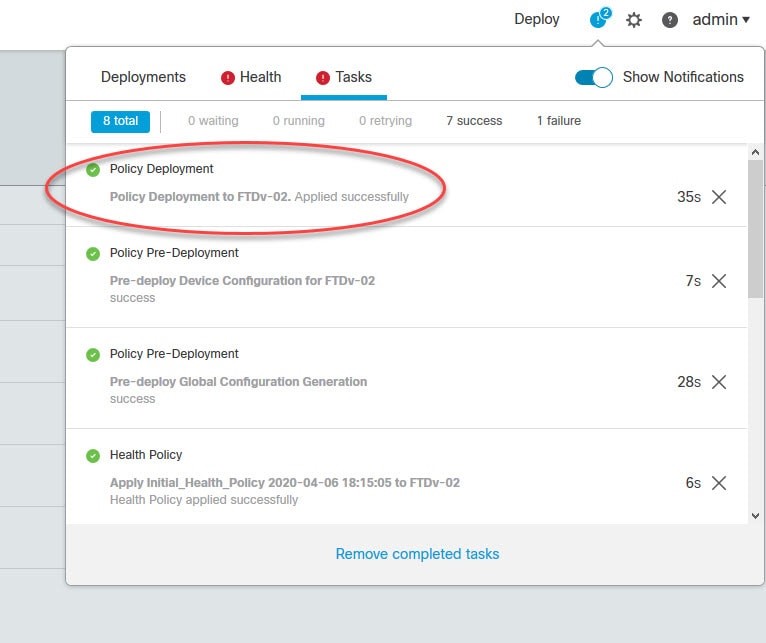
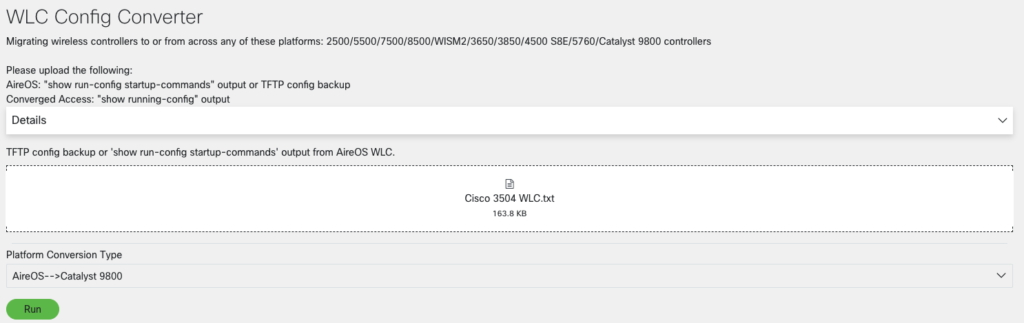
Check Your Cisco Software
Use the Cisco Software Checker to search for Cisco Security Advisories that apply to specific software releases of the following products: Cisco ASA, FMC, FTD, FXOS, IOS, IOS XE, NX-OS and NX-OS in ACI Mode.
To use the tool, select a product, platform (as required) and one or more releases, enter the output of the show version command, or upload a text file that lists specific releases. Then narrow the check to certain advisories, if desired.
The availability of security fixes after the End of Sale is defined in the product’s End-of-Sale announcement, as explained in the Cisco End-of-Life Policy. Additional information about Cisco software updates, vulnerability rating and scoring is available in the Cisco Security Vulnerability Policy.
This tool does not provide information about Cisco IOS XR Software or interim software builds. Also note that for Cisco ASA, FMC, FTD and FXOS Software, the tool only contains vulnerability information for Cisco Security Advisories first published from January 2022 onward, and for NX-OS Software and NX-OS Software in ACI Mode from July 2019 onward.
To find vulnerabilities using the Cisco Software Checker, follow these steps:
Access the Cisco Software Checker:
Visit the Cisco Software Checker web page. You can find this tool on Cisco’s official website or by searching for “Cisco Software Checker” in your preferred search engine.
