Mastering Data Protection: AWS Backup.

In the ever-evolving digital landscape, where data is the lifeblood of businesses and organizations, the concept of data backup has become paramount. In essence, a backup is a secure and duplicate copy of your critical data and information. ensuring that in the face of unexpected calamities, or data corruption, your valuable information remains intact and recoverable. A well-implemented backup strategy is akin to a safety net for your digital assets, providing you with the assurance that, even in the worst-case scenarios, your data can be resurrected, and business operations can continue with minimal disruption.
What is AWS Backup Service and Why It Matters?
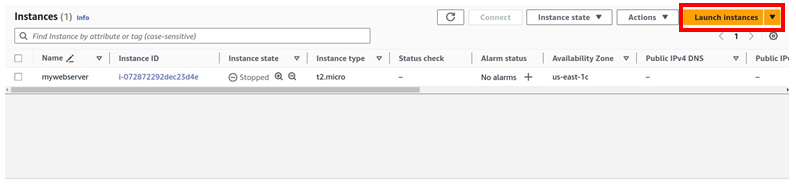
AWS Backup is a fully managed service offered by Amazon Web Services (AWS). It makes it easy to centralize and automate data protection across AWS services. AWS Backup is designed to simplify the backup process, making it easier to create, manage, and restore backups for critical data.
Key components of AWS backup service.
Backup’s
A backup or recovery point represents the content of a resource, such as an Amazon Elastic Block Store (Amazon EBS) volume at a specified time. It is a term that refers generally to the different backups in AWS services, such as Amazon EBS snapshots and DynamoDB backups.
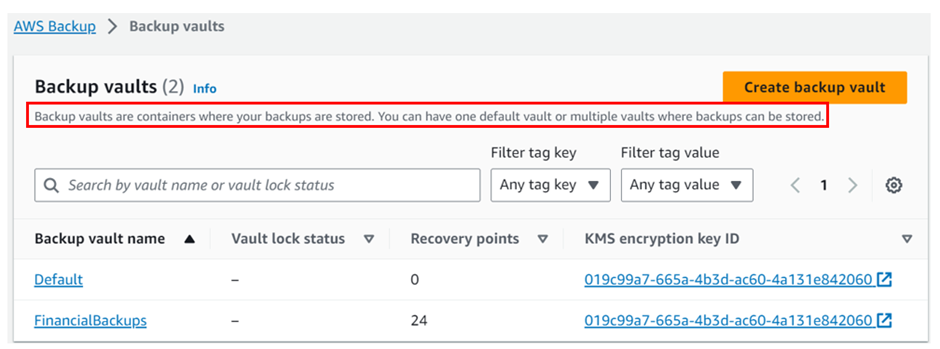
Backup vaults
Vaults are simply logical containers that help you organize and manage your backups effectively. You can create multiple vaults to categorize and store backups based on your requirements.
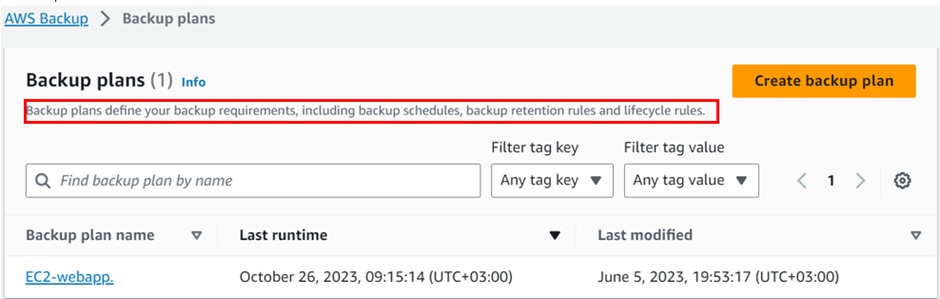
Backup plan
These are at the heart of AWS Backup and define your backup policies and schedules. Within a backup plan, you specify settings such as backup frequency, retention periods, and lifecycle rules.
Lifecycle Rules:
Lifecycle rules determine the retention period of your backups and when they should be deleted. You can configure rules to automatically transition backups to cold storage or remove them when they’re no longer needed.
