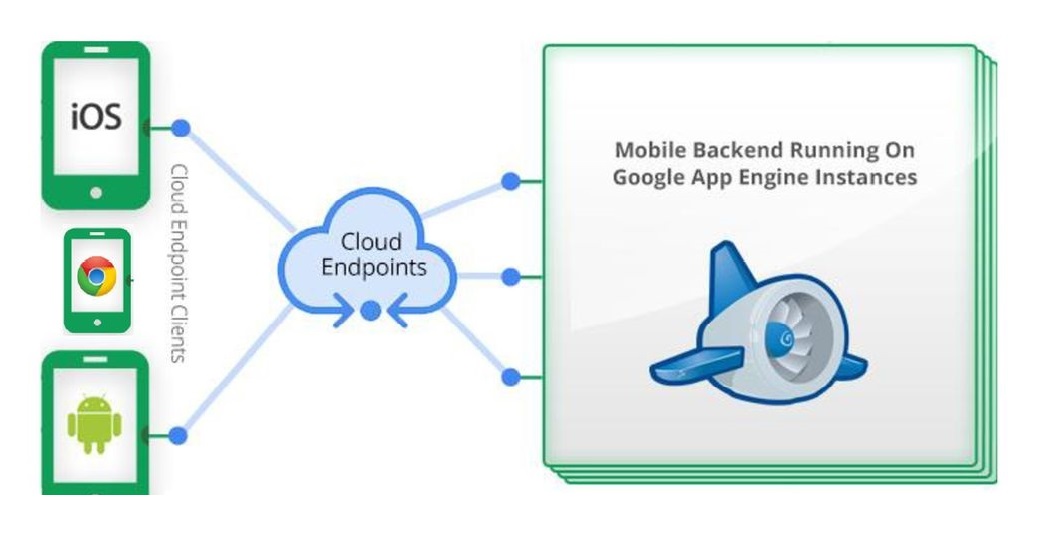
One of the most helpful troubleshooting methods for any IT administrator is figuring out where a host is located on the network. You can do this if you know only its IP address or you have its MAC address already. If you don’t have its MAC address but have access to the machine, you can follow this guide here on how to get the MAC address. It has instructions for Windows 10, MAC, Linux, and so on.
Once you have the MAC address, you’ll need to have access to the network switch. If your network is all connected together via a trunk link, all that you need access to it just one switch, either through telnet, ssh, or console and you can remotely connect to the other neighboring switches via its management IP address (provided everything is configured with management IP and proper setting is in place).
Once you have the MAC address and have access a network switch, you can use the “show mac address-table address” command to try to track down the switch port the host is connected to.
See below for a demonstration:
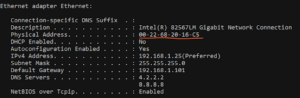
Here I have a Windows 10 machine with a MAC address of 00-22-68-20-16-C5. You can also see that it has an IP address of 192.168.1.25 (sometimes this is needed so that you ping it to see if it responds on the network).
To see the syntax of the “show mac address-table address” on a Cisco catalyst switch, just type as shown below :
cisco-sw-1#show mac address-table address ?
H.H.H 48 bit mac address
You can see that it expects the MAC address in a decimal format in blocks of three. Now see what happens when I type that out :
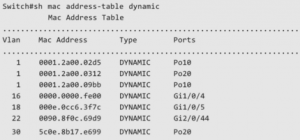
cisco-sw-1#show mac address-table address 0022.6820.16c5
Mac Address Table
—————————————————
Vlan Mac Address Type Ports
—— ———–———– ——–—–
10 0022.6820.16c5 DYNAMIC Gi2/0/48<—- It is going through this port.