https://sec.cloudapps.cisco.com/security/center/softwarechecker.x

Provide Software Information:
Enter the details of the Cisco software version you want to check for vulnerabilities. This typically includes the software name, version number, and possibly other relevant information
Select a Method
- Search By Release
- Select a Cisco Operating System (In this tab you can select your device)
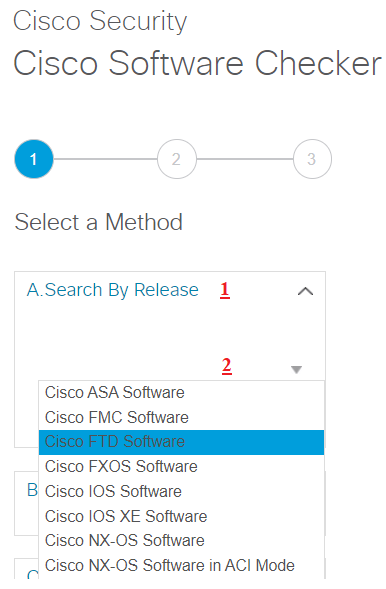
3. Select FTD platform (in this tab you can select your device model)
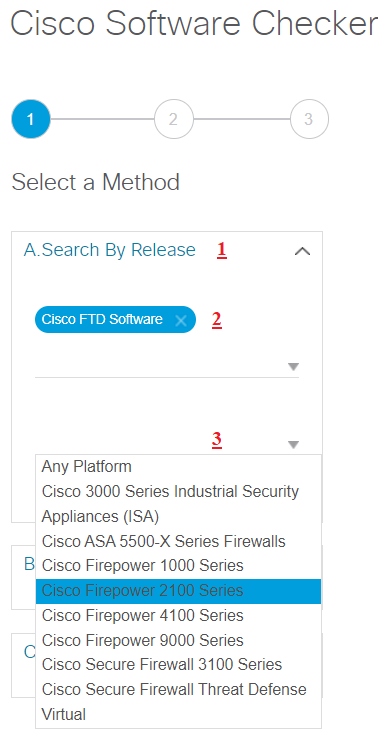
4.Select one or more FTD releases (In this tab you can select current OS version)
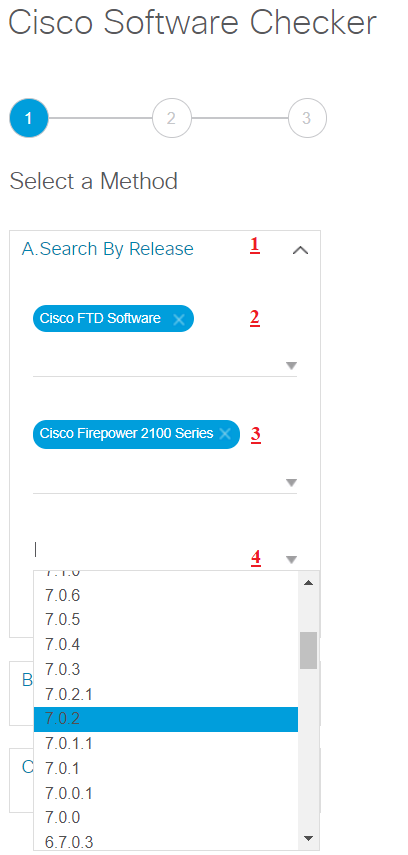
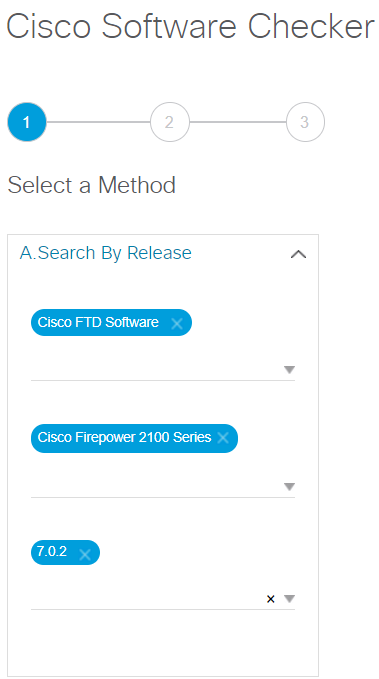
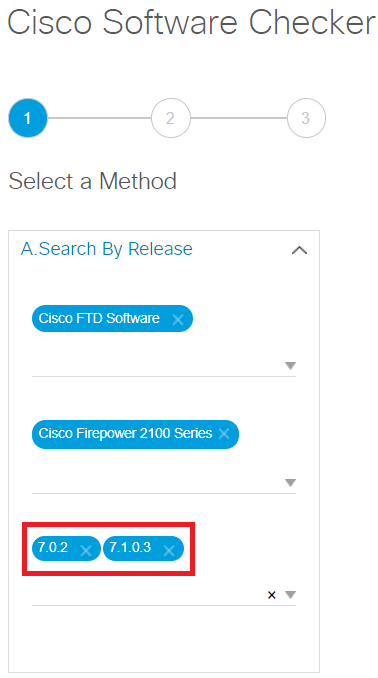
You can select more than one OS version too.
Run the Continue:
Click the ” Continue “button to initiate the vulnerability check. You can check/uncheck Cisco Security impact rating, like All, Critical, High, Medium etc.