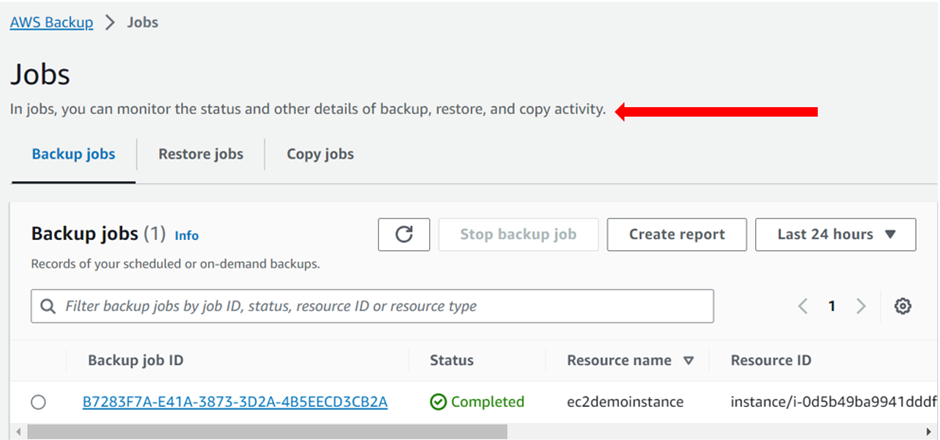
Backup Jobs:
Once the backup is scheduled, the backup details can be monitored status and other details like backup, restore, and copy activity. Backup job statuses include pending, running, aborted, completed, and failed.
Recovery Points:
These are specific states of your resources captured by backup jobs at particular points in time. AWS Backup retains multiple recovery points based on the retention settings in your backup plan.
Vault Lock:
Vault lock provides an additional layer of security for your backups. When enabled, it prevents the deletion of backup data for a specified retention period, ensuring data integrity and compliance with retention policies.
the importance of AWS backup in today’s data-driven world.
Data resilience.
Data loss can be catastrophic for any organization. AWS Backup ensures that your critical data is protected and can be quickly recovered in case of accidental deletions, hardware failures, or data corruption.
Security and Compliance
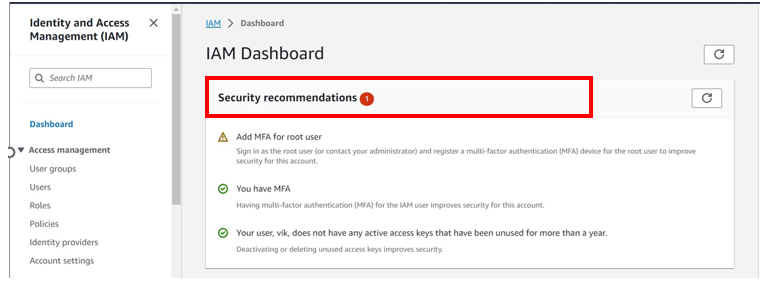
AWS Backup integrates with AWS Identity and Access Management (IAM) and AWS Key Management Service (KMS) to provide secure, encrypted backups. This is crucial for meeting regulatory requirements and maintaining data privacy.
Simplicity and Automation
AWS Backup simplifies the backup process with automated policies, making it easy to create, schedule, and manage backups without the need for complex scripting or manual interventions.
Centralized Management
With AWS Backup, you can manage backups for multiple AWS services from a single console, streamlining backup operations and reducing management overhead.
Cross-Region and Cross-Account Backups
AWS Backup enables you to create backups that span regions and AWS accounts, enhancing data resilience and disaster recovery capabilities.
Cross-Account and Cross-Regional Backups
Cross-account and cross-regional backups form the cornerstone of a resilient data protection strategy. Cross-account backups involve replicating critical data from one AWS account to another, mitigating the risk of accidental data loss, and enhancing security by adhering to the principle of least privilege.
Cross-regional backups extend this protection by replicating data across different AWS regions, guarding against region-specific outages or unforeseen disruptions.
If you have any questions concerning this article or have an AWS project that require our assistance, please reach out to us by leaving a comment below or email us at sales@accendnetworks.com!
Thank you!