1. How you can make it healthier and safe
2. How to make it efficient
3. If we do PKI then what best practice should we move on with
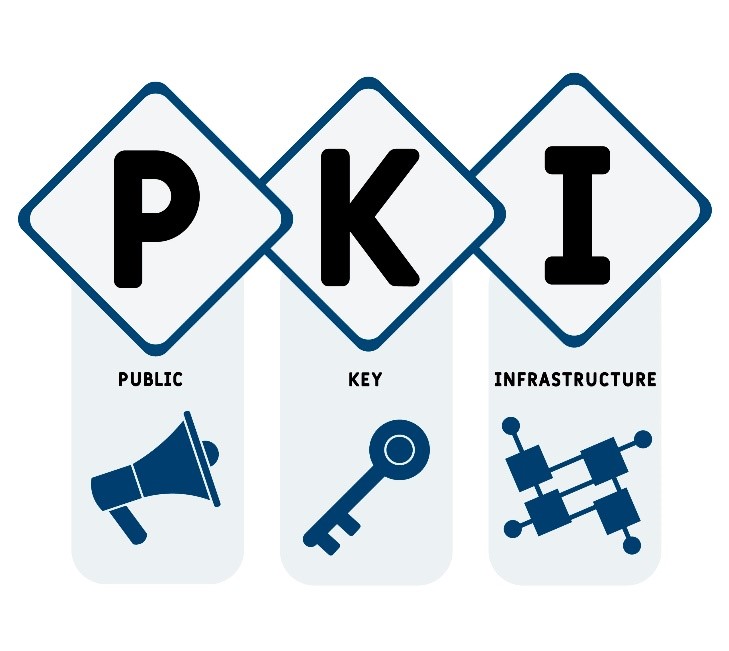
PKI (public key infrastructure) is the underlying framework that enables entities -- users and servers -- to securely exchange information using digital certificates. The entities that facilitate and use PKI typically involve general internet users, web clients or browsers, and company servers -- though this can extend to other virtual machines (VMs) as well.
The word infrastructure describes PKIs since it does not refer to one single physical entity. Instead, it refers to the components used to encrypt data and authenticate digital certificates. These components include the hardware, software, policies, procedures, and entities needed to safely distribute, verify and revoke certificates.
Public key infrastructure (PKI) is the well-established protocol for organizations that need to secure distributed points of communication, such as browsers and IoT and mobile devices. For device manufacturers and application developers, revenue security depends on creating a highly secure ecosystem that ensures regulatory compliance and consumer trust.
The security needs of networks and the infrastructure protecting them change over time in response to new threats and advances in technology. With tens of billions of IoT devices already in operation, the potential attack vectors for hackers to steal data or infiltrate systems are great and growing exponentially. PKI is a vital element of IoT network security, provisioning unique device identities, bolstering authentication protocols, and enabling trusted communication channels between servers and devices. However, not all implementations follow PKI security best practices, resulting in flawed and vulnerable systems.
in technical terms, PKI is a two-key asymmetric cryptosystem that supports various information technology (IT) systems in their pursuit of high-level information confidentiality, encryption and confidence. The two keys, in this case, are also the two main pieces that facilitate this secure data management: a public key and a private key.
To put PKI in the best practice possible as well efficiently I would like to use the 7-Step Method in order.
To ensure a secure and smooth PKI setup, start by following some simple best practices. Plan Our implementation carefully from the beginning because making changes later can be difficult and costly. Understand your PKI needs well, both now and for the future. By doing this, we will avoid potential security risks and save time and resources, making your PKI experience much easier.
Define key and certificate security policies and protocols that address every stage of their lifecycle. Establishing a PKI may seem straightforward from the outset, but when one considers the millions of certificates that will possibly be issued, their expirations, and the security issues that would require revocation, it can quickly become very complicated. This becomes a potential security flaw, as the more complex a PKI is, the more difficult it is to track identities and revoke certificates that could be used to breach a system.
An important PKI design best practice is to plan for the entire lifecycle of certificates. By fully mapping the policies regarding the issuing, updating, monitoring, expiry, revocation, and decommissioning of certificates, all future managers of the PKI will have a clear outline of what should happen with certificates at all stages of their existence.
The cryptographic keys that are used in the PKI are the most vulnerable point of a PKI deployment and must always be protected. Hackers can use a variety of techniques to analyze and detect keys while they are in use or transit. Once in control of these keys, they can decrypt private data or pose as authenticated users to access systems. Within this context another PKI security best practice is to always use hardware security modules (HSMs), where possible, to store keys and perform cryptographic operations.
If you need to provision older devices without a secure update mechanism, which are already in the field, make sure to use white-box cryptography so that keys are not exposed in the clear during the provisioning process.
Throughout a PKI deployment, regular checks should be performed to ensure that the Certificate Policy and Certificate Practice Statements (CP/CPS) are being implemented and adhered to. Even for internal deployments, it is still a PKI design best practice to create audit trails that can be easily accessed and monitored. This ensures compliance with security policies and with the desired assurance level of the organization.
The root CA is the master key that underpins the entire PKI. If it is compromised, every certificate issued is invalid and would have to be revoked and reissued. PKI deployment best practices dictate that the root CA remains strictly protected and is never published online. The initiation of a PKI should begin with a root signing ceremony, where the policies surrounding the root are established. These policies should cover the root’s chain of custody, where the root is stored, and how it’s scripted.
Unfortunately, attacks on PKIs are not just an external issue. The private keys and other data surrounding your PKI can be extremely valuable. For that and other reasons, threats can also come from employees. There are a number of PKI deployment best practices that can be implemented to mitigate internal threats. These include using secured rooms for key and root programming that require two or more security IDs to access, and using a distributed security model that ensures there is no single point of responsibility that can be compromised.
Issuing certificates and provisioning keys and identities as PKI security best practices are still only one step in running a secure PKI. The ongoing integrity must be maintained. This includes a process for revoking keys and certificates that can no longer be trusted. Certificate authorities should maintain a certificate revocation list, which contains all suspended security certificates. Communications with a device or application using a revoked certificate should be blocked. For example, an IoT device using a certificate that is no longer authorized will not be able to gain access to a server.
Creating a highly secure and trusted ecosystem for your organization’s devices or applications depends on a successful and ongoing PKI deployment that follows PKI implementation best practices. While it’s possible to develop and manage a PKI internally, it requires resources and expertise outside of many organizations’ capabilities and may not scale smoothly as production grows.
Intertrust PKI is a managed PKI for IoT service that is trusted across the world and already secures the identities of billions of devices. Our scalable and flexible identity provisioning and PKI management is built on PKI design best practices and utilizes industry-leading security technologies, including white-box cryptography, to ensure that your networks and organizations are secured against risks arising from distributed communication points.