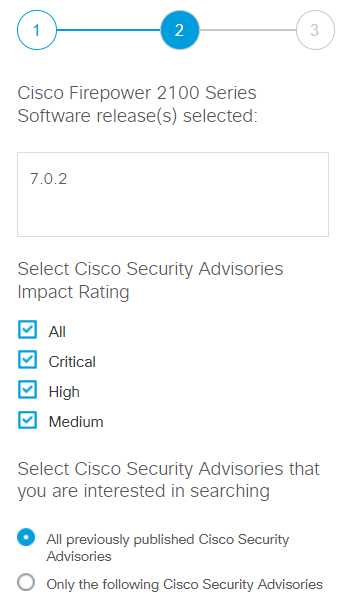
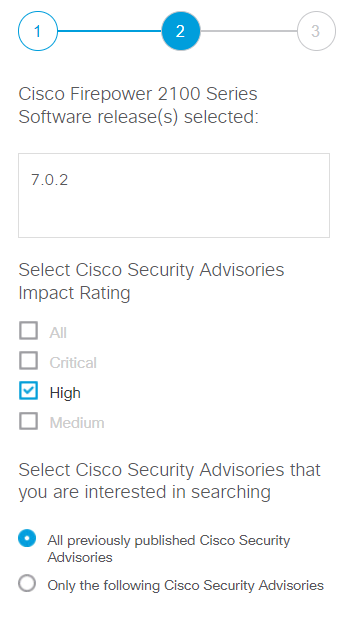
Run the Continue
Click the ” Continue “button to initiate the vulnerability check
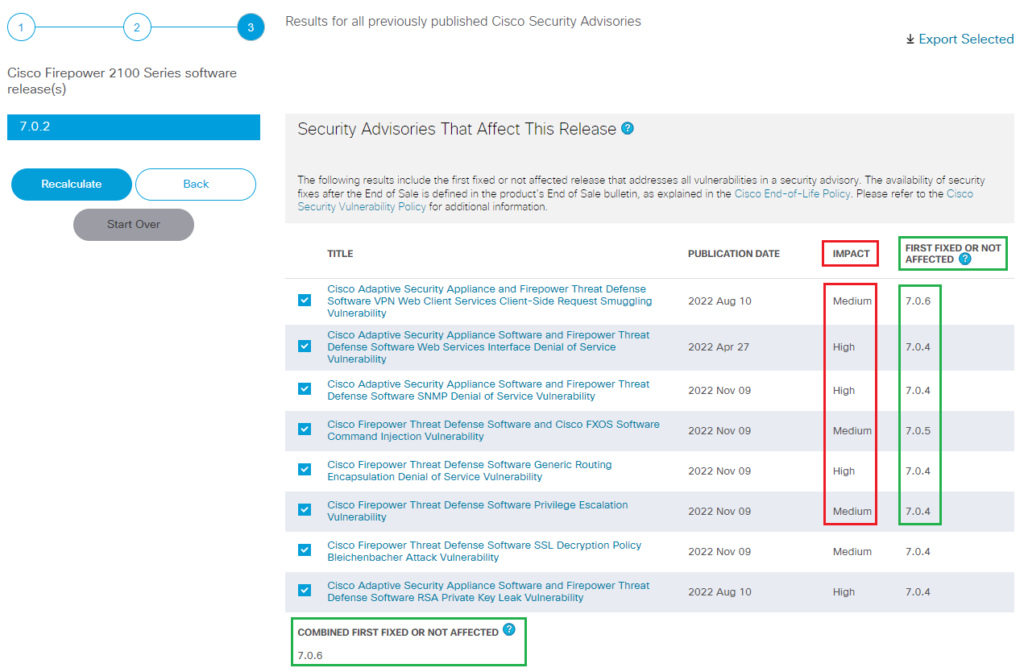
Review the Results:
The tool will generate a report that indicates whether the software version you entered is vulnerable to any known security vulnerabilities. The report may include details about the vulnerabilities, their severity, and potential impact.
In this report, we can see all impacts of Cisco FTD 2100 Series software release 7.0.2 and workaround/fixes as well.
Follow Recommendations:
For any identified vulnerabilities, the tool will provide recommendations on how to address the issues. These recommendations may include upgrading to a patched version, applying workarounds, or implementing other security measures.
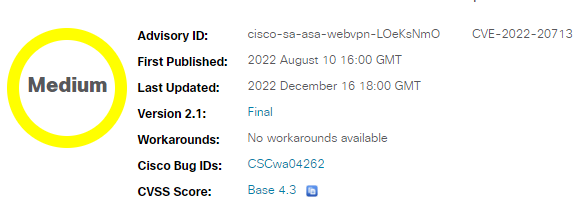
Select any Title and you’ll get more information about that BU
• Summary
• Affected Products
• Vulnerable Products
• Determine the Software Configuration
• Workarounds
• Fixed Software
Additional Information:
The tool may provide links to relevant Cisco Security Advisories or other documentation for further information about the vulnerabilities and how to mitigate them.
Take Action:
Based on the results and recommendations, take appropriate action to address the vulnerabilities. This may involve updating your software to a non-vulnerable version, applying patches, or implementing other security measures.
Remember that the Cisco Software Checker is designed to help you identify vulnerabilities in known software versions based on information provided by Cisco. It’s important to regularly check for updates and follow Cisco’s security advisories to stay informed about the latest vulnerabilities and recommended actions. Additionally, consider implementing a comprehensive security strategy that includes regular patching, network segmentation, intrusion detection, and incident response planning to enhance your overall network security.