Total Mac Addresses for this criterion : 1
There you can see that it shows the MAC address is going through port Gi2/0/48 on switch cisco-sw-1. You can issue “show run int gi2/0/48” to check that port’s configuration :
cisco-sw-1#show run int gig2/0/48
Building configuration…
Current configuration : 133 bytes
!
interface GigabitEthernet2/0/48
switchport trunk encapsulation dot1q
switchport trunk native vlan 10
cswitchport mode trunk
end
We know from the above output (and from the show mac output) that this is a trunk port and usually a higher numbered port is connected to another neighboring switch. You can also verify this by issuing “show cdp neigh” :
cisco-sw-1#show cdp neigh
Capability Codes: R – Router, T – Trans Bridge, B – Source Route Bridge
S – Switch, H – Host, I – IGMP, r – Repeater, P – Phone,
D – Remote, C – CVTA, M – Two-port Mac Relay
Device ID Local Intrfce Holdtme Capability Platform Port ID
cisco-sw-2 Gig 2/0/48 174 T S WS-C3524- Fas 0/24
You can see that there is another switch connected to it and the port that it uses. Again, the host that we’re tracking has a MAC address of 0022.6820.16c5 and IP address of 192.168.1.25 and it is seen through our neighbor switch. We need to ssh or telnet to it to repeat the steps above to try to track the port it is connected to.
I am going to log into that switch but if you don’t know the management IP of that switch, you can issue “show cdp neigh detail” and it will show you its assigned management IP, see below :
cisco-sw-1#show cdp neigh detail
—————————————————
Device ID: cisco-sw-2
Entry address(es) :
IP address: 192.168.1.101
Platform: cisco WS-C3524-XL, Capabilities: Trans-Bridge Switch
Interface: GigabitEthernet2/0/48, Port ID (outgoing port): FastEthernet0/24
Holdtime : 154 sec
Version :
Cisco Internetwork Operating System Software
IOS ™ C3500XL Software (C3500XL-C3H2S-M), Version 12.0(5)WC3b, RELEASE SOFTWARE (fc1)
Copyright (c) 1986-2002 by cisco Systems, Inc.
Compiled Fri 15-Feb-02 10:51 by antonino
advertisement version: 2
Protocol Hello: OUI=0x00000C, Protocol ID=0x0112; payload len=27, value=00000000FFFFFFFF010121FF000000000000003094BBEA40FF000A
VTP Management Domain: ‘ccie’
Native VLAN: 10
Duplex: full
cisco-sw-1#
There you can see that the management IP is 192.168.1.101. You can get the other switch’s detailed information such as model number and version it is running..etc. I have a really old switch in my lab.
Now let’s access that switch and see try to track down that host :
cisco-sw-1#telnet 192.168.1.101
Trying 192.168.1.101 … Open
User Access Verification
Username: paula
Password :
cisco-sw-2>en
Password :
cisco-sw-2#show mac address 0022.6820.16c5
Non-static Address Table :
Destination Address Address Type VLAN Destination Port
——————— ————— ——————–——
Now you see that the host is connected to port Fast0/11. You can also issue show run int fast0/11 to verify that it is an access port (typically used for end user’s device)
cisco-sw-2#show run int fast0/11
Building configuration…
Current configuration :
!
interface FastEthernet0/11
switchport access vlan 10
End
You can see that it is connected to VLAN 10, which may be useful for other purposes.
What happens if when you run the show mac-address-table address command and it doesn’t return anything at all? It might be because the device has been idle for sometime and it is not being alive on the network anymore. Most switches have a MAC aging timer with 5 minutes and after that, it clears the CAM table (or MAC address table). This is because the switch has only so much memory and it can’t hold all the MAC addresses it has learned in its table forever. It needs to clear that and make room for newer MAC addresses as they are active and the cycle repeats.
You then have to generate some activity by pinging its IP address and then you can start issuing the show mac address command. Continue to repeat this process on all neighboring switches (if needed) until you can identify the switch that has the host connected to it.
Here is another trick. If you want to know the IP address of that MAC address, you can issue a show arp and it will tell you the IP address.
cisco-sw-1#show arp | inc 0022.6820.16c5
Internet 192.168.1.25 0 0022.6820.16c5 ARPA Vlan 10
The above steps should also work for different vendors as well and they may have different syntax. Just check out the correct syntax if needed.
If you need help with any of the above or with troubleshooting in general, please feel free to reach out to us at sales@accendnetworks.com for a free consultation and we’ll be glad to assist